[Pass Ensure VCE Dumps] Download Free PassLeader Premium 196q 70-685 Exam Questions (71-90)
Need The newest 70-685 Exam Dumps? Why not try PassLeader's 196q 70-685 vce dumps or 70-685 pdf dumps? Recntly, the 70-685 exam has been changed with a lot of new questions, old version 70-685 vce dumps or practice tests are not valid now, if you want to pass exam 70-685 easily, please download the latest update 196q 70-685 braindumps from PassLeader. Now visit passleader.com and you will get all the 70-685 study materials including free 70-685 study guide with valid 70-685 vce dumps and free vce player, which will help you passing 70-685 exam easily! keywords: 70-685 exam,196q 70-685 exam dumps,196q 70-685 exam questions,70-685 pdf dumps,70-685 vce dumps,70-685 study guide,70-685 practice test,Pro: Windows 7, Enterprise Desktop Support Technician Exam 
QUESTION 71
The help desk reports that users receive a security warning message when they try to access the internal Web site shown in the exhibit:
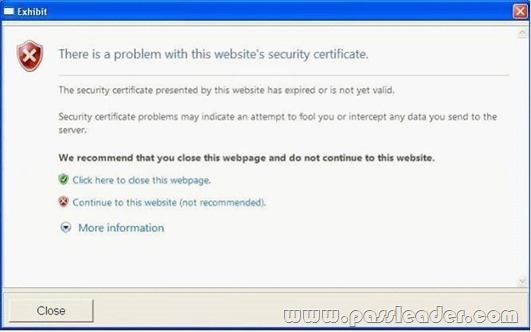
The help desk confirms that users never received this security warning message before. You need to provide a solution to prevent users from receiving the security warning when they try to access the internal Web site. What should you do? A. Instruct the users to download the certificate of the Web server.
B. Instruct the users to download a new certificate revocation list (CRL).
C. Request that a domain administrator renew the Web server SSL certificate.
D. Request that a domain administrator renew the user authentication certificates for all users. Answer: C QUESTION 72
Users in the branch office report slow network performance when they connect to the file shares in the main office. You need to recommend a solution to improve performance when users access the file shares from the branch office. The solution must minimize hardware costs. What should you recommend implementing? A. BranchCache
B. DirectAccess
C. Distributed File System Replication (DFSR)
D. Universal Group Membership Caching Answer: A
Explanation:
http://www.youtube.com/watch?v=vZboHyu9isA QUESTION 73
The help desk reports that all newly installed desktop computers cannot access the companys file server. The help desk sends you the screen capture shown in the exhibit:
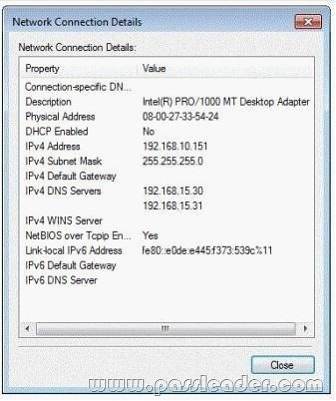
You need to resolve the network connectivity issue. The solution must adhere to the company policy. What should you instruct help desk to do?
 A. Modify Windows Firewall and enable File and Printer Sharing in the public profile.
B. Modify Windows Firewall and enable File and Printer Sharing in the domain profile.
C. Modify the network configuration and define the IPv4 default gateway.
D. Modify the network configuration to automatically obtain an IP address and a DNS server address. Answer: D Case Study 7 - Contoso, Ltd. (QUESTION 74 - QUESTION 77)
Scenario
You are an enterprise desktop support technician for Contoso, Ltd.
IP Addressing
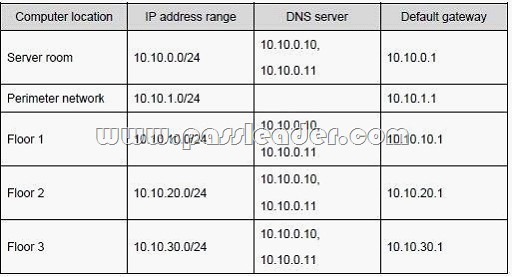
Contoso has one office. The IP addressing for Contoso is configured as shown in the following table:
Active Directory Configuration
You have an Active Directory forest that contains one domain named contoso.com. All domain controllers run Windows Server 2008 R2. An OU exists for each department in the company. The MainOffice Users and Computers OU contains the OUs for each department in the company. The Users OUs contains the user accounts for each department. The Computers OUs contain the computer accounts for each department. The Domain Controllers OU contains the computer accounts for all domain controllers. The Servers OU contains the computer accounts for all other servers. Custom Group Policy objects (GPOs) are linked to each departmental OU, the Domain Controllers OU, and the Servers OU.
Server Configuration
The relevant servers are configured as shown in the following table:
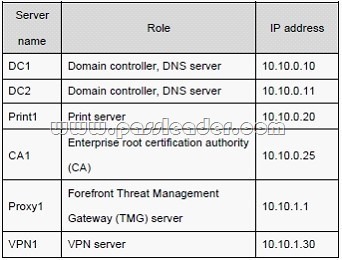
A year ago, a Windows Server 2008 R2 VPN server was deployed. Ten sales users participated in a pilot project to test the new VPN. The pilot project lasted two months. After the pilot project, the VPN server was put into production. The VPN server allows L2TP/IPSec-based VPN connections only. The VPN server requires certificate authentication.
Printer Configuration
Network printers are located in a single room on each floor. Users can search Active Directory to find printers that are nearby. Print1 is the print server for all printers.
Client Computer Configuration
Most users have desktop computers. Several users in the sales and management departments have portable computers because they travel frequently. All client computers run Windows 7 Enterprise. The Windows Internet Explorer proxy settings are configured on all client computers by using a GPO named GPO-IE. GPO-IE is linked to the domain. All users in the company use a custom application named App1. App1 is manually installed on all client computers. A new version of App1 is available. Some features in the new version of App1 are incompatible with the previous version of App1. QUESTION 74
The help desk reports that several users use the previous version of App1, which causes some data to become corrupt. You need to recommend a solution to prevent all users from using the previous version of App1. What should you recommend? A. that a domain administrator create a GPO linked to the domain and configure AppLocker settings in the GPO
B. that a domain administrator create a GPO linked to the domain and configure Software Installation settings in the GPO
C. that the new version of App1 be added to the Data Execution Prevention (DEP) settings on each client computer
D. that the previous version of App1 be added to the Data Execution Prevention (DEP) settings on each client computer Answer: A QUESTION 75
A new print device is installed on Floor 1 and shared on Print1. Users report that when they search Active Directory for printers on Floor 1, the new shared printer is missing. All other shared printers on Floor 1 appear. The help desk reports that users can manually connect to the shared printer. You need to ensure that the new shared printer is displayed when users search for printers on Floor 1. What should you do? A. Modify the permissions of the printer.
B. Configure a network location for the printer.
C. Request that a domain administrator modify the Active Directory site configuration.
D. Request that a domain administrator modify the GPO that is linked to each departmental OU. Answer: B QUESTION 76
The sales users that were part of the VPN server pilot project report that they can no longer establish VPN connections to the internal network. You need to ensure that all authorized users can establish VPN connections to the internal network. What should you request a domain administrator to do? A. Enable auto-renewal for certificates.
B. Increase the lifetime of the Kerberos user ticket.
C. Increase the lifetime of the Kerberos service ticket.
D. Increase the certification validity period for the computer certificate template. Answer: A QUESTION 77
Portable computer users report that they can use Internet Explorer to browse Internet Web sites only when they are connected to the company network. You need to ensure that portable computer users can access Internet Web sites from wherever they connect. What should you do? A. Instruct the users to configure static IPv4 settings.
B. Instruct the users to configure automatic IPv4 settings.
C. Request that a domain administrator link GPO-IE to Active Directory site objects.
D. Request that a domain administrator create a new GPO that modifies the Internet Explorer Maintenance settings, and then link the new GPO to the Users OUs. Answer: C Case Study 8 - Fourth Coffee (QUESTION 78 - QUESTION 81)
Scenario
You are an enterprise desktop support technician for Fourth Coffee. The network contains a single domain named fourthcoffee.com.
Physical Environment
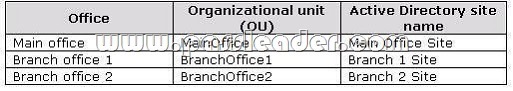
The company has three offices. The offices are configured as shown in the following table:
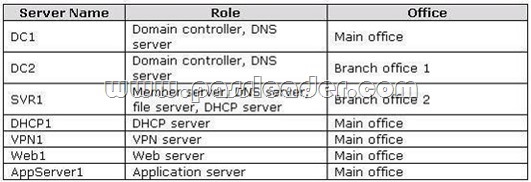
The relevant servers are configured as shown in the following table:
The Web1 server is accessible only through the URL http://web1.fourthcoffee.local.
Application Configurations
Fourth Coffee deploys an application named App1 to users in the main office by using a Group Policy Object (GPO) named APP1Deploy. App1 requires that a drive named M be mapped to \AppServer1AppData$. App1 saves information on a local computer if drive M is unavailable. All client computers have drive M.
Security Policy
The corporate security policy states that domain controllers can only be deployed in secure data centers. Branch office 2 does not have a secure data center.
Client Configuration
All users connect remotely through VPN1. VPN1 is configured to accept only SSTP-based VPN connections. All client computers receive IP configurations from DHCP. You recently purchased 100 desktop computers from a new hardware vendor. QUESTION 78
The application support team reports that the App1 data of some users is not saved to AppServer1. The team reports that the users deleted the mapped drive. You need to prevent the users from deleting the mapped drive. Which settings should you request be modified in the APP1Deploy GPO? A. Administrative Templates
B. AppLocker
C. Group Policy Preferences
D. Software Restriction Policies Answer: C
Explanation:
A. Administrative Templates. The Administrative Template files allow you to configure and manage registry-based Group Policy settings. They are Unicode text files with the extension .adm in Windows XP with SP2 and Windows Server 2003 with SP1, and XML files with the extensions .admx and .adml in Windows Vista and later versions of Windows. Standard Administrative Templates are deployed with your Windows operating systems. Administrative Templates display the registry settings that you can apply to your users' computers in your GPOs. Information in the templates populates the administrative interface in Group Policy Object Editor, which you use to set secure registry-based policy information. A number of standard templates automatically populate the Group Policy Object Editor, and you can add or remove templates later. Developers can create custom templates as needed.
C. Group Policy Preferences. You can use Group Policy preferences to better deploy and manage operating system and application settings. Group Policy preferences enable IT professionals to configure, deploy, and manage operating system and application settings they previously were not able to manage using Group Policy. Examples include mapped drives, scheduled tasks, and Start menu settings. For many types of operating system and application settings, using Group Policy preferences is a better alternative to configuring them in Windows images or using logon scripts. Group Policy preferences can be used to implement settings which are "preferred" but not mandatory. This enables IT professionals to deploy software (including Internet Explorer 8) in a standardized initial configuration and still permit users to customize some aspects to their liking. QUESTION 79
The help desk reports that the new computers experience intermittent failures that generate stop errors. You need to collect all the critical errors from the new computers. What should you configure? A. a boot configuration data (BCD) store
B. debugging information
C. event subscriptions
D. the system protection settings Answer: C QUESTION 80
VPN users report that they cannot access shared resources in the branch offices. They can access shared resources in the main office. Users in the main office report that they can access shared resources in the branch offices. You need to ensure that the VPN users can access shared resources in the branch offices. What should you request? A. that a change be made to the routing table on VPN1
B. that VPN1 be configured to support PPTP-based VPN connections
C. that the routers between the main office and the branch offices be reconfigured
D. that a DNS record for servers in the branch offices be added to the Internet DNS zone for fourthcoffee.com Answer: A

http://www.passleader.com/70-685.html QUESTION 81
Users in branch office 2 map drives to shared folders on SRV1. The users report that they cannot access files in the shared folders when the WAN link between branch office 2 and the main office is unavailable. When they attempt to access the files, they are prompted to enter their credentials but are denied access. You need to ensure that the users can access the shared folders if the WAN link fails. What should you do? A. Instruct a desktop support technician to configure Offline Files on the Windows 7 computers.
B. Instruct a desktop support technician to configure BranchCache on the Windows 7 computers.
C. Request that a domain administrator deploy a domain controller in branch office 2.
D. Request that a domain administrator enable Universal Group Membership Caching for branch office 2. Answer: B
Explanation:
You should use BranchCache in distributed mode and not offline files. Offline files are for single-user files and this question specifies it's a shared folder. Case Study 9 - Wingtip Toys (QUESTION 82 - QUESTION 86)
Scenario
You are an enterprise desktop support technician for Wingtip Toys. Wingtip Toys has two offices.
Active Directory Configuration
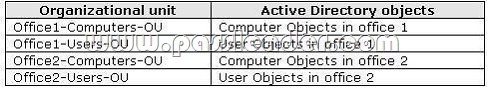
The network contains a single Active Directory domain. An Active Directory site exists for each office. The network contains the organizational units (OUs) that are shown in the following table:
The network contains an enterprise root certification authority (CA). Certificate autoenrollement is enabled for all users.
Network Configuration
Each office has a wireless network. You control access to the wireless network in office 1 by using Network Access Protection (NAP). A Group Policy object (GPO) named GPO1 configures the NAP settings for the computers in office 1.
Resource Access
The Documents folders of all users are encrypted by using Encrypting File System (EFS). The Documents folders of all users are backed up daily. A Web server named Web1 hosts an internal Web site named WebSite1. Users connect to WebSite1 from the Internet by using the URL http://website1.wingtiptoys.com. The domain name website1.wingtiptoys.com is resolved by using the hosts file that is located on each client computer. Users frequently work from home. Home users connect to the internal network by using SSTP- based VPN connections.
Line of Business Applications
Your company has a line-of-business application named App1. App1 is installed only on computers that run Windows XP. You test App1 by using the Microsoft Application Compatibility Toolkit (ACT). ACT reports that App1 can be made compatible to run on Windows 7. QUESTION 82
You deploy App1 on a test Windows 7 computer and notice that it fails to run. You need to ensure that App1 runs on Windows 7 computers. What should you do? A. Digitally sign App1.
B. Develop and deploy a shim for App1.
C. Configure an AppLocker policy.
D. Configure a Software Restriction Policy. Answer: B
Explanation:
http://www.youtube.com/watch?v=XgbjlrdkvUk
http://technet.microsoft.com/en-us/library/dd837645(v=ws.10).aspx QUESTION 83
The help desk reports that they receive many calls from remote users who cannot access Internet Web sites while they are connected to the VPN. The help desk instructs the users to manually configure the VPN connection so that the users can access Internet Web sites while connected to the VPN. You need to provide a recommendation to reduce the number of calls to the help desk regarding this issue. What should you recommend? A. Deploy a Network Policy Server (NPS).
B. Replace the SSTP-based VPN with a PPTP-based VPN.
C. Issue computer certificates from a trusted root certification authority (CA) to all remote users.
D. Create and distribute Connection Manager Administration Kit (CMAK) profiles to all remote users. Answer: D QUESTION 84
A group of users from office 2 travels to office 1 to work on a project. The users from office 2 report that they are unable to connect to the wireless network in office 1 from their portable computers. A help desk administrator manually provides the users with access to the wireless network. You need to ensure that the next time users from office 2 travel to office 1 they can connect to the wireless network in office 1. What should you request? A. Link GPO1 to Office2-Users-OU.
B. Link GPO1 to Office2-Computers-OU.
C. Change the office attribute for the user accounts.
D. Change the location attribute for the computer accounts. Answer: B QUESTION 85
A user's computer fails. The help desk provides the user with a new computer. The user's Documents folder is restored from the backup. The user reports that he can no longer access his encrypted files. The help desk recovers the files by using a data recovery agent (DRA). You need to ensure that when users receive new computers, they can access their encrypted files without administrative intervention. What should you request? A. credential roaming be enabled
B. BitLocker be enabled on all computers
C. user accounts be trusted for delegation
D. the CA be configured for key archival and recovery Answer: A
Explanation:
A. credential roaming be enabled. Credential roaming allows organizations to store certificates and private keys in Active Directory Domain Services (AD DS) separately from application state or configuration information. Credential roaming uses existing logon and auto enrollment mechanisms to securely download certificates and keys to a local computer whenever a user logs on and, if desired, remove them when the user logs off. In addition, the integrity of these credentials is maintained under any conditions, such as when certificates are updated and when users log on to more than one computer at a time.
C. user accounts be trusted for delegation. This security setting determines which users can set the Trusted for Delegation setting on a user or computer object. The user or object that is granted this privilege must have write access to the account control flags on the user or computer object. A server process running on a computer (or under a user context) that is trusted for delegation can access resources on another computer using delegated credentials of a client, as long as the client account does not have the Account cannot be delegated account control flag set. QUESTION 86
An administrator modifies the external IP address of Web1 and creates a Hosts (A) record for website1.wingtiptoys.com on the external DNS servers. Your users report that they can no longer connect to website1.wingtiptoys.com from the Internet. You need to ensure that users can connect to website1.wingtiptoys.com from the Internet. What should you do? A. Instruct the users to modify the DNS client settings on their computers.
B. Instruct the users to remove an entry from the Hosts file that is located on their computers.
C. Request that an administrator create a Pointer (PTR) resource record for the new IP address of Web1.
D. Request that an administrator create an alias (CNAME) resource record for website1.wingtiptoys.com. Answer: B Case Study 10 - Humongous Insurance (QUESTION 87 - QUESTION 89)
Scenario
You are an enterprise desktop support technician for Humongous Insurance.
Active Directory Configuration
The company has two offices named Office1 and Office2. The network contains an Active Directory forest named humongousinsurance.com. An Active Directory site exists for each office. The sites are named Site1 and Site2.
Server Configuration
All servers run Windows Server 2008 R2 and are joined to the domain. The relevant servers are configured as shown in the following table:
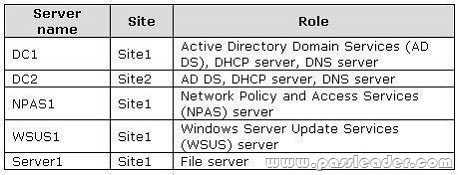
The corporate security policy states that all domain controllers must have only the following roles:
- AD DS
- DNS server
- DHCP server
Network Configuration
Site1 and Site2 connect to each other by using a WAN link.
Client Computer Configuration
All client computers run Windows 7 Enterprise and are members of the domain. Some client computers are portable computers and some are desktop computers. The computers do not support hardware virtualization. All computers are configured to receive Windows Updates from WSUS1.
Remote Access Configuration
Users can connect to NPAS1 from the Internet by using all of the VPN protocols that are supported by Windows Server 2008 R2. Fabrikam, Inc. is a customer of Humongous Insurance. Several Humongous Insurance users work at the Fabrikam office and access resources on the Humongous Insurance network by using direct VPN connections to NPAS1. Fabrikam contains several wireless access points.
Application Configuration
All computers in the finance department run a custom application suite named App1. Several users in the sales department install an application named App2. App2 runs as a service and logs on by using the credentials of the user who installed the application. QUESTION 87
Several users in the sales department report that their user accounts are locked out shortly after they change their user passwords. You need to minimize the number of account lockouts that occur after the users change their passwords. What should you instruct the users to do? A. Delete all entries from the Credential Manager vault.
B. Change their passwords and then create a password reset disk.
C. Change their passwords and then configure App2 to log on by using a service account.
D. Change their passwords and then log off and log back on to their computers. Answer: C QUESTION 88
Each day, 100 users in Office2 download a 5-MB product catalog file from a share on Server1. The network administrator reports that the downloads cause an excessive load on the WAN link between Office1 and Office2. You need to recommend a solution to minimize WAN utilization. The solution must not require that additional servers be deployed. What should you recommend? A. BranchCache in distributed cache mode
B. BranchCache in hosted cache mode
C. Distributed File System Replication (DFSR)
D. File Server Resource Management (FSRM) Answer: A QUESTION 89
Humongous Insurance users who work at Fabrikam report that when they move between different wireless networks, they are prompted to manually reconnect to the VPN. You need to ensure that the users can automatically reconnect to the VPN when they move between wireless networks. What should you request? A. that a network administrator create a CNAME record named AUTODISCOVER in the humongousinsurance.com DNS zone
B. that a network administrator enable Network Load Balancing on NPAS1
C. that users use only IKEv2-based VPN connections
D. that users use only SSTP-based VPN connections Answer: C Case Study 11 - Baldwin Museum of Science (QUESTION 90 - QUESTION 94)
Scenario
You are an enterprise desktop support technician for the Baldwin Museum of Science. The Baldwin Museum of Science is located in Dublin. The museum has 2,000 employees. All employees have laptop computers that have cellular connections. The museum has a main office and three satellite offices.
Active Directory Configuration
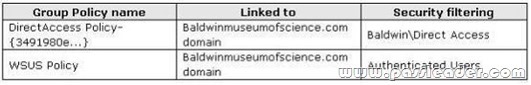
The network contains an Active Directory forest. The forest contains a domain named Baldwinmuseumofscience.com. The relevant group policy information is shown in the following table:
Server Configuration
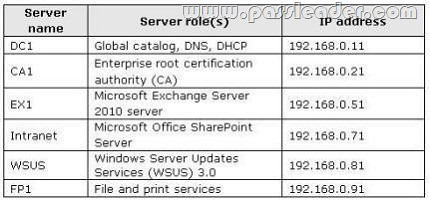
All servers are located in the main office and run Windows Server 2008 R2. The relevant servers are configured as shown in the following table:
Users access the network remotely by using a DirectAccess connection.
Client Computer Information
All client computers run Windows 7 Enterprise (x86). The client computers are configured to receive Windows Updates from http://WSUS.
Application Configuration
All users run Microsoft Office Outlook 2010 and use Outlook Anywhere. Users access the intranet Web site by using the URL http://intranet. The museum hosts several Web sites that use the domain suffix fineartschool.net.
Corporate Security Policy
The corporate security policy states that all updates on client computers must be installed from the internal WSUS server. QUESTION 90
Users report that they can only access the fineartschool.net Web servers by entering the full URL to the servers. You need to recommend a solution that allows users to access the Web servers by using single label names. Your solution must ensure that users can access the intranet Web server by using the URL http://intranet. What should you recommend? A. the DHCP server option for the DNS domain name be removed
B. fineartschool.net be added as the primary DNS suffix in the Default Domain Policy
C. fineartschool.net be added to the DNS Search Suffix list in the Default Domain Policy
D. the Allow DNS Suffix Appending to unqualified Multi-Label Name Queries setting be enabled in the Default Domain Policy Answer: C

http://www.passleader.com/70-685.html
|











