(New Updated) Download Free Cisco 350-018 617q Study Materials With New Added Exam Questions (31-60)
What's the secret of easily passing new 350-018 exam? PassLeader have been updated the 350-018 617q exam dumps with the newest exam questions. We offer the latest 350-018 617q PDF dumps and VCE dumps with New Version VCE Player for free download to ensure your 350-018 exam pass. Now visit www.passleader.com and get the 100 percent pass ensure 350-018 617q braindump! keywords: 350-018 exam,350-018 exam dumps,350-018 617q exam questions,350-018 617q pdf dumps,350-018 vce dumps,350-018 617q braindump,CCIE Security Written Exam, v4.0 
NEW QUESTION 31
Refer to the exhibit. What is the most likely reason for the error?
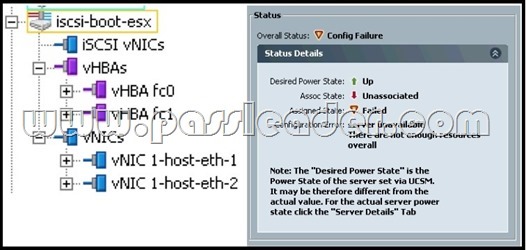 A. There are not enough local hard drives to satisfy the local disk configuration policy.
B. One of the resource pools is depleted (WWN, MAC, UUID).
C. The destination blade is equipped with an M61KR-B adapter.
D. The server is not equipped with adequate memory.
E. A User Ack maintenance policy has been applied. Answer: C NEW QUESTION 32
Refer to the exhibit. How many additional chassis equipped with Cisco UCS 2204XP I/O Modules could be connected at maximum bandwidth without exceeding the existing port licenses?
 A. 1
B. 2
C. 3
D. 4
E. 5 Answer: B NEW QUESTION 33
Refer to the exhibit. Assume that there is no disjoint Layer 2 configuration. Based on the output, what will happen if uplink eth1/7 on FI-A fails?
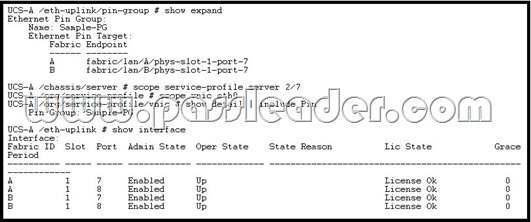 A. The host will lose Ethernet uplink connectivity on FI-A.
B. Fabric failover will force the vNIC that is bound to FI-A to use uplink eth1/7 on FI-B.
C. Cisco UCS Manager will disable the host vNIC that is connected to FI-A.
D. Traffic from any hosts using this pin group will use e1/8 on FI-A. Answer: D NEW QUESTION 34
Refer to the exhibit. You are setting up a service profile to iSCSI boot using a Cisco UCS VIC 1240. The service profile returns a configuration error when you attempt to associate it. What is the problem, based on the exhibit?
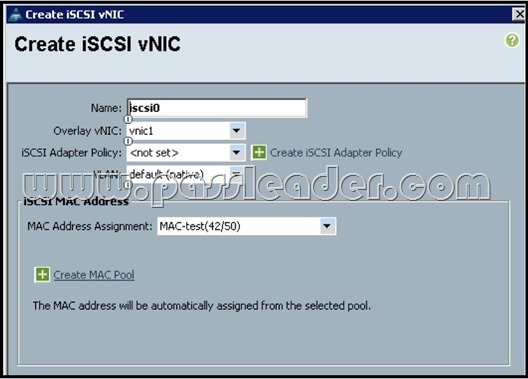 A. The iSCSI adapter policy is not set.
B. iSCSI boot will not work with the default VLAN.
C. The default VLAN should not be set as native on the overlay vNIC.
D. The MAC address assignment is invalid. Answer: D NEW QUESTION 35
You plan to add a new VLAN to your updating service profile template. Assuming that the default maintenance policy is configured, which statement about applying this change is true? A. The change will be applied immediately once the blade is rebooted.
B. The change will be deferred until the user acknowledges.
C. The change will be applied immediately with no disruption to any bound service profiles.
D. The change will generate an impact summary message.
E. The change will require all bound service profiles to be unbound. Answer: C NEW QUESTION 36
You have configured a Cisco UCS C460 M2 Rack-Mount Server with two VIC 1225 adapters for single-wire management with Cisco UCS Manager. Which statement correctly describes the operation of these adapters? A. One VIC is designated to carry management, and the other VIC is designated to carry data traffic.
B. Both VICs will be used for management and data traffic.
C. One VIC will carry management, and both VICs will carry data traffic.
D. The Cisco UCS C460 M2 does not support two VIC 1225 adapters simultaneously. Answer: C NEW QUESTION 37
Which two items have an impact on the maximum number of virtual interfaces that can be created on a virtual interface card? (Choose two.) A. Number of blades in the chassis
B. Number of acknowledged links between the Fabric Interconnect and the I/O module
C. Number of connected uplinks
D. Number of Fabric Interconnect port ASICs used by uplinks
E. Number of Fabric Interconnects
F. Number of VIC Answer: BD NEW QUESTION 38
What is the purpose of the management interface monitoring policy? A. to monitor the management interface counters for errors and drops
B. to prevent VM traffic from being black-holed during a cluster switchover
C. to sync MAC address tables between peer fabric interconnects
D. to ensure that the management interface of the managing fabric interconnect can reach the gateway Answer: D NEW QUESTION 39
How are unified port expansion modules for Cisco UCS 6200 Series Fabric Interconnects licensed? A. All ports are fully licensed by default.
B. The first eight ports on the module are licensed by default.
C. The expansion modules contribute eight licenses to the global pool by default.
D. The expansion modules contribute six licenses to the global pool by default.
E. The first six ports on the module are licensed by default. Answer: D NEW QUESTION 40
Refer to the exhibit. In the figure, the load balancer acts a transparent TCP proxy, and establishes the connection with the client on behalf of the real server. What is this type of spoofing called?
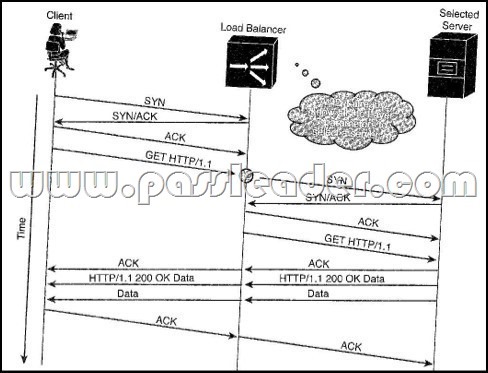 A. Delayed binding
B. Software-based load balancing
C. Transport proxy
D. Application binding Answer: A NEW QUESTION 41
A load balancer performs an operation on a predefined parameter, such as the IP address, HTTP cookie, or URL, when a new connection is made so that another connection with the same parameter will always reach the same server. Which load-balancing predictor does this statement describe? A. Round robin
B. Least-connections
C. Hashing
D. Least-loaded Answer: C NEW QUESTION 42
What are the three benefits of SSL offload? (Choose three.) A. Total offload of encryption from the servers
B. Partial offload of encryption from the servers
C. Layer 5 to 7 awareness for Layer 7 switching
D. Layer 5 to 7 awareness for Layer 5 to 7 switching
E. Public certificates required on both load balancer and the real server
F. Public certificate required only on load balancer Answer: ACF NEW QUESTION 43
Refer to the exhibit. Which type of SSL offload configuration is shown in the output?
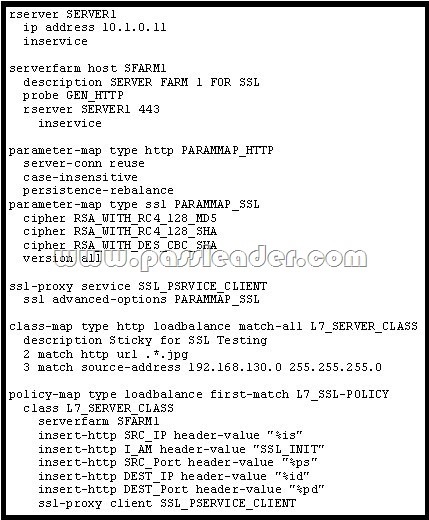 A. SSL termination
B. SSL initiation
C. End-to-end SSL
D. SSL testing Answer: B NEW QUESTION 44
In the basic DNS resolution process, which component receives the query and sends it to the location that knows the IP address for the destination? A. DNS resolver
B. D-proxy
C. Root server
D. Intermediate server
E. Authoritative server Answer: B NEW QUESTION 45
Which four options describe benefits of the global load-balancing solution? (Choose four.) A. Device status within the data center
B. Performance granularity
C. Centralized client access
D. Intelligent traffic management
E. Reacts quickly for availability only
F. Server monitoring statistics
G. Round robin support only for load-balancing Answer: ABDF

http://www.passleader.com/350-018.html NEW QUESTION 46
Which two statements about dynamic port binding are true? (Choose two.) A. The port is connected when the VM is powered on and disconnected when the VM is powered off.
B. The port is created when the VM is powered on and destroyed when the VM is powered off.
C. The max-port limits are enforced.
D. The max-port limits are not enforced.
E. The port is always connected. Answer: AC NEW QUESTION 47
Which two methods can be used in communications between the Cisco Nexus 1000V VEM and the VSM? (Choose two.) A. Routed TCP traffic using HTTPS
B. Routed UDP traffic using port 4785
C. Routed UDP traffic using port 7845
D. Layer 2 direct traffic using MAC addresses
E. Layer 2 broadcast traffic
F. Routed TCP traffic using port 4785
G. Routed TCP traffic using port 7845 Answer: BD NEW QUESTION 48
Refer to the exhibit. An administrator is setting up the VSM and VEM in Layer 3 mode. The administrator adds a host to the distributed switch in VMware, but does not see the module join the VSM. Given the configuration in the exhibit, which three configuration items must be included in the configuration? (Choose three.)
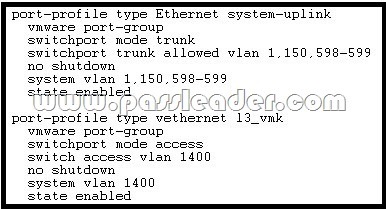 A. The vEthernet Port Profile parameter must be set to Capability I3control.
B. The vEthernet Port Profile parameter must be set to VSM l3control.
C. The Ethernet Port Profile parameter must be set to System VLAN 1400.
D. The Ethernet Port Profile parameter must be set to VLAN 1400 in the allowed trunk.
E. The Ethernet Port Profile parameter must be set to Capability l3control.
F. The vEthernet Port Profile parameter must be set to Mode Trunk.
G. The vEthernet Port Profile parameter must be set to VEM l3control. Answer: ACD NEW QUESTION 49
Which of the following is an advanced networking function performed by VEM? A. QoS
B. Snooping
C. VSAN creation
D. VLAN pruning Answer: A NEW QUESTION 50
Refer to the exhibit. The network administrator is adding a new Cisco Nexus 1000V Switch to vCenter, but does not see the new switch under the vCenter networking tab. Which option describes the most correct cause of this error?
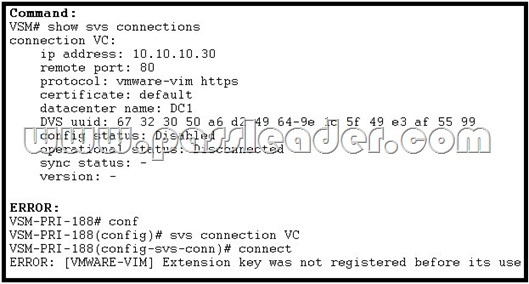 A. There is a missing control VLAN in the VSM configuration.
B. There is a missing packet VLAN in the VSM configuration.
C. VSM has no network connection to vCenter.
D. The VSM extension key is not installed on vCenter.
E. The vCenter extension key is not installed on VSM. Answer: D NEW QUESTION 51
Which statement about FabricPath is correct? A. In FabricPath, FTag is the 10-bit field in FabricPath encapsulation that identifies the topology or distribution tree.
B. In FabricPath, FTag is the 8-bit field in FabricPath encapsulation that identifies the topology or distribution tree.
C. In FabricPath, the FTag is the 16-bit field in FabricPath encapsulation that identifies the topology or distribution tree.
D. In FabricPath, the FTag is the 32-bit field in FabricPath encapsulation that identifies the topology or distribution tree. Answer: A NEW QUESTION 52
Which two options describe devices as they operate in FabricPath topologies? (Choose two.) A. Edge (or leaf) devices: These devices have ports that are connected to classic Ethernet devices (servers, firewalls, router ports, and so on) and ports that are connected to the FabricPath cloud (or FabricPath ports). Edge devices are able to map a MAC address to the destination switch ID.
B. Spine devices: These devices exclusively interconnect edge devices. Spine devices switch exclusively based on the destination switch ID.
C. Edge (or leaf) devices: These devices have ports that are connected to classic Ethernet devices (servers, firewalls, router ports, and so on) and ports that are connected to the FabricPath cloud (or FabricPath ports). Edge devices are able to map a source address to the destination switch ID.
D. Spine devices: These devices exclusively interconnect edge devices. Spine devices switch exclusively based on the source switch ID. Answer: AB NEW QUESTION 53
What are the two FEX connection modes? (Choose two.) A. Hard-pinning mode
B. Soft-pinning mode
C. Port channel mode
D. Physical-pinning mode
E. Clan pinning mode Answer: AC NEW QUESTION 54
How many licenses are provided with the purchase of the Cisco UCS 6296 fabric interconnect? A. 18
B. 16
C. 12
D. 8 Answer: A NEW QUESTION 55
What is the default burst in a LAN QoS policy? A. 10240
B. 9216
C. 20480
D. 1548 Answer: A NEW QUESTION 56
Which feature must be enabled on the upstream Fibre Channel switch if the fabric interconnect is configured in end-host mode? A. NPV
B. NPIV
C. Zoning
D. Smart Zoning Answer: B NEW QUESTION 57
Fault suppression allows you to suppress SNMP trap and Call Home notifications during a planned maintenance period. Which three commands are necessary to activate these suppression polices in Cisco UCS Manager? (Choose three.) A. Default-chassis-all-maint
B. Default-chassis-phys-maint
C. Default-fex-all-maint
D. Default-FI-phys-maint
E. Default-blade-phys-maint
F. Default-vic-phys-maint Answer: ABC NEW QUESTION 58
How many traffic monitoring sessions can you create on Cisco UCS Manager? A. 16
B. 8
C. 24
D. 32 Answer: A NEW QUESTION 59
Refer to the exhibit. Which statement about the interface that is connected to the NPV core switch is true?
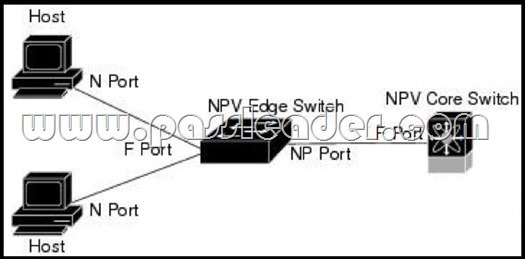 A. The switch that connects to the hosts is identified in the design as an NPV edge switch, and the port that connects to the core is an NP port.
B. The interface that is connected to the NPV switch will need to be configured as an N-Port.
C. The interface that is connected to the NPV core will become an FP port.
D. The link between the NPV core switch and edge will come up as an E port. Answer: A NEW QUESTION 60
When an NP port becomes operational, the NP switch first logs itself into the core switch by sending a FLOGI request (using the port WWN of the NP port). What will occur next? A. The switch registers with the fabric name server.
B. The switch will perform a PLOGI to the port login server.
C. The switch will register parameters using FDISC.
D. The NPV switch will perform a PLOGI using FDISC to register with the fabric name server. Answer: A

http://www.passleader.com/350-018.html
|









