[New Exam Dumps] First Try Free PassLeader 70-414 Exam Dumps and First Pass 70-414 Exam
New Updated 70-414 Exam Questions from PassLeader 70-414 pdf dumps! Welcome to download the newest PassLeader 70-414 vce dumps: http://www.passleader.com/70-414.html (229 Q&As) Keywords: 70-414 exam dumps, 70-414 exam questions, 70-414 vce dumps, 70-414 pdf dumps, 70-414 practice test, 70-414 study guide, Implementing an Advanced Server Infrastructure Exam Case Study 7: Contoso Ltd Case D (NEW QUESTION 212 - NEW QUESTION 225)
Overview
Contoso, Ltd., is a manufacturing company that makes several different components that are used in automobile production. Contoso has a main office in Detroit, a distribution center in Chicago, and branch offices in Dallas, Atlanta, and San Diego. The contoso.com forest and domain functional level are Windows Server 2008 R2. All servers run Windows Server 2012 R2, and all client workstations run Windows 7 or Windows 8. Contoso uses System Center 2012 Operations Manager and Audit Collection Services (ACS) to monitor the environment. There is no certification authority (CA) in the environment.
Current Environment
The contoso.com domain contains the servers as shown in the following table:
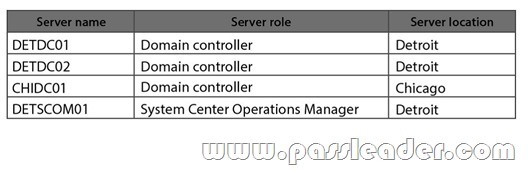 Contoso sales staff travel within the United States and connect to a VPN by using mobile devices to access the corporate network. Sales users authenticate to the VPN by using their Active Directory usernames and passwords. The VPN solution also supports certification-based authentication. Contoso uses an inventory system that requires manually counting products and entering that count into a database. Contoso purchases new inventory software that supports wireless handheld scanners and several wireless handheld scanners. The wireless handheld scanners run a third party operating system that supports the Network Device Enrollment Service (NDES). Business Requirements Security The wireless handheld scanners must use certification-based authentication to access the wireless network. Sales users who use mobile devices must use certification-based authentication to access the VPN. When sales users leave the company, Contoso administrators must be able to disable their VPN access by revoking their certificates. Monitoring All servers must be monitored by using System Center 2012 Operating Manager. In addition to monitoring the Windows operating system, you must collect security logs from the CA servers by using ACS, and monitor the services that run on the CA and Certificate Revocation List (CRL) servers, such as certification authority and web services. Technical Requirements CA Hierarchy Contoso requires a two-tier CA hierarchy. The CA hierarchy must include a stand-alone offline root and two Active Directory-integrated issuing CAs: one for issuing certificates to domain-joined devices, and one for issuing certificates to non-domain-joined devices by using the NDES. CRLs must be published to two web servers: one in Detroit and one in Chicago. Contoso has servers that run Windows Server 2012 R2 to use for the CA hierarchy. The servers are described in the following table: 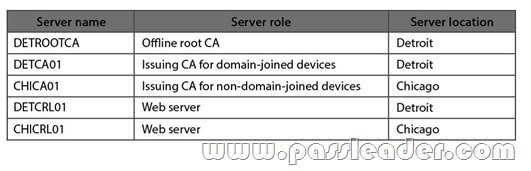 The IT security department must have the necessary permissions to manage the CA and CRL servers. A domain group named Corp-IT Security must be used for this purpose. The IT security department users are not domain admins. Fault Tolerance The servers that host the CRL must be part of a Windows Network Load Balancing (NLB) cluster. The CRL must be available to users in all locations by using the hostname crl.contoso.com, even if one of the underlying web servers is offline. NEW QUESTION 212
You need to automatically restart the appropriate web service on DETCRL01 and CHICRL01 if the web service is stopped. Solution: You create a recovery task in SCOM and configure it to start the World Wide Web publishing service. Does this meet the goal? A. Yes
B. No Answer: A
Explanation:
The Internet Information Services (IIS) World Wide Web Publishing Service (W3SVC), sometimes referred to as the WWW Service, manages the HTTP protocol and HTTP performance counters. The following is a list of the managed entities that are included in this managed entity:
* IIS Web Site. An Internet Information Services (IIS) Web site is a unique collection of Web pages and Web applications that is hosted on an IIS Web server. Web sites have bindings that consist of a port number, an IP address, and an optional host name or names.
* Active Server Pages (ASP)
https://technet.microsoft.com/en-us/library/cc734944(v=ws.10).aspx NEW QUESTION 213
You plan to allow users to run internal applications from outside the company's network.
You have a Windows Server 2012 R2 that has the Active Directory Federation Services (AD FS) role installed. You must secure on-premises resources by using multi-factor authentication (MFA). You need to design a solution to enforce different access levels for users with personal Windows 8.1 or iOS 8 devices.
Solution: You install a local instance of MFA Server. You connect the instance to the Microsoft Azure MFA provider, and then run the following Windows PowerShell cmdlet:
Enable-AdfsDeviceRegistration
Does this meet the goal? A. Yes
B. No Answer: B
Explanation:
We must install AD FS Adapter, not register a host for the Device Registration Service. Note: The Enable-AdfsDeviceRegistration cmdlet configures a server in an Active Directory Federation Services (AD FS) farm to host the Device Registration Service.
https://msdn.microsoft.com/en-us/library/azure/dn807157.aspx NEW QUESTION 214
An organization uses an Active Directory Rights Management Services (AD RMS) cluster named RMS1 to protect content for a project. You uninstall AD RMS when the project is complete. You need to ensure that the protected content is still available after AD RMS is uninstalled.
Solution: You enable the decommissioning service by using the AD RMS management console. You grant all users the Read & Execute permission to the decommission pipeline.
Does this meet the goal? A. Yes
B. No Answer: B
Explanation:
The proper procedure is: Inform your users that you are decommissioning the AD RMS installation and advise them to connect to the cluster to save their content without AD RMS protection. Alternatively, you could delegate a trusted person to decrypt all rights- protected content by temporarily adding that person to the AD RMS super users group. After you believe that all of the content is unprotected and saved, you should export the server licensor certificate, and then uninstall AD RMS from the server. NEW QUESTION 215
Your network contains an Active Directory domain named contoso.com. Your company has an enterprise root certification authority (CA) named CA1. You plan to deploy Active Directory Federation Services (AD FS) to a server named Server1. The company purchases a Microsoft Office 365 subscription. You plan to register the company's SMTP domain for Office 365 and to configure single sign-on for all users. You need to identify which certificate is required for the planned deployment. Which certificate should you identify? A. a server authentication certificate that is issued by a trusted third-party root CA and that contains the subject name serverl.contoso.com
B. a self-signed server authentication certificate for server1.contoso.com
C. a server authentication certificate that is issued by a trusted third-party root CA and that contains the subject name Server1
D. a server authentication certificate that is issued by CA1 and that contains the subject name Server1 Answer: A
Explanation:
Prepare Your Server and Install ADFS You can install ADFS on a domain controller or another server. You'll first need to configure a few prerequisites. The following steps assume you're installing to Windows Server 2008 R2.
Using Server Manager, install the IIS role and the Microsoft .NET Framework. Then purchase and install a server-authentication certificate from a public certificate authority. Make sure you match the certificate's subject name with the Fully Qualified Domain Name of the server.
Launch IIS Manager and import that certificate to the default Web site.
https://technet.microsoft.com/en-us/magazine/jj631606.aspx NEW QUESTION 216
You administer an Active Directory Domain Services environment. There are no certification authorities (CAs) in the environment. You plan to implement a two-tier CA hierarchy with an offline root CA. You need to ensure that the issuing CA is not used to create additional subordinate CAs. What should you do? A. In the CAPolicy.inf file for the issuing CA, enter the following constraint:
PathLength=1
B. In the CAPolicy.inf file for the root CA, enter the following constraint:
PathLength=1
C. In the CAPolicy.inf file for the root CA, enter the following constraint:
PathLength=2
D. In the CAPolicy.inf file for the issuing CA, enter the following constraint:
PathLength=2 Answer: B
Explanation:
You can use the CAPolicy.inf file to define the PathLength constraint in the Basic Constraints extension of the root CA certificate. Setting the PathLength basic constraint allows you to limit the path length of the CA hierarchy by specifying how many tiers of subordinate CAs can exist beneath the root. A PathLength of 1 means there can be at most one tier of CAs beneath the root. These subordinate CAs will have a PathLength basic constraint of 0, which means that they cannot issue any subordinate CA certificates.
http://blogs.technet.com/b/askds/archive/2009/10/15/windows-server-2008-r2-capolicy-inf-syntax.aspx NEW QUESTION 217
You have a small Hyper-V cluster built on two hosts that run Windows Server 2012 R2 Hyper-V. You manage the virtual infrastructure by using System Center Virtual Machine Manager 2012. Distributed Key Management is not installed. You have the following servers in the environment:
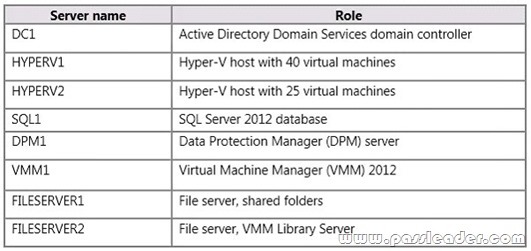
You have the following requirements:
- You must back up virtual machines at the host level.
- You must be able to back up virtual machines that are configured for live migration.
- You must be able to restore the entire VMM infrastructure.
You need to design and implement the backup plan. What should you do? A. Run the following Windows PowerShell command:
Get-VM VMM1 | Checkpoint-VM-SnapshotName "VMM backup"
B. Run the following Windows PowerShell command:
Set-DPMGlobalProperty-DPMServerName DPM1-KnownVMMServers VMM1
C. Configure System State Backup for DCL.
D. Configure backup for all disk volumes on FILESERVER1 Answer: B
Explanation:
DPM can protect Hyper-V virtual machines V during live migration.
Connect servers--Run the the Set-DPMGlobalProperty PowerShell command to connect all the servers that are running Hyper-V to all the DPM servers.
The cmdlet accepts multiple DPM server names.
Set-DPMGlobalProperty -dpmservername <dpmservername> -knownvmmservers <vmmservername>
https://technet.microsoft.com/en-us/library/jj656643.aspx NEW QUESTION 218
You need to deploy the new SQL Server virtual machines. What should you do? A. On Chi-Primary, configure placement rules for the specified nodes.
B. On the specified cluster nodes in the primary data center in Chicago, run the following Windows PowerShell command: Set-SCVMHost -AvaliableForPlacement
C. On the specified cluster nodes in the primary data center in Chicago, select the Host is available for placement check box.
D. On Sea-Primary, configure placement rules for the specified nodes.
E. Both the Assertion and the Reason are false. Answer: B
Download the newest PassLeader 70-414 exam questions from PassLeader now! 100% Pass Guarantee! 70-414 pdf dumps & 70-414 vce dumps: http://www.passleader.com/70-414.html (229 Q&As)
|


