[Pass Ensure VCE Dumps] Wrote 70-680 Exam With PassLeader New 580q 70-680 Practice Test and PDF Study Guide (201-230)
100% Valid 70-680 Exam Pass Tips: PassLeader's 580q 70-680 exam dumps were updated in recent days with new 70-680 exam questions added, PassLeader ensure the latest 70-680 VCE dumps or PDF dumps are the newest and the most valid, our 70-680 practice tests will help you 100 percent pass 70-680 exam. Visit passleader.com and get the 70-680 exam questions with PDF and VCE. New version VCE player is also free now. keywords: 70-680 exam,580q 70-680 exam dumps,580q 70-680 exam questions,70-680 pdf dumps,70-680 vce dumps,70-680 braindumps,70-680 practice tests,70-680 study guide,TS: Windows 7, Configuring Exam 
QUESTION 201
A user reports that he is unable to start his computer. He provides the following information:
- The boot partition is encrypted by using BitLocker Drive Encryption (BitLocker).
- The user cannot locate his BitLocker recovery key.
You need to start Windows 7 on the computer. The solution must use the minimum amount of administrative effort. What should you do? A. From the BIOS, disable the Trusted Platform Module (TPM).
B. Start the computer from the Windows 7 installation media and select Repair your computer.
C. Start the computer from the Windows 7 installation media, press SHIFT + F10, and then run chkdsk.
D. Start the computer from the Windows 7 installation media and select Install now. Answer: D
Explanation:
No recovery key = no recovery. Time to install. Any other option defeats the whole point of encrypting it. Encrypted volumes are locked when the encryption key is not available. When the operating system volume is locked, you can boot only to recovery mode. In recovery mode, you can enter the BitLocker password or you can attach the USB device that has the recovery key stored and restart the computer. Once you enter the recovery password or key, you can boot your computer normally. The following events trigger recovery mode:
* The boot environment changes. This could include one of the boot files being modified.
* TPM is disabled or cleared.
* An attempt is made to boot without the TPM, PIN, or USB key being provided.
* You attach a BitLocker-encrypted operating system volume to another computer. QUESTION 202
Your company network includes portables computers that have Windows 7 Ultimate and Windows 7 Professional installed. You want to standardize all portable computers to Windows 7 Professional for Key Management Server (KMS) licensing purpose. You need to install Windows 7 Professional on all Windows 7 Ultimate portable computers What should you do? A. Launch Windows Update.
B. Perform a clean installation over the existing system partition.
C. Perform a clean installation on a non-system partition.
D. Supply the Windows 7 Professional KMS Key.
E. Launch Windows Anytime Upgrade. Answer: B QUESTION 203
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series. A company has a new deployment of Windows Deployment Services (WDS), the Microsoft Deployment Toolkit (MDT), and the Windows Automated Installation Kit (WAIK). You need to capture an image of a Windows 7 reference computer. Which two actions should you perform on the server before performing actions on the reference computer? (Each correct answer presents a complete solution. Choose two.) A. Run the Dism command with the /Mount-Wim option.
B. Create a capture image in WDS.
C. Run the BCDEdit command.
D. Run the Dism command with the /Add-Driver option.
E. Run the ImageX command with the /mount parameter.
F. Use Sysprep with an answer file and set the UpdateInstalledDrivers option in the answer file to No.
G. Add a boot image in WDS.
H. Run the Start /w ocsetup command.
I. Run the PEImg /prep command.
J. Run the Diskpart command and the attach command option.
K. Use Sysprep with an answer file and set the UpdateInstalledDrivers option in the answer file to Yes.
L. Use Sysprep with an answer file and set the PersistAllDeviceInstalls option in the answer file to True.
M. Run the Dism command with the /Add-Package option.
N. Use Sysprep with an answer file and set the PersistAllDeviceInstalls option in the answer file to False. Answer: BG
Explanation:
http://technet.microsoft.com/en-us/library/cc766320(v=ws.10).aspx
MDT relies on boot images created in WDS, WAIK is a collection of tools that you use to help automate deployment. To capture an image created on a reference computer you need to add a boot.wim files to WDS, then using the boot.wim, create a capture wim file (usually called capture.wim). This allows you to capture a a reference computer. QUESTION 204
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series.
A company has client computers that run Windows 7 Enterprise. Users complain that Windows displays too many notifications when they try to install software or make changes to their computer. You need to decrease the number of notifications that Windows displays when users try to install software or make changes to their computer. Which two choices should you use to achieve this goal? (Each correct answer presents a complete solution. Choose two.) A. Local Users and Groups
B. The Services Management console
C. The Netsh command
D. The Group Policy Management console
E. Share Permissions
F. The Folder Properties window
G. Device Manager
H. The Icacls command
I. The User Account Control Settings Control Panel window Answer: DI QUESTION 205
Your corporate network contains a Remote Desktop Gateway (RD Gateway) server named Server1 and a Remote Desktop Session Host (RD Session Host) server named Server2. You have a computer named Computer1 that runs Windows 7. You use Computer1 from home. You need to access Server2 from Computer1. What should you do? A. Run Mstsc.exe /admin /v:server2:443.
B. Run Mstsc.exe /console /v:server2:8080.
C. Create a Remote Desktop Connection and modify the Connect from anywhere settings.
D. Create a Remote Desktop Connection and modify the Server authentication settings. Answer: C
Explanation:
To connect using an RD Gateway server, navigate to the Advanced tab of the Remote Desktop Connection Properties dialog box and click Settings under Connect From Anywhere. This opens the RD Gateway Server Settings dialog box. This dialog box allows you to specify RD Gateway settings, including whether or not you want the RD Gateway to be detected automatically, whether to use a specific RD Gateway server, as shown in the firgure, or you can specify Do Not Use an RD Gateway Server, which is the default setting. QUESTION 206
A company has client computers that run Windows 7. You set up a virtual private network (VPN) infrastructure that encapsulates Point-to-Point Protocol (PPP) traffic over the Secure Sockets Layer (SSL) channel of the HTTPS protocol. You need to create the VPN connection on the company's client computers. Which type of VPN should you use? (To answer, select the appropriate setting or settings in the work area.)
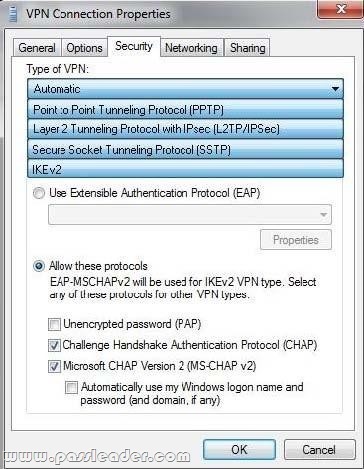 Answer:
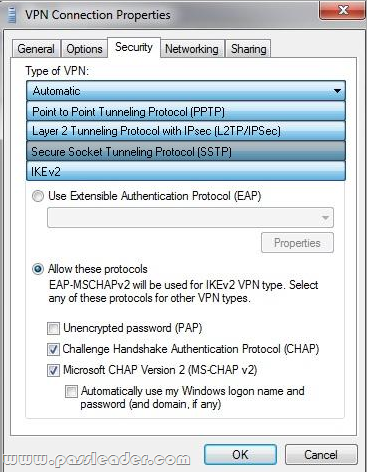 QUESTION 207
You have a computer that runs Windows 7. You need to connect to a network projector from the computer. What should you do? A. Run Displayswitch.exe and select Projector only.
B. Run Netproj.exe and provide the path to the projector.
C. From Device Manager, click Add legacy hardware.
D. From Network and Sharing Center, create an ad hoc network and run Displayswitch.exe. Answer: B QUESTION 208
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series.
Your company office network includes a file server that has Windows Server 2008 R2 installed and client computers that have Windows 7 Enterprise installed. The computers are members of an Active Directory domain. The file server has the BranchCache feature installed. The client computers have a third-party firewall application installed. You configure BranchCache on all computers to run in Distributed Cache mode. You need to ensure that the client computers can access all cached files. What should you do? A. Configure firewall exception rules for multicast traffic, inbound and outbound traffic for local UDP port 3702, and inbound and outbound traffic for local TCP port 80.
B. Check permissions.
C. Configure firewall exception rules for inbound and outbound traffic for local TCP port 80 and for inbound and outbound traffic for local TCP port 8443.
D. Create a Group Policy object and enable the Set BranchCache Hosted Cache mode policy.
E. Run the Netsh branchcache set service mode=HOSTEDSERVER clientauthentication=NONE command.
F. Run the Netsh branchcache set service mode=HOSTEDCLIENT command.
G. Run the Netsh branchcache set service mode=DISTRIBUTED command
H. Create a Group policy object and configure the Set percentage of disk space used for client computer cache option.
I. Create a Group policy that sets Hash Publication for Branchcache as disabled. Answer: A
Explanation:
Configuring Windows 7 as a BranchCache client involves enabling BranchCache, selecting either Hosted Cache mode or Distributed Cache mode, and then configuring the client firewall to allow BranchCache traffic. You can configure BranchCache either using Group Policy or by using the Netsh command-line utility. The firewall rules that you configure depend on whether you are using Hosted Cache or Distributed Cache mode. You can use predefined firewall rules or manually create them based on protocol and port. The required firewall rules are as follows: The BranchCache - Content Retrieval (Uses HTTP) predefined rule. If this rule is not available, create rules that allow inbound and outbound traffic on TCP port 80. This rule is required for both Hosted Cache and Distributed Cache mode. You can create this rule using Windows Firewall With Advanced Security. The BranchCache - Peer-Discovery (Uses WSD) predefined rule. If this rule is not available, create rules that allow inbound and outbound traffic on UDP port 3702. This rule is only required when using Distributed Cache mode. The BranchCache - Hosted Cache Client (HTTPS-Out) predefined rule. It this rule is not available, configure a rule that allows outbound traffic on TCP port 443. This rule is required only when using Hosted Cache mode. You need to configure the firewall rules only when you configure BranchCache using Group Policy. When you configure BranchCache using Netsh, the appropriate firewall rules are set up automatically. QUESTION 209
A computer that runs Windows XP has one basic disk containing a single partition. The partition has 30 GB of free space. The hard disk has 5 GB of unallocated space. You need to install Windows 7 in a dual-boot configuration. Windows 7 must not be installed in a virtual hard disk (VHD). What should you do first? A. Compress the hard drive.
B. Extend the primary partition.
C. Share the hard drive.
D. Shrink the primary partition. Answer: D QUESTION 210
You administer a desktop computer that has the following hardware specifications:
- Dual-core 2.5 GHz processor
- 1 GB RAM
- 25 GB unpartitioned disk space
- Onboard graphics that has WDDM 1.0
You install a customized Windows 7 Enterprise 64-bit image on the computer by using unpartitioned disk space. The computer operates unacceptably slow. You need to improve the performance of the computer. What should you do? A. Install another 1 GB of RAM.
B. Open Task Manager. Set the priority of all SYSTEM processes to High.
C. Install a video card that has 128 MB of video RAM.
D. Perform the initial Windows Experience Index run. Answer: A
Explanation:
http://windows.microsoft.com/en-us/windows7/products/system-requirements
Should have 2GB RAM as a minimum.

http://www.passleader.com/70-680.html QUESTION 211
You plan to deploy Windows 7 images. You need ensure that you can deploy images by using the Windows Preinstallation Environment (Windows PE). What should you add to the Windows PE image? A. Imagex.exe
B. Loadstate.exe
C. Mighost.exe
D. Usmtutils.exe Answer: A
Explanation:
Creating an Image for Rapid Deployment. The most common scenario for ImageX is capturing and applying an image from a network location for rapid deployment. This scenario requires booting your technician computer into Windows PE, capturing the image with ImageX, putting the image on a network share, and then applying the image to the destination computers.ImagexImageX is a command-line tool that enables original equipment manufacturers (OEMs) and corporations to capture, to modify, and to apply file-based disk images for rapid deployment. ImageX works with Windows image (.wim) files for copying to a network, or it can work with other technologies that use .wim images, such as Windows Setup, Windows Deployment Services (Windows DS), and the System Management Server (SMS) Operating System Feature Deployment Pack. QUESTION 212
You use a desktop computer that has Windows 7 SP1 Ultimate installed. You update the driver for the computer's sound card and the computer becomes unresponsive. You need to be able to roll back the sound card driver. What should you do? A. Boot the computer from a Windows Recovery Environment (Windows RE) disk, and then restore the system image.
B. Start the computer, press F8, and then select: Repair Your Computer.
C. Start the computer, press F8, and then select: Debugging Mode.
D. Restart the computer in safe mode. Answer: D QUESTION 213
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series. A company has a server running Windows Server 2008 R2, with Windows Deployment Services (WDS), the Microsoft Deployment Toolkit (MDT), and the Windows Automated Installation Kit (WAIK) set up. The company also has client computers running Windows 7 Enterprise. You need to remove some files from a virtual hard disk on a client computer. What should you do first? A. Use Sysprep with an answer file and set the PersistAllDeviceinstalls option in the answer file to True.
B. Run the BCDEdit /delete command.
C. Run the Start /w ocsetup command.
D. Use Sysprep with an answer file and set the UpdateinstalledDrivers option in the answer file to Yes.
E. Run the Dism command with the /Add-Driver option.
F. Add a boot image and create a capture image in WDS.
G. Run the PEImg /prep command.
H. Run the ImageX command with the /mount parameter.
I. Run the Dism command with the /Mount-Wim option.
J. Use Sysprep with an answer file and set the UpdateInstalledDrivers option in the answer file to No.
K. Run the Dism command with the /Add-Package option.
L. Run the Diskpart command and the attach command option.
M. Use Sysprep with an answer file and set the PersistAllDeviceInstalls option in the answer file to False. Answer: L
Explanation:
DiskPart.exe and managing Virtual Hard Disks (VHDs) in Windows 7 In Windows 7, new commands have been added in DiskPart to allow for the creation and management of Virtual Hard Disks (.vhd files). The DiskPart VHD management commands have been provided below in 2 sections ?commonly used commands with examples and other commands. It is assumed in each of the examples that DiskPart.exe has already been launched in an elevated command prompt.
Creating a VHD
The example below creates a 20GB dynamically expanding VHD called "test.vhd" and places it in the root of the C: drive. Note that the type parameter is optional and the default type is fixed. create vdisk file=c:test.vhd maximum=20000 type=expandable Attaching a VHD
The following example shows how to select and attach the VHD. It also provides steps for partitioning, formatting and assigning a drive letter to the attached VHD.
select vdisk file=c:test.vhd
attach vdisk
create partition primary
format fs=ntfs label="Test VHD" quick
assign letter=v
Detaching the VHD
To detach (i.e. unmount) the VHD, use the following example:
select vdisk file=c:test.vhd
detach vdisk QUESTION 214
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. An Answer choice may be correct for more than one QUESTION in the series.
A company has a server running Windows Server 2008 R2, with Windows Deployment Services (WDS), the Microsoft Deployment Toolkit (MDT), and the Windows Automated Installation Kit (WAIK) set up. The company also has client computers running Windows 7 Enterprise. You need to capture an image of a client computer. What should you do on the server before performing actions on the client computer? A. Use Sysprep with an answer file and set the UpdatelnstalledDrivers option in the answer file to No.
B. Run the Diskpart command and the attach command option.
C. Use Sysprep with an answer file and set the PersistAllDevicelnstalls option in the answer file to False.
D. Use Sysprep with an answer file and set the UpdatelnstalledDrivers option in the answer file to Yes.
E. Add a boot image and create a capture image in WDS.
F. Run the BCDEdit /delete command.
G. Run the Dism command with the /Add-Driver option.
H. Run the ImageX command with the /mount parameter.
I. Run the Dism command with the /Add-Package option.
J. Use Sysprep with an answer file and set the PersistAllDevicelnstalls option in the answer file to True.
K. Run the Start /w ocsetup command.
L. Run the Dism command with the /Mount-Wim option.
M. Run the PEImg /prep command. Answer: E QUESTION 215
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series.
A company has a server running Windows Server2008 R2 with Windows Deployment Services (WDS), the Microsoft Deployment Toolkit (MDT), and the Windows Automated Installation Kit (WAIK) set up. The company also has client computers running Windows 7 Enterprise. A new driver is released for the network cards that are installed in the client computers. You need to update the image with the new driver for the network cards. What should you do to add the driver to the mounted Windows image file? A. Run the Start /w ocsetup command.
B. Run the Diskpart command and the attach command option.
C. Use Sysprep with an answer file and set the PersistAllDeviceInstalls option in the answer file to True.
D. Use Sysprep with an answer file and set the PersistAllDeviceInstalls option in the answer file to False.
E. Use Sysprep with an answer file and set the UpdateInstalledDrivers option in the answer file to Yes.
F. Run the Dism command with the /Mount-Wim option.
G. Use Sysprep with an answer file and set the UpdateInstalledDrivers option in the answer file to No.
H. Run the PEImg /prep command.
I. Run the ImageX command with the /mount parameter.
J. Add a boot image and create a capture image in WDS.
K. Run the Dism command with the /Add-Driver option.
L. Run the BCDEdit /delete command.
M. Run the Dism command with the /Add-Package option. Answer: K QUESTION 216
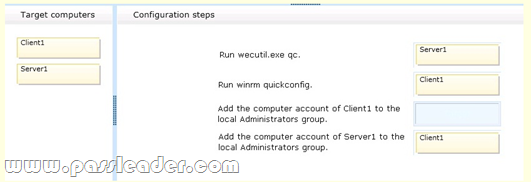
Your company network includes a Windows Server 2008 R2 server named Served. You use a client computer named Client1 that has Windows 7 Enterprise installed. Both computers are members of an Active Directory domain. You want to automatically forward events from Client1 to Server1. You need to configure the required source-initiated subscription. What should you do? (To answer, drag the appropriate configuration step or configuration steps to the correct target computer or target computers in the answer area. An answer choice can be used once, more than once, or not at all.)
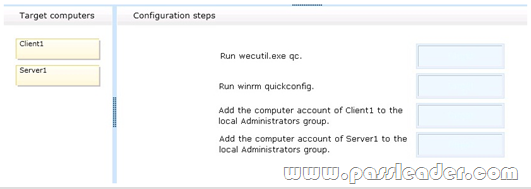 Answer:
 QUESTION 217
You have a computer that runs Windows 7. You need to identify the disk, memory, CPU, and network resources that an application is currently using. Which tool should you use? A. Component Services
B. Performance Information and Tools
C. Reliability Monitor
D. Resource Monitor Answer: D QUESTION 218
You need to identify the hardware failures have occurred on your computer in the past six months. What should you do? A. From the Control Panel, open Performance Information and Tools.
B. From the Control Panel, open Troubleshooting.
C. From the Action Center, under Maintenance, click View reliability history.
D. From the Action Center, open Recovery. Answer: C QUESTION 219
Your company network includes a Windows Server 2008 R2 server named Server1 and client computers that have Windows 7 installed. All computers are members of an Active Directory domain. You use a computer named Client1. You plan to collect events from Client1 on Server1 by using HTTPS. On Server1, you start and configure the Windows Event Collector service. On Client1, you start the Windows Remote Management service. You discover that no events are being collected. You need to ensure that events are forwarded from Client1 to Server1. What should you do? A. On Client1, create an inbound Rule to allow port 5986 for the Public connection type.
B. On Server1, create a Windows Event Collector firewall exception for the Domain connection type.
C. On Client1, create an outbound Rule to allow port 443 for the Domain connection type.
D. On Client1, create an inbound Rule to allow port 5986 for the Domain connection type. Answer: D QUESTION 220
Your company network includes computers that have Windows 7 Enterprise installed. The computers use IP addresses of DNS and WINS servers assigned statically. The DNS and WINS servers on the company network have been taken offline for upgrades. Users report that they can no longer access the Internet. You need to provide access to the Internet for the computers during the maintenance. What should you do? A. Change the IP address of the primary WINS to a public name server.
B. Change the IP address of the default gateway.
C. Change the IP address of the primary DNS to a public DNS.
D. Change the client IP address and subnet mask. Answer: C

http://www.passleader.com/70-680.html QUESTION 221
You support desktop computers that have Windows 7 Enterprise installed. All computers are configured with system protection on drive C and with a backup task that runs daily at midnight. One of the users reports that in the morning she has installed a new version of a browser. After the installation, a folder that has favorite shortcuts was replaced with new content. You need to restore the most recent version of the folder that contains the user data. What should you do? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
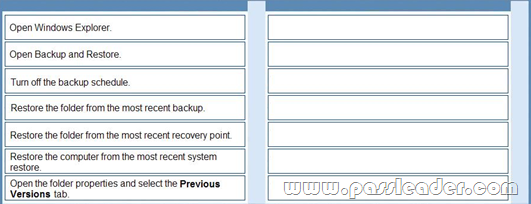 Answer:
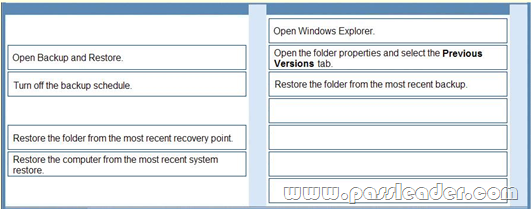 QUESTION 222
You use a computer that has Windows 7 SP1 installed and has a folder named C:Data. The active network connection for the computer is configured as Public. You assign User1 to a local group called DataUsers. The group has been granted Read NTFS permissions for the folder. User1 browses to the shared folder across the network and receives the following error message:
"Access is Denied."
You need to ensure that the user can download files from the shared folder. What should you do? A. Allow file and printer sharing through Windows Firewall.
B. Change the network location of the computer from a Public network to a Home or Work network.
C. From the Security settings of the C:Data folder, assign the Full Control NTFS permissions to User1.
D. From the Advanced Sharing settings of the folder, assign the Read share permission to User1.
E. From the Advanced Sharing permissions, enable caching. Answer: D QUESTION 223
You have a public computer that runs Windows 7. On the computer, you create two user accounts named Admin1 and User1. Admin1 is a member of the Administrators group and User1 is a member of the Users group. You need to configure the computer to meet the following requirements:
- Allow Admin1 full access to Control Panel.
- Prevent User1 from accessing Control Panel.
What should you do? A. Create a new local Group Policy object (GPO) linked to the Admin1 account. From User Configuration set Prohibit Access to Control Panel to Disabled.
B. Create a new local Group Policy object (GPO) linked to the User1 account. From User Configuration, set Prohibit Access to Control Panel to Enabled.
C. From Local Security Policy, set System objects: Strengthen default permissions of internal system objects (e.g., Symbolic Links) to Enabled and set User Account Control: Admin Approval Mode for the Built-in Administrator account to Disabled.
D. From Local Security Policy, set System objects: Strengthen default permissions of internal system objects (e.g., Symbolic Links) to Disabled and set User Account Control: Admin Approval Mode for the Builtin Administrator account to Enabled. Answer: B
Explanation:
Group Policy Settings for Control Panel. There are several Group Policy settings that control the behavior of Control Panel in Windows 7. The full path of this node in the Group Policy Management Console is: User ConfigurationAdministrative TemplatesControl PanelProhibit access to the Control PanelThis policy setting allows you to disable all Control Panel programs.If you enable this policy setting, you prevent Control.exe from starting. As a result, users cannot start Control Panel or run any Control Panel items. It also removes Control Panel from the Start menu, and it removes the Control Panel folder from Windows Explorer. If users try to select a Control Panel item from the Properties menu, a message appears that explains a policy setting prevents the action. QUESTION 224
Your network has a main office and a branch office. The branch office has five client computers that run Windows 7 and a server that runs Windows Server 2008 R2. The branch office server is enabled for BranchCache. You need to configure Windows Firewall on each client computer so that cached content can be retrieved from the branch office server. Which firewall rule should you enable on the client computers? A. BranchCache - Content Retrieval (Uses HTTP)
B. BranchCache - Hosted Cache Server (Uses HTTPS)
C. BranchCache - Peer Discovery (Uses WSD)
D. File and Printer Sharing Answer: A
Explanation:
Configure domain member client distributed cache mode firewall rules When you configure BranchCache in distributed cache mode, BranchCache client computers use the Hypertext Transfer Protocol (HTTP) for data transfer with other client computers. BranchCache client computers also use the Web Services Dynamic Discovery (WS-Discovery) protocol when they attempt to discover content on client cache servers. You can use this procedure to configure client firewall exceptions to allow incoming HTTP and WS-Discovery traffic on client computers that are configured for distributed cache mode. The BranchCache ?Content Retrieval (Uses HTTP) predefined rule. If this rule is not available, create rules that allow inbound and outbound traffic on TCP port 80. This rule is required for both Hosted Cache and Distributed Cache mode. The BranchCache ?Peer- Discovery (Uses WSD) predefined rule. If this rule is not available, create rules that allow inbound and outbound traffic on UDP port 3702. This rule is only required when using Distributed Cache mode. The BranchCache Hosted Cache Client (HTTPS-Out) predefined rule. It this rule is not available, configure a rule that allows outbound traffic on TCP port 443. This rule is required only when using Hosted Cache mode. QUESTION 225
You have an answer file for a Windows 7 installation. You need to perform an unattended installation of Windows 7 by using the answer file. What should you do? A. Name the answer file autounattend.ini and save it to a USB disk. Start the computer from the Windows 7 DVD.
B. Name the answer file unattend.txt and save it to a USB disk. Start the computer from the Windows Preinstallation Environment (Windows PE).
C. Name the answer file autounattend.xml and save it to a USB disk. Start the computer from the Windows 7 DVD.
D. Name the answer file unattend.xml and save it to a USB disk. Start the computer from the Windows Preinstallation Environment (Windows PE). Answer: C
Explanation:
Unattended installation
You can perform an unattended installation of Windows 7 by using an installation file called Unattend.xml. These installation files store answers to the questions asked by the Setup Wizard. When the Windows 7 installation process starts, Windows checks for attached USB storage devices that have this file in their root directory. Unattended installations are suitable when you need to deploy Windows 7 to a large number of computers because you do not have to interact with them manually, responding to prompts, as the installation progresses.Building a Reference Installation You configure your reference computer with a customized installation of Windows 7 that you then duplicate onto one or more destination computers. You can create a reference installation by using the Windows product DVD and (optionally) the answer file you created in the previous section. To install your reference computer using an answer file, perform the following procedure:
1. Turn on the reference computer. Insert the Windows 7 product DVD and the UFD containing the answer file (Autounattend.xml) that you created in the previous section. Note that the use of an answer file is optional, although it is the method Microsoft recommends. If you prefer, you can install Windows 7 manually from the installation DVD-ROM.
2. Restart the computer by pressing CTRL+ALT+DEL. You may have to override the boot order to boot from the CD/DVD-ROM disk. If so, select the appropriate function key to override the boot order during initial boot. Windows Setup (Setup.exe) starts automatically and searches the root directory of all removable media for an answer file called Autounattend.xml.
3. After Setup finishes, you can validate that all customizations were applied. For example, if you included the optional Microsoft-Windows-IE-InternetExplorer feature and set the Home_Page setting in your answer file, you can verify these settings by opening Internet Explorer.
4. To prepare the reference computer for the user, you use the Sysprep utility with the /generalize option to remove hardware-specific information from the Windows installation and the /oobe option to configure the computer to boot to Windows Welcome upon the next restart. QUESTION 226
You have a Windows 7 Windows image (WIM) that is mounted. You need to view the list of third-party drivers installed in the image. What should you do? A. Run Dism.exe and specify /get drivers parameter.
B. Run Driverquery.exe and specify the /si parameter.
C. From Device Manager, view all hidden devices.
D. From Windows Explorer, open the WindowsSystem32Drivers folder from the mount folder. Answer: A
Explanation:
DismDeployment Image Servicing and Management (DISM) is a command-line tool used to service Windows images offline before deployment. You can use it to install, uninstall, configure, and update Windows features, packages, drivers, and international settings. Subsets of the DISM servicing commands are also available for servicing a running operating system. Windows 7 introduces the DISM command-line tool. You can use DISM to service a Windows image or to prepare a Windows PE image. DISM replaces Package Manager (Pkgmgr.exe), PEimg, and Intlcfg in Windows Vista, and includes new features to improve the experience for offline servicing. You can use DISM to perform the following actions: - Prepare a Windows PE image.
- Enable or disable Windows features within an image.
- Upgrade a Windows image to a different edition.
- Add, remove, and enumerate packages.
- Add, remove, and enumerate drivers.
- Apply changes based on the offline servicing section of an unattended answer file.
- Configure international settings.
- Implement powerful logging features.
- Service operating systems such as Windows Vista with SP1 and Windows Server 2008.
- Service a 32-bit image from a 64-bit host and service a 64-bit image from a 32-bit host.
- Service all platforms (32-bit, 64-bit, and Itanium).
- Use existing Package Manager scripts.
NOT DriverqueryEnables an administrator to display a list of installed device drivers and their properties. If used without parameters, driverquery runs on the local computer. (Could not see documention of images, only computers, therefore assumed this command does not support images) /si : Displays digital signature information for both signed and unsigned device drivers. QUESTION 227
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. AnAnswer choice may be correct for more than one QUESTION in the series.
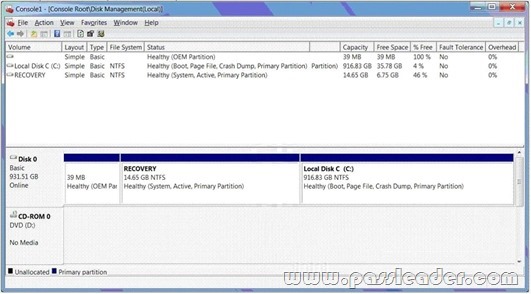
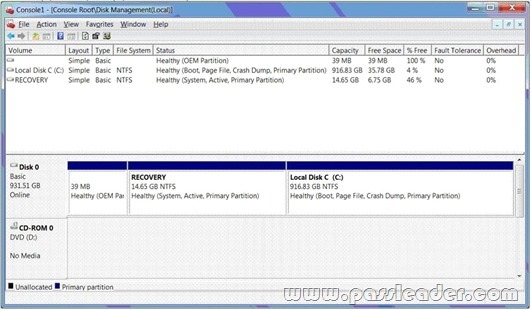
You use a desktop computer that has Windows 7 Ultimate SP1. This relevant portions of the computer configuration are shown in the following below.
- The Disk Management Console (Click the Exhibit button.)
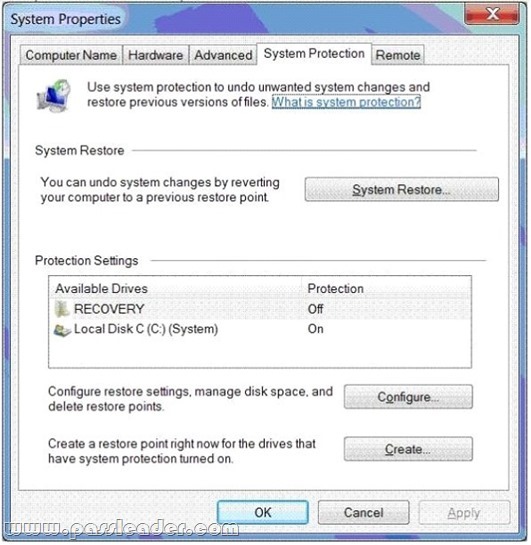
- The System Properties window (Click the Exhibit button.)
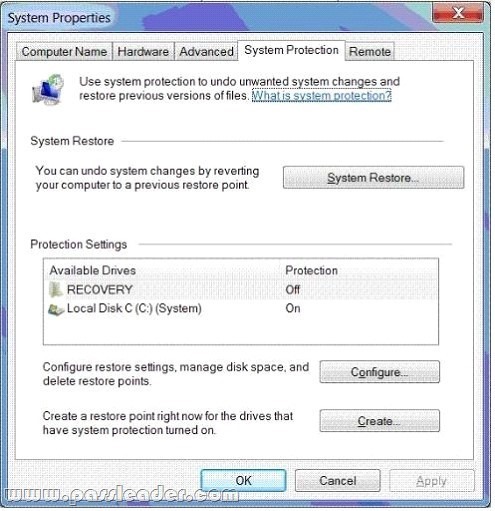
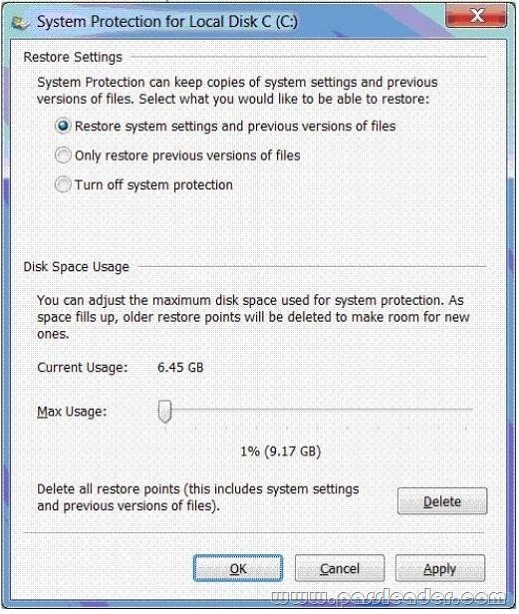
- The System protection for Local Disk C window (Click the Exhibit button.)
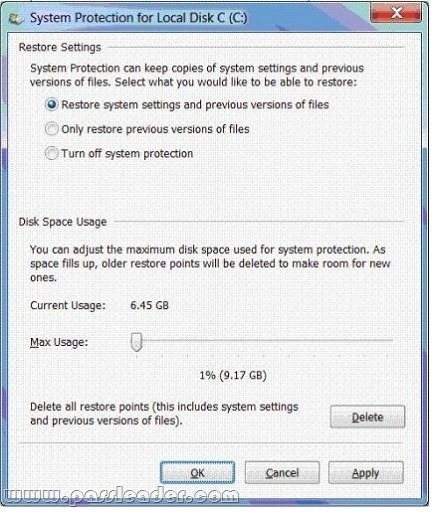
You create a password for several Microsoft Office files from your Documents library. You share the Documents library over a network. You need to ensure that network users are unable to access the unprotected version of the files. What should you do? A. Delete restore points.
B. Create a restore point.
C. Perform a system restore.
D. Search for the file in the Recycle Bin.
E. Increase disk space used for system protection.
F. Copy the file from a previous version of a folder.
G. Set restore settings Only restore previous version of files.
H. Run the cipher /x command from the elevated command prompt.
I. Run the vssadmin list volumes command from the elevated command prompt.
J. Run the vssadmin list shadows command form the elevated command prompt.
K. Run the compact /U <file_name> command form the elevated command prompt. Answer: A QUESTION 228
Note: This question is part of a series of questions that use the same set of answer choices. An Answer choice may be correct for more than one question in the series.
You use a desktop computer that has Windows 7 Ultimate SP1. This relevant portions of the computer configuration are shown in the following below.
- The Disk Management Console (Click the Exhibit button.)
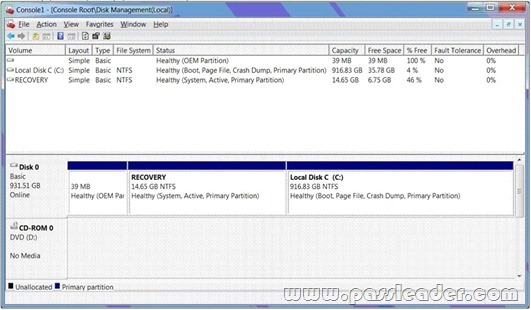
- The System Properties window (Click the Exhibit button.)
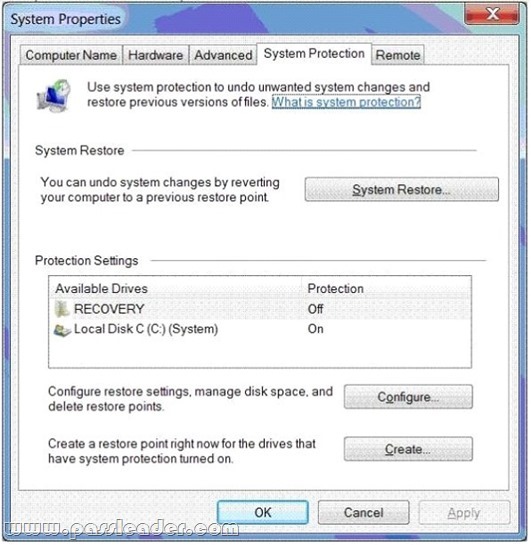
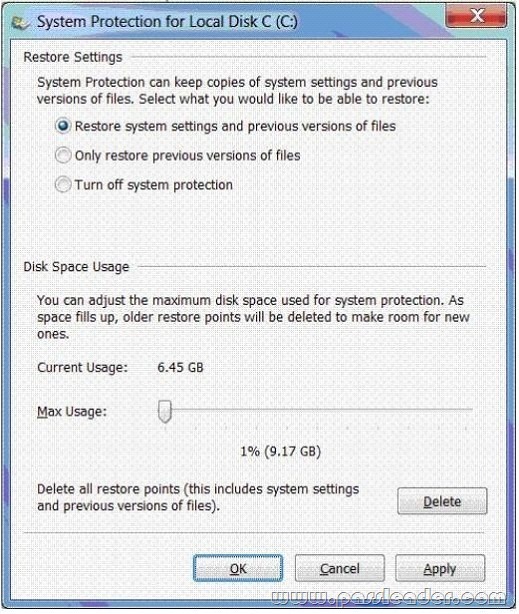
- The System protection for Local Disk C window (Click the Exhibit button.)
You share your Documents library over a network. You discover that one of the files in the library was replaced with a previous version and then renamed. You need to restore the most recent version of the original file. What should you do? A. Delete restore points.
B. Create a restore point.
C. Perform a system restore.
D. Search for the file in the Recycle Bin.
E. Increase disk space used for system protection.
F. Copy the file from a previous version of a folder.
G. Set restore settings Only restore previous version of files.
H. Run the cipher /x command from the elevated command prompt.
I. Run the vssadmin list volumes command from the elevated command prompt.
J. Run the vssadmin list shadows command form the elevated command prompt.
K. Run the compact /U <file_name> command form the elevated command prompt. Answer: F
Explanation:
Note: To restore a previous version of a file or folder that's included in a library, right-click the file or folder in the location where it's saved, rather than in the library. For example, to restore a previous version of a picture that's included in the Pictures library but is stored in the My Pictures folder, right-click the My Pictures folder, and then click Restore previous versions. QUESTION 229
Note: This question is part of a series of questions that use the same set of answer choices. An Answer choice may be correct for more than one question in the series.
You use a desktop computer that has Windows 7 Ultimate SP1. This relevant portions of the computer configuration are shown in the following below.
- The Disk Management Console (Click the Exhibit button.)
- The System Properties window (Click the Exhibit button.)
- The System protection for Local Disk C window (Click the Exhibit button.)
You share the Pictures library over a network. You discover that a JPEG image file located in the library was moved by a network user into a ZIP archive and is protected by using a password. You need to open the image file. What should you do? A. Delete restore points.
B. Create a restore point.
C. Perform a system restore.
D. Search for the file in the Recycle Bin.
E. Increase disk space used for system protection.
F. Copy the file from a previous version of a folder.
G. Set restore settings Only restore previous version of files.
H. Run the cipher /x command from the elevated command prompt.
I. Run the vssadmin list volumes command from the elevated command prompt.
J. Run the vssadmin list shadows command form the elevated command prompt.
K. Run the compact /U <file_name> command form the elevated command prompt. Answer: F
Explanation:
Note: To restore a previous version of a file or folder that's included in a library, right-click the file or folder in the location where it's saved, rather than in the library. For example, to restore a previous version of a picture that's included in the Pictures library but is stored in the My Pictures folder, right-click the My Pictures folder, and then click Restore previous versions. QUESTION 230
You have a computer that runs Windows 7. You have a system image backup of the computer. You install a new application that is configured to run as a service. You restart the computer and receive a STOP error message. You need to successfully start Windows 7 in the minimum amount of time. What should you do? A. Start the computer from the Windows 7 installation media and select Startup Repair.
B. Start the computer and select Last Known Good Configuration from the advanced startup options.
C. Start the computer and select Safe Mode from the advanced startup options. Restore a restore point.
D. Start the computer and select Safe Mode from the advanced startup options. Restore the system image. Answer: B
Explanation:
Last Known Good Configuration (Advanced) ) feature in Advanced Boot Options is a recovery option that you use to start your computer with the most recent settings that worked. Last Known Good Configuration (Advanced) restores registry information and driver settings that were in effect the last time the computer started successfully. You should use the Last Known Good Configuration (Advanced) feature when you cannot start Windows 7 after you make a change to your computer, or when you suspect that a change that you just made is causing a problem, for example, if you cannot start Windows after you install a new video driver. When you start your computer by using the Last Known Good Configuration (Advanced) feature, Windows 7 uses the configuration stored in the following registry key: HKEY_LOCAL_MACHINESystemCurrentControlSetXX (where by XX are numbers starting with 01 and rising in number to 02, 03, 04 and so on). This is the registry key that is used to store the configuration settings for the Drivers and Services on the system. Each time you boot the system, Windows will be assisted booting by using the registry key "HKEY_LOCAL_MACHINESystemCurrentControlSet" which will point to another control set key, normally HKEY_LOCAL_MACHINESystemCurrentControlSet01, (depending on how the system is configured) which contains the setting for the current boot process. Each time Windows boots there will also be a values created under the "HKEY_LOCAL_MACHINESystemCurrentControlSetSelect" key. These contain REG_DWORD data that enable the Control Keys to operate the way they are designed to. These values tell the CurrentControlSet key which numbered CurrentControlSet to point to enable Windows to boot successfully. The data that tells Last Good Known Configuration which numbered CurrentControlSet to load is also stored under these values. They also contain the data that tells Windows which CurrentContolSet not to use, as there is information stored that lets Windows know what CurrentControlSet has failed to load when Windows was unable to boot. The Last Known Good Configuration CurrentControlSet will change each time the system configuration for the control set changes. This means that each time you install or uninstall a driver or service, a new numbered CurrentControlSet will be created and stored. If you alter the system, and it is then unable to boot, the Last Known Good Configuration will point to the CurrentControlSet that was last used in a successful boot. This happens each time that Windows boots and there should typically be only four control sets, although it is not uncommon to have five or six of these Control Sets contained in the registry. Windows will keep track of how many Control Sets are stored and should clear old ones once a certain amount is reached. If installing a new program or device should render the system unbootable, you may be able to use "Last Known Good Configuration" to restore the damaged Control Set registry key with an earlier key that enabled the system to boot. This will remove the registry key(s) that relates to the problem driver or service. It will not remove the actual driver or service but will render it unusable. This could result in any program or device the was installed after the last boot having to be re-installed as their configuration setting will have been over written. When you perform a system restore following a normal boot or following a boot that uses the Last Known Good Configuration (Advanced) option, a restore point is created that enables you to undo the changes if they do not fix your problem. However, if you perform a system restore when the computer is in Safe Mode or by using the System Recovery options, you cannot undo the restore operation. In this case, if your problem is not resolved, you can run another system restore and choose a different restore point.

http://www.passleader.com/70-680.html
|















