[Pass Ensure VCE Dumps] Real PassLeader 70-663 Braindumps And VCE Dumps Ensure 100 Percent Exam Passing (91-110)
Where To Get The 100% Valid 70-663 exam dumps? Come to PassLeader! Here you can get the latest version 70-663 PDF dumps or VCE dumps, we guarantee our 291q 70-663 exam questions are the latest and you will get all the new questions and answers, which are not available on other wesites now! Now try our best 70-663 exam dumps with VCE and you will acquire your 70-663 certification exam immediately. keywords: 70-663 exam,291q 70-663 exam dumps,291q 70-663 exam questions,70-663 pdf dumps,70-663 vce dumps,70-663 braindumps,70-663 practice test,70-663 study guide,Pro: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Exam 
QUESTION 91
You have an Exchange Server 2010 organization. You plan to delegate administration of the organization. You have a group named Technicians that contains all the level-two technicians in the organization. You need to ensure that the Technicians group can manage the properties of all the mailbox databases. The solution must minimize the number of permissions assigned to the Technicians group. Which management role should you assign to the Technicians group? A. Help Desk
B. Organization Management
C. Recipient Management
D. Server Management QUESTION 92
You have an Exchange Server 2010 organization. Your companys security policy states that users must not be able to encrypt e-mail messages by using Outlook Web App (OWA). You need to recommend a client access solution that meets the requirements of the security policy. What should you include in the solution? A. managed folder mailbox policies
B. multiple OWA virtual directories
C. OWA segmentation
D. WebReady Document Viewing Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/bb123962(v=exchg.80).aspx QUESTION 93
You have an Exchange Server 2010 organization that contains five Hub Transport servers, five Mailbox servers and one Edge Transport server. You need to provide a solution to ensure that users can prevent legitimate inbound e-mail messages from being classified as spam. What should you do? A. Enable sender filtering
B. Enable Sender ID filtering
C. Configure a custom MailTip
D. Configure safelist aggregation Answer: D QUESTION 94
You have an Exchange Server 2010 organization. You plan to delegate Exchange administrative rights to some users in the organization. You need to recommend a solution that tracks all changes made to the Exchange organization. What should you include in the solution? A. administrator audit logging
B. circular logging
C. diagnostic logging
D. Windows Security Auditing Answer: A QUESTION 95
You have an Exchange Server 2010 organization that contains Windows Mobile 5.0 devices. Your company plans to replace all mobile devices with Windows Mobile 6.5 devices. You need to identify which users accessed their mailboxes by using Windows Mobile 5.0 devices in the past month. What should you do? A. Create a Data Collector Set.
B. Install and run the Exchange Server User Monitor (ExMon).
C. Export and review the Internet Information Services (IIS) logs.
D. Enable User Agent logging, and then review the agent logs. Answer: C QUESTION 96
You have an Exchange Server 2010 organization. You need to recommend a solution that prevents the permanent deletion of e-mail messages from the mailboxes of employee who have been dismissed from the company. What should you recommend? A. Implement managed folders.
B. Implement a legal hold for each mailbox.
C. Implement a Retention Policy for each mailbox.
D. Implement an Outlook Protection Rule for each mailbox. Answer: B QUESTION 97
You have an Exchange Server 2010 organization. The organization contains a global security group named Group1. You plan to deploy a monitoring solution for the Exchange servers in your organization. You need to recommend a solution that allows members of Group1 to monitor the performance of Exchange Server 2010 servers. Your solution must prevent members of Group1 from modifying the configurations of the Exchanges Server 2010 organization. What should you include in the solution? A. Delegation of Control Wizard
B. Federation Trusts
C. Reliability Monitor
D. Role Based Access Control (RBAC) Answer: D QUESTION 98
Your company has a main office and 10 branch offices. You have an Exchange Server 2010 organization. All Exchange servers are installed on virtual machines. You need to create a monitoring plan for the Exchange servers that meets the following requirements:
- Identify Exchange server errors
- Provide alerts when Exchange services are stopped
- Produce statistical analysis and reporting
Which tool should you include in the plan? A. Microsoft System Center Service Manager
B. Microsoft System Center Operations Manager
C. Microsoft System Center Configuration Manager
D. Microsoft System Center Virtual Machine Manager Answer: B
Explanation:
System Center Operations Manager 2007 R2, Microsoft's end-to-end service-management product, is your best choice for Windows environments. It works seamlessly with Microsoft infrastructure servers, such as Windows Server, and application servers, such as Microsoft Exchange, helping you to increase efficiency while enabling greater control of the IT environment.
http://www.microsoft.com/en-us/server-cloud/system-center/operations-manager.aspx QUESTION 99
Your network consists of an Active Directory domain that contains the domain controllers shown in the following table.
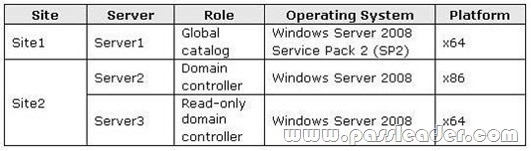
You plan to deploy an Exchange Server 2010 server in each site. You need to recommend changes to the domain controllers to support the installation of Exchange Server 2010. What should you do? A. Enable Server2 as a global catalog server.
B. Enable Server3 as a global catalog server.
C. Upgrade Server2 to Windows Server 2008 SP2 (x64).
D. Upgrade Server3 to Windows Server 2008 SP2 (x64). Answer: A
Explanation:
The global catalog maintains an index of the Active Directory database for objects within its domain. Additionally, it stores partial copies of data for all other domains within a forest. Exchange Server relies on global catalog servers to resolve email addresses for users within the organization. Failure to contact a global catalog server causes emails to bounce, as the recipient's name cannot be resolved. Microsoft Exchange Server 2010 stores all configuration and recipient information in the Active Directory directory service database. When a computer that is running Exchange 2010 requires information about recipients and information about the configuration of the Exchange organization, it must query Active Directory to access the information. Active Directory servers must be available for Exchange 2010 to function correctly. By default, whenever an Exchange 2010 server starts, it binds to a randomly selected domain controller and global catalog server in its own site. You can view the selected directory servers by viewing the properties of the Exchange 2010 server in the Exchange Management Console or by using the Get-ExchangeServer cmdlet in the Exchange Management Shell. You can also use the Set-ExchangeServer cmdlet to configure a static list of domain controllers to which an Exchange 2010 server should bind or a list of domain controllers that should be excluded. You can't deploy an Exchange 2010 server in any site that contains only read-only directory servers. QUESTION 100
Your company has a main office and 50 branch offices. Each office is configured as an Active Directory site. Each branch office site contains a domain controller. The main office site contains all the global catalog servers in the forest. Each branch office contains a WAN link that connects to the main office. You need to plan the deployment of new Mailbox servers to meet the following requirements:
- Ensure that users in the branch offices can access their mailboxes if their local domain controller fails
- Deploy the minimum number of Exchange servers
What should you include in the plan? A. One Mailbox server in each office and global catalog servers in each branch office
B. One Mailbox server in each office and Universal Group Membership Caching in each branch office
C. One Mailbox server in each branch office only
D. Multiple Mailbox servers in the main office only Answer: D
Explanation:
This is an interesting question however if you break it down it starts to make sense Main Office has the Global Catalog Servers - not the Branch Offices Branch Offices connect to the main office via a Wan Link While each branch office does have a domain controller they are not Global Catalog Servers. Further there are 50 branch offices so it makes no sense to deploy a mailbox server in each branch office or to have 50 Global Catalog Servers. The best answer is D as this would meet the requirement of deploying the least amount of Exchange Servers.

http://www.passleader.com/70-663.html QUESTION 101
Your Exchange Server 2010 organization contains two Hub Transport servers in a single site. The organization receives all e-mail sent to a SMTP domain named contoso.com. Your company purchases another company that uses a SMTP domain named fabrikam.com. You plan to manage message hygiene for both SMTP domains. You need to recommend changes to the organization to support the planned deployment. The solution must prevent e-mail sent to fabrikam.com from being delivered to your internal organization. What should you recommend? A. Deploy a new Hub Transport server, and then create remote domains.
B. Deploy a new Hub Transport server, and then configure transport rules.
C. Deploy an Edge Transport server, and then create accepted domains.
D. Deploy an Edge Transport server, and then configure a federation trust. Answer: C QUESTION 102
You have an Exchange Server 2010 organization. You need to recommend a storage solution that meets the following requirements:
- Provides users with an alternate location for storing e-mail messages
- Provides users with access to the alternate location by using Outlook Web App (OWA)
What should you recommend? A. journal rules
B. managed folders
C. personal archives
D. personal folders (.pst) Answer: C QUESTION 103
You have an Exchange Server 2010 organization. Your company's legal department sends compliance e-mail messages by adding recipients to the blind carbon copy (Bcc) field. The company's compliance policy includes the following requirements:
- All e-mail messages sent to external recipients must be archived in a central repository
- Compliance officers must be able to identify all the recipients of archived e-mail messages
You need recommend a solution to meet the compliance policy requirements. What should you recommend? A. journal rules
B. message tracking
C. Personal Archives
D. transport rules Answer: A QUESTION 104
You have an Exchange Server 2010 organization for a company named Contoso, Ltd. Contoso has the following security policy:
- Messages that contain the word budget cannot be sent to external recipients
- Messages that contain the name Northwind Traders must be sent to the legal department automatically
You need to recommend a solution to meet the security policy. What should you recommend? A. Create two transport rules.
B. Create two message classifications.
C. Create one transport rule and configure a legal hold.
D. Create one message classification and configure a legal hold. Answer: A QUESTION 105
You have an Exchange Server 2010 organization. You have a group named Help Desk that contains all the help desk users in the organization. You need to ensure that the Help Desk group can manage all the mailboxes and mail-enabled contacts in the organization. The solution must minimize the number of permissions assigned to the Help Desk group. Which management role should you assign to the Help Desk group? A. Mail Recipients
B. Mail Recipient Creation
C. Organization Client Access
D. Recipient Policies Answer: A
Explanation:
Section: Designing and Deploying Messaging Compliance, System Monitoring, and Reporting The Mail Recipients management role enables administrators to manage existing mailboxes, mail users, and mail contacts in an organization. This role can't create these recipients. Use the Mail Recipient Creation role to create them. This role type doesn't enable you to manage mail-enabled public folders or distribution groups. Use the following roles to manage these objects:
Mail Enabled Public Folders Role
Distribution Groups Role
http://technet.microsoft.com/en-us/library/dd876911.aspx QUESTION 106
You have an Exchange Server 2010 organization. You need to plan a message hygiene solution that meets the following requirements:
- Spoofing must be minimized
- Open SMTP relays must be added to IP block lists automatically
What should you include in the plan? A. Sender ID filtering and recipient filtering
B. Sender ID filtering and sender reputation
C. sender filtering and recipient filtering
D. sender reputation and recipient filtering Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/bb124512.aspx QUESTION 107
Your network contains an Exchange Server 2010 server. You need to plan a mailbox sharing solution for the organization to meets the following requirements:
- Ensure that assistants can read and modify the e-mail messages of their managers
- Ensure that assistants can impersonate their managers when they send e-mail messages
What should you include in the plan? A. Full Access and Send As permissions
B. Full Access and send on behalf of permissions
C. Role Based Access Control (RBAC) assignments and Send As permissions
D. Role Based Access Control (RBAC) assignments and send on behalf of permissions Answer: A
Explanation:
You have to:
1. Grant access to a mailbox and its content.
2. Grant the right to send messages as the mailbox owner. In the Exchange Management Console, right-click the mailbox you want to work with and then select "Manage Full Access Permission" or "Manage Send As Permission". QUESTION 108
You have an Exchange Server 2010 organization named contoso.com. The organization contains two Client Access servers named CAS1 and CAS2 that are in a Client Access server array. All internal and external users connect to their mailboxes by using mail.contoso.com. You need to install a certificate on the Client Access servers to meet the following requirements:
- Support 500 client computers that are not joined to the Active Directory domain
- Support clients that use Microsoft Office Outlook in Cached Exchange Mode, Autodiscover, and Exchange ActiveSync
- Minimize client and user support costs
What should you do? A. From a trusted third-party certification authority (CA), generate a certificate request that contains the mail.contoso.com and Autodiscover names.
B. From a trusted third-party certification authority (CA), generate a certificate request that contains the CAS1.contoso.com and CAS2.contoso.com names.
C. From an internal Active Directory-integrated certification authority (CA), generate a certificate request that contains the mail.contoso.com and Autodiscover names.
D. From an internal Active Directory-integrated certification authority (CA), generate a certificate request that contains the CAS1.contoso.com and CAS2.contoso.com names. Answer: A QUESTION 109
You have an Exchange Server 2010 organization. Your company has a relationship with another company. The partner company has an Exchange Server 2010 organization. You need to recommend a security solution to meet the following requirements:
- Ensure that all e-mail delivery between your servers and the partner company's servers is encrypted
- Ensure that all communication between your servers and the partner company's servers is authenticated
What should you include in the solution? A. Active Directory Rights Management Services (AD RMS)
B. Domain Security
C. Forms-based Authentication
D. Secure/Multipurpose Internet Mail Extensions (S/MIME) Answer: B
Explanation:
Domain Security refers to the set of functionality in Microsoft Exchange Server 2010 and Microsoft Office Outlook 2007 that provides a relatively low-cost alternative to S/MIME or other message-level security solutions. The purpose of the Domain Security feature set is to provide administrators a way to manage secured message paths over the Internet with business partners. After these secured message paths are configured, messages that have successfully traveled over the secured path from an authenticated sender are displayed to users as Domain Secured in the Outlook and Microsoft Office Outlook Web App interface. Domain Security uses mutual Transport Layer Security (TLS) authentication to provide session-based authentication and encryption. Mutual TLS authentication differs from TLS as it's usually implemented. Typically, when TLS is implemented, the client verifies that the connection securely connects to the intended server by validating the server's certificate. This is received as part of TLS negotiation. In this scenario, the client authenticates the server before the client transmits data. However, the server doesn't authenticate the session with the client. With mutual TLS authentication, each server verifies the connection with the other server by validating a certificate that's provided by that other server. In this scenario, where messages are received from external domains over verified connections in an Exchange 2010 environment, Outlook 2007 displays a Domain Secured icon.
http://technet.microsoft.com/en-us/library/bb124392.aspx QUESTION 110
Your company has an Active Directory forest named contoso.com. You plan to deploy an Exchange Server 2010 organization that will contain two servers. Each server will have the Client Access server role, the Hub Transport server role, and the Mailbox server role installed. You plan to add both servers to a database availability group (DAG). You need to recommend a high-availability solution for the Client Access server role. Your solution must ensure that users are not prompted to authenticate if a Client Access server becomes unavailable. What should you recommend? A. Create and configure a Client Access server array, and then install a hardware load balancer.
B. Create and configure a Client Access server array, and then install Windows Network Load Balancing on both servers.
C. Deploy Microsoft Internet Security and Acceleration (ISA) Server 2006, and then implement DNS round robin.
D. Deploy Microsoft Internet Security and Acceleration (ISA) Server 2006, and then install Windows Network Load Balancing. Answer: A
Explanation:
While it is possible to install the Windows Network Load Balancing for a client access array that solution will not work for this question.
Windows Network Load Balancing. Windows Network Load Balancing (WNLB) is the most common software load balancer used for Exchange servers. There are several limitations associated with deploying WNLB with Microsoft Exchange.
WNLB can't be used on Exchange servers where mailbox DAGs are also being used because WNLB is incompatible with Windows failover clustering. If you're using an Exchange 2010 DAG and you want to use WNLB, you need to have the Client Access server role and the Mailbox server role running on separate servers. Due to performance issues, we don't recommend putting more than eight Client Access servers in an array that's load balanced by WNLB.
WNLB doesn't detect service outages. WNLB only detects server outages by IP address. This means if a particular Web service, such as Outlook Web App, fails, but the server is still functioning, WNLB won't detect the failure and will still route requests to that Client Access server. Manual intervention is required to remove the Client Access server experiencing the outage from the load balancing pool.
WNLB configuration can result in port flooding, which can overwhelm networks. Because WNLB only performs client affinity using the source IP address, it's not an effective solution when the source IP pool is small. This can occur when the source IP pool is from a remote network subnet or when your organization is using network address translation.
http://technet.microsoft.com/en-us/library/ff625247.aspx

http://www.passleader.com/70-663.html
|

