Preparing 70-686 exam with vaild 70-686 exam dumps, trying PassLeader’s 70-686 vce dumps or 70-686 pdf dumps, our 70-686 exam dumps coverd all the real exam questions, all new 70-686 exam questions are available in PassLeader’s 70-686 braindumps. Our 200q 70-686 premium vce file is the best study guide for preparing 70-686 exam, browsing PassLeader’s website and download 200q 70-686 exam questions.
keywords: 70-686 exam,200q 70-686 exam dumps,200q 70-686 exam questions,70-686 pdf dumps,70-686 vce dumps,70-686 braindumps,70-686 practice test,70-686 study guide,Pro: Windows 7, Enterprise Desktop Administrator Exam

QUESTION 16
Your company has 1,000 client computers. You are planning to deploy Windows 7 and a new line-of-business application. You have the following requirements:
* Install the application as part of the standard Windows 7 deployment.
* Use a single Windows 7 image for the deployment.
The application must be available for use on client computers that are not connected to the network. You need to ensure that the application is installed on all new client computers. What should you do?
A. Deploy the application by using Windows Server Update Services (WSUS).
B. Publish the application by using Group Policy Software Installation.
C. Service an offline image of Windows 7 to add the new application.
D. Service an online image of Windows 7 to add the new application.
Answer: D
QUESTION 17
You deploy Windows 7 Enterprise to 1,000 client computers by using an image file. You need to define an image update strategy to incorporate software updates. What should you do?
A. Install the deployment image on a client computer. Run the update package on the client computer, run Sysprep, and then recapture the image.
B. Append a disk volume that contains the update to the deployment image.
C. Mount the deployment image on a client computer that runs Windows 7. Run the updatepackage on the client computer.
D. Install the deployment image on a client computer. Run the update package on the client computer, run BCDedit, and then recapture the image.
Answer: A
QUESTION 18
You are planning to upgrade Internet Explorer. You have the following requirements:
* create a report that identifies which computers are succesfully upgraded
* do not install additional software on the client computers
You need to design a deployment method that meets the requirements. What should you do?
A. Use Windows Server Update Services (WSUS)
B. Use Internet Explorer Administration Kit (IEAK) and Group Policy
C. Use Microsoft System Center Configuration Manager
D. Use Microsoft System Center Essentials
Answer: A
QUESTION 19
Your company has a single Active Directory Domain Services (AD DS) domain with Windows Server 2008 R2 member servers and 1,000 Windows 7 client computers. You are designing the deployment of a custom application. You have the following requirements:
* The application must be available to only users who need it.
* Minimize network traffic during deployment.
You need to design a deployment strategy that meets the requirements. Which deployment method should you use?
A. Microsoft Application Virtualization (App-V)
B. Microsoft System Center Configuration Manager 2007
C. RemoteApp and Desktop Connections
D. software installation in Group Policy
Answer: C
QUESTION 20
Your network consists of an Active Directory Domain Services (AD DS) forest with 1,000 client computers that run Windows XP. Nine hundred of the computers are on the local area network. One hundred computers are portable computers that connect to the main office only once every few months. You are planning to deploy Windows 7. You need to generate a report of the software that is installed on all client computers. You need this information as soon as possible. What should you use?
A. Microsoft System Center Data Protection Manager
B. Microsoft Desktop Optimization Pack
C. Microsoft System Center Essentials
D. Microsoft System Center Operations Manager
Answer: B
QUESTION 21
Your network has client computers that run Windows Vista. You are planning to deploy Windows 7. You need to detect and analyze the compatibility of an application that requires elevated privileges. What should you do?
A. Use the Standard User Analyzer (SUA) Wizard.
B. Run a virtual version of the Setup Analysis Tool (SAT).
C. Use the Standard User Analyzer (SUA) tool.
D. Run a stand-alone version of the Setup Analysis Tool (SAT).
Answer: C
QUESTION 22
Your company’s network has client computers that run Windows 7. Multiple users share the computers in the shipping department. These computers reside in the Shipping Computers Organizational Unit (OU). The company wants to deploy a new application. The application is not packaged. You have the following requirements:
* Deploy the application to all computers in the shipping department.
* Perform the deployment from a central location.
You need to plan the software deployment process to meet the requirements. Which two actions should you include in the process? (Each correct answer presents part of the solution. Choose two.)
A. Using Microsoft System Center Configuration Manager, create a collection that contains the shipping department computers, and assign the package to the collection.
B. Create a package by using Microsoft System Center Configuration Manager.
C. Create a Group Policy object (GPO) and add a software installation policy under the Computer Configuration container.
D. In the Group Policy Management Console, link the software installation policy to the Shipping Computers OU.
E. Using Microsoft System Center Configuration Manager, create a collection that contains the shipping department users, and assign the package to the collection.
Answer: AB

http://www.passleader.com/70-686.html
QUESTION 23
Your network has client computers that run Windows XP. All users access a custom line-ofbusiness application. The line-of-business application is not compatible with Windows 7. You are planning to deploy Windows 7. You have the following requirements:
* The application must run on all client computers.
* The application executable must reside on each client computer.
You need to manage application compatibility to meet the requirements. What should you do?
A. Install the application on a Remote Desktop Services server.
B. Install a shim for the application on each client computer.
C. Virtualize the application by using Microsoft Application Virtualization (App-V).
D. Install the Windows Compatibility Evaluator on each client computer.
Answer: B
QUESTION 24
Your company has 1,000 client computers that run Windows XP Professional x64. You are planning to deploy Windows 7 Enterprise x64. The company uses an application that is incompatible with Windows 7 Enterprise x64. You have the following requirements:
* Provide all users with access to the application.
* Deploy and manage the application by using a centralized solution.
You need to design a solution that meets the requirements. What should you do?
A. Install the application on all client computers by using Group Policy, and then use the Compatibility tab.
B. Install the Microsoft Application Virtualization (App-V) client on each client computer, and run the application in offline mode.
C. Install the Microsoft Enterprise Desktop Virtualization (MED-V) package on each client computer.
D. Install the Microsoft Application Virtualization (App-V) client on each client computer, and stream the application by using App-V.
Answer: C
QUESTION 25
Your companys network has client computers that run Windows 7. Multiple users share the computers in the shipping department. These computers reside in the Shipping Computers Organizational Unit (OU). The network design is shown in the following diagram.
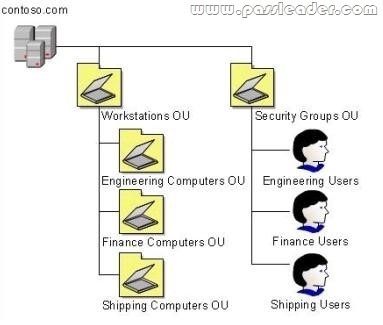
You are planning to deploy an application. The application is packaged as a Microsoft Windows Installer package (MSI). You need to deploy the application only to computers in the shipping department. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Link the software installation policy to the Workstations OU.
B. Link the software installation policy to the Shipping Computers OU.
C. Create a new Group Policy object (GPO) and add a software installation policy under the User Configuration container.
D. Create a new Group Policy object (GPO) and add a software installation policy under the Computer Configuration container.
Answer: BD
QUESTION 26
Your company has 1,000 Windows XP computers. You plan to migrate these computers to Windows 7. You need to detect compatibility issues that can occur during the installation and configuration process for a specific application. Which tool should you use?
A. Windows Compatibility Evaluator
B. Setup Analysis Tool
C. Inventory Collector
D. Update Compatibility Evaluator
Answer: B
QUESTION 27
Your companys network has client computers that run Windows 7. When a user attempts to log on to the domain from a computer named Client1, she receives the following message: The system cannot log you on to this domain because the system’s computer account in its primary domain is missing or the password on that account is incorrect. You need to ensure that the user can log on to the domain from Client1. What should you do?
A. Disjoin and rejoin Client1 to the domain.
B. Reset the account password for Client1 through Active Directory Users and Computers.
C. Add the computer account for Client1 to the Domain Computers Active Directory group.
D. Reset the account password for the user through Active Directory Users and Computers.
Answer: A
QUESTION 28
Your company has two Active Directory Domain Services (AD DS) domains, Domain1 and Domain2. A two-way trust relationship exists between the domains. Users in both domains can log on to client computers in only their own domains. System logs on the domain controllers display the error message Clock skew too great when users in Domain1 attempt to log on to client computers in Domain2. You need to ensure that users can log on to client computers in both domains. What should you do?
A. Decrease the Maximum tolerance for computer clock synchronization setting in the default Domain Group Policy object ( GPO ).
B. Configure the primary domain controller (PDC) emulatorin each domain to synchronize its clock with the same external time source.
C. Run a startup script that includes Net Time /setsntp on all client computers.
D. Run a startup script that includes Net Time /querysntp on all client computers.
Answer: B
QUESTION 29
Your company has an Active Directory Domain Services (AD DS) forest with a single domain named contoso.com. The design of the organizational units (OUs) and Group Policy objects (GPOs) is shown in the following diagram.
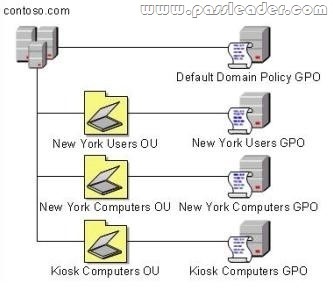
Multiple computer configuration settings and user configuration settings are defined in the Kiosk Computers GPO. A security audit indicates that user configuration settings that are defined in the Kiosk Computers GPO are not applied when users log on to client computers that are in the Kiosk Computers OU. You need to ensure that the user configuration settings are correctly applied. What should you do?
A. Enable loopback processing in Merge mode on the Default Domain Policy GPO.
B. Disable the user configuration settings on the Default Domain Policy GPO.
C. Enable loopback processing in Replace mode on the Kiosk Computers GPO.
D. Disable the user configuration settings on the New York Users GPO.
Answer: C
QUESTION 30
You have a single Active Directory Domain Services (AD DS) site. All client computers run Windows 7. Users in the marketing department use a custom application. You create a new Group Policy object (GPO) and link it to the site. Users in the marketing department then report that they are unable to use the custom application. You need to ensure that all users in the marketing department are able to use the custom application. You need to ensure that all other users continue to receive the new GPO. What should you do?
A. Add marketing users to a domain group. Use security filtering to grant the group the Allow-Read permission and the Allow-Apply Group Policy permission for the GPO.
B. Move marketing users to a dedicated organizational unit (OU). Apply the Block Inheritance setting to the OU.
C. Add marketing users to a domain group. Use security filtering to grant the group the Allow-Read permission and the Deny-Apply Group Policy permission for the GPO.
D. Move marketing users to a dedicated organizational unit (OU). Apply the Block Inheritance setting to the domain.
Answer: C

http://www.passleader.com/70-686.html