[Pass Ensure VCE Dumps] Download Free PassLeader Premium 196q 70-685 Exam Questions (131-150)
Pass 70-685 exam easily by learning PassLeader 70-685 exam dumps! PassLeader just updated the 196q 70-685 exam questions, the new 70-685 VCE or PDF practice tests cover all the real questions, which will help you passing 70-685 exam easily. What's more, PassLeader's new 70-685 VCE dumps and PDF dumps have corrected many wrong answers, which is not available in other free 70-685 VCE dumps, it will ensure you 100 percent passing 70-685 exam! keywords: 70-685 exam,196q 70-685 exam dumps,196q 70-685 exam questions,70-685 pdf dumps,70-685 vce dumps,70-685 practice test,70-685 study guide,Pro: Windows 7, Enterprise Desktop Support Technician Exam 
QUESTION 131
A corporate environment includes client computers running Windows 7 Enterprise. Users are unable to start Windows Internet Explorer after several new ActiveX controls are deployed to their client computers. You need to recommend an approach for determining whether the issue is caused by the ActiveX controls. What is the best approach to achieve the goal? (More than one answer choice may achieve the goal. Select the BEST answer.) A. Start Internet Explorer in InPrivate Browsing mode.
B. Restart each client computer and select the Safe Mode startup option.
C. Start Internet Explorer in No Add-ons mode.
D. Restart each client computer and select the Last Known Good Configuration startup option. QUESTION 132
A corporate environment includes client computers running Windows 7 Enterprise. The client computers are joined to an Active Directory Domain Services (AD DS) domain named contoso.com. Employees frequently access secure websites that are subsites of an external domain named fabrikam.com. Pop-up windows from the fabrikam.com subsites are being blocked. You need to recommend an approach for ensuring that the pop-up windows from the fabrikam.com subsites are allowed. What is the best approach to achieve the goal? (More than one answer choice may achieve the goal. Select the BEST answer.) A. Add *.fabrikam.com to the Local Intranet zone in Internet Explorer on each client computer.
B. Add *.fabrikam.com to the Trusted Sites zone in Internet Explorer on each client computer.
C. Set the Pop-up Blocker Blocking Level to Low on each client computer.
D. Disable the Pop-up Blocker on each client computer. Answer: B QUESTION 133
A corporate environment includes client computers running Windows 7 Enterprise. The client computers are joined to an Active Directory Domain Services (AD DS) domain. A member server named SERVER01 hosts shared folders and a website. DNS is the primary name-resolution protocol in use. There have been no recent changes to the DNS entries. The user of a client computer named PC01 can access the shared folders, but cannot access the website by using Windows Internet Explorer. Users of other client computers can access the shared folders and the website. You need to recommend an approach for ensuring that the user can access the website from PC01. What is the best approach to achieve the goal? (More than one answer choice may achieve the goal. Select the BEST answer.) A. Clear the proxy server setting from Internet Explorer on PC01.
B. Run the ipconfig /registerdns command from SERVER01.
C. Run the ipconfig /flushdns command from PC01.
D. Restart the World Wide Web Publishing service on SERVER01. Answer: C QUESTION 134
A corporate environment includes 10,000 client computers running Windows 7 Enterprise. The client computers are joined to an Active Directory Domain Services (AD DS) domain named contoso.com. DNS is the preferred name-resolution protocol. There have been no recent changes to the DNS entries. WINS is not running in the environment. When most users attempt to connect to pc01.contoso.com from their client computers, the URL resolves to the incorrect IP address. The URL resolves correctly from only one client computer. On the client computers experiencing the issue, the HOSTS file does not include an entry for pc01.contoso.com. You need to recommend an approach for resolving pc01.contoso.com correctly from all client computers. What is the best approach to achieve the goal? (More than one answer choice may achieve the goal. Select the BEST answer.) A. Run the ipconfig /flushdns command from the client computers experiencing the issue.
B. Add a pc01 entry pointing to the correct IP address to the LMHOSTS file on each of the client computers experiencing the issue.
C. Add a pc01.contoso.com entry pointing to the correct IP address to the HOSTS file on each of the client computers experiencing the issue.
D. Run the ipconfig /registerdns command from PC01. Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/cc784552(WS.10).aspx QUESTION 135
You have a development network that you use for testing purposes. The development network contains an Active Directory domain. Users have computers that run Windows 7. The users have several virtual machines that run Windows 7. The virtual machines are joined to Active Directory. Several users report that when they discard changes on the virtual machines, and then attempt to log on to the machines, they sometimes receive the following error message:
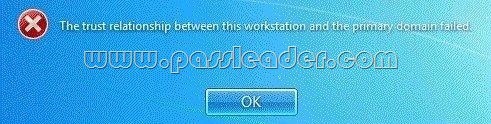
You need to prevent this error from recurring. What should you do? A. Create a Password Setting object (PSO) in Active Directory.
B. Modify the security settings by using a Group Policy object (GPO).
C. On the virtual machines, create a password reset disk.
D. On the virtual machines, modify the User Account Control (UAC) settings. Answer: B QUESTION 136
You are troubleshooting recurring performance issues on a Windows 7 client computer. Each time a performance issue occurs, an associated event log entry is written to the Application event log. You need to recommend ways to query the Application event log from the command line. Which commands should you recommend? (Choose all that apply.) A. wevtutil qe application / rd:true / f:text
B. eventvwr / happlication.evtx
C. wevtutil gl application
D. Get-Event - Eventldentifier =2
E. eventvwr \localhost
F. Get- WmiObject Win32_NTLogEvent -filter- LogFile 'Application'" Answer: AEF QUESTION 137
A Windows 7 client computer named PCO1 has intermittent performance issues. Each time a performance issue occurs, an associated event log entry is written to the Application event log. You need to ensure that a Windows 7 administrative computer named PC02 receives the event log entries from PCO1. What should you do? (Choose all that apply.) A. Run the winrmquickconfig command on PCO1 and PC02. Run the wecutil qc command on PC02.
B. Run the winrmquickconfig command on PCO1 only. Run the wecutil qc command on PC02.
C. Add the PC02 computer account to the local Administrators group on PCO1.
D. Create a new event subscription on PCO1.
E. Create a new event subscription on PC02.
F. Add the PCO1 computer account to the local Administrators group on PC02. Answer: BCE QUESTION 138
All client computers on your company network run Windows 7 and are members of an Active Directory Domain Services (AD DS) domain. A network administrator changes the IP address of a file server. Employees are unable to connect to the file server. You need to ensure that the employees are able to connect to the file server immediately. Which command should you instruct the employees to run? A. ipconfig /showdns
B. ipconfig /registerdns
C. ipconfig /flushdns
D. Ipconfig /renew Answer: C QUESTION 139
A company has computers that run Windows 7 Enterprise. A user's computer has been crashing and showing error messages over the past several days. You need to gather historical information about the errors. Which tools should you use? (Choose all that apply.) A. Troubleshooting in Control Panel
B. Performance Monitor
C. Disk Defragmenter
D. Event Viewer
E. Reliability Monitor Answer: DE QUESTION 140
A company has computers running the 64-bit version of Windows 7 Enterprise. All computers are joined to an Active Directory Domain Services (AD DS) domain. All users are part of the local Administrators group. A user is trying to install a legacy 32-bit application that requires administrative permissions to install. The user reports that the inst.exe installer does not run. Instead, it shows an "access denied" error message and closes. The user does not see a prompt to grant the application permission to make changes to the computer. You need to ensure that inst.exeruns successfully and can install the application. What should you do? (Choose all that apply.) A. Run Disk Defragmenteron the hard disk and then run inst.exe.
B. Modify the properties for inst.exeto run as Administrator.
C. Run the Troubleshoot compatibility wizard for inst.exe.
D. Enable the Administrator account, log on, and then run inst.exe.
E. Advise the user that inst.exe cannot be installed on this system because it is not compatible with 64-bit operating systems.
F. Advise the user that inst.exe cannot be installed on this system because it is not compatible with Windows 7. Answer: BCD
Explanation:
http://www.sevenforums.com/tutorials/316-compatibility-mode.html

http://www.passleader.com/70-685.html QUESTION 141
A company has a main office and a branch office. The network contains a single Active Directory domain. All computers are members of the domain. Five users in the branch office report that their Windows 7 computer is slow when it runs multiple applications. From your computer, you need to identify the application that consumes the most processor resources on the computers. Which tool should you use? A. Event Viewer
B. Performance Monitor
C. CPU Meter gadget
D. Task Manager Answer: B
Explanation:
http://www.youtube.com/watch?v=1S9wLElymz8 QUESTION 142
A company has new portable computers running Windows 7. On one of the computers, the USB mouse cursor does not move. You connect the mouse to another computer, where it works correctly. You need to recommend possible solutions to the problem. What should you recommend? (Choose all that apply.) A. Connect the mouse into a different USB port.
B. Enable the USB controller in the BIOS.
C. Disable the computer's trackpad.
D. Disable Hot Keys on the computer.
E. Turn on Mouse Keys. Answer: ABC QUESTION 143
You are troubleshooting performance issues on a Windows 7 Enterprise client computer. An unfamiliar service is running on the computer. You need to recommend the solutions that identify which process identifier (PID) is associated with the service. What should you do? (Choose all that apply.) A. Pun the System Configuration utility (rnsconfig.exe) and view the Services tab.
B. Run the sc query command.
C. Use Windows Task Manager and view the Services tab.
D. Run the sc queryex command.
E. Run the Services management console. Answer: CD
Explanation:
http://technet.microsoft.com/en-us/library/dd228921(WS.10).aspx
In order to get to know, or view, retrieve and identify the process ID or PID of the processes running in Windows operating system, users or administrators can make use of Task Manager. However, Task Manager does not display PID information by default. To display the PID value in Task Manager, go to Processes tab, click on View menu, and then click on Select Columns...In the "Select Columns" or "Select Process Page Columns" dialog, tick and check the checkbox for PID (Process Identifier), and click OK. QUESTION 144
A company has computers running Windows 7 Enterprise. Connections to the company's wireless network are filtered by MAC address. The company purchases a new computer that must be connected to the wireless network. You need to recommend all the commands that discover the MAC address of the new computer's wireless network adapter. Which commands should you recommend? (Choose all that apply.) A. getmac /v
B. ipconfig /all
C. netstat
D. ipconfig
E. ipconfig / allcompartments Answer: AB
Explanation:
http://technet.microsoft.com/en-us/library/bb490913.aspx QUESTION 145
Existing Internet Explorer security settings and GPOs are applied throughout the company. However, users are visiting websites known by Internet Explorer to host malicious content. You need to ensure that users cannot visit those websites. Which setting in the GPO should you enable to achieve this goal? A. Turn off Managing SmartScreen Filter for Internet Explorer 8
B. Prevent Bypassing SmartScreen Filter Warnings
C. Turn on ActiveX Filtering
D. Prevent ignoring certificate errors
E. Turn off Managing Phishing filter Answer: B QUESTION 146
Existing Internet Explorer security settings and GPOs are applied throughout the company. However, users are visiting websites known by Internet Explorer to host malicious content. You need to ensure that users cannot visit those websites. Which setting in the GPO should you enable to achieve this goal? A. Turn off Managing SmartScreen Filter for Internet Explorer 8
B. Prevent Bypassing SmartScreen Filter Warnings
C. Turn on ActiveX Filtering
D. Prevent ignoring certificate errors
E. Turn off Managing Phishing filter Answer: B QUESTION 147
Drag and Drop Question
A company has computers that run Windows 7 Enterprise. A 500-GB hard disk has a single volume and 450-GB of free space. You attempt to reduce the size of the volume but the operation fails due to physical disk errors on the hard disk. You need to ensure the computer has a hard disk without physical disk errors and containing all existing data. Which two actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
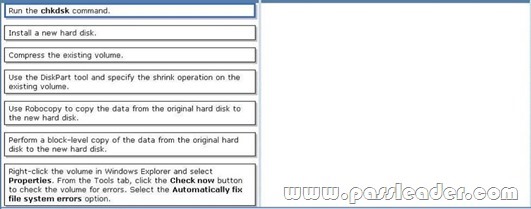 Answer:
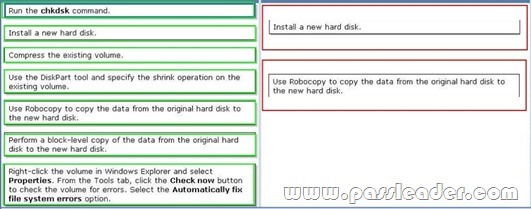 QUESTION 148
You install an application on one of the company's test computers. The application fails to run and is affecting other applications. You are unable to uninstall the application successfully. You need to remove the application from the test computer without modifying user documents. What should you do? A. Restart the test computer by using in Last Known good Configuration
B. Use Windows Backup to restore the test computer
C. Use System Restore to restore the test computer
D. Restart the test computer in Safe Mode Answer: C QUESTION 149
One of the company's client computers is configured with the company's System Protection settings. That computer becomes unresponsive. You run a system restore on the computer. The system restore does not restore the computer system settings. You need to ensure that all future system restores for the computer include system settings. You reimage the client computer with the company's corporate image. What should you do next? A. Modify the System Protection properties for the C volume
B. Create a new system restore point
C. Modify the Shadow Copies properties for the C volume
D. Create a new critical volume backup Answer: A QUESTION 150
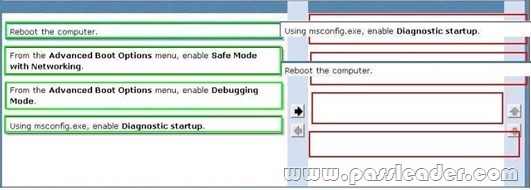
Drag and Drop Question
You install an application named App01 on a client computer running Windows 7. The application automatically appears in the system tray. Upon reboot, the application consumes all of the computer's network bandwidth. You need to stop the application from consuming the bandwidth so that you can troubleshoot the problem. Which two actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
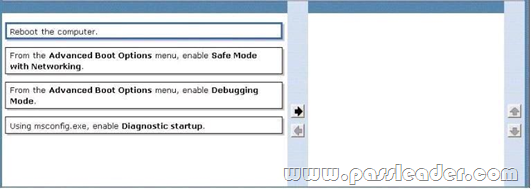 Answer:

http://www.passleader.com/70-685.html
|





