[Free-Dumps] Do Not Miss 400-251 Exam Dumps Shared By PassLeader -- 100% Exam Pass Guarantee (Question 181 – Question 210)
New Updated 400-251 Exam Questions from PassLeader 400-251 PDF dumps! Welcome to download the newest PassLeader 400-251 VCE dumps: http://www.passleader.com/400-251.html (366 Q&As) Keywords: 400-251 exam dumps, 400-251 exam questions, 400-251 VCE dumps, 400-251 PDF dumps, 400-251 practice tests, 400-251 study guide, 400-251 braindumps, CCIE Security Exam p.s. Free 400-251 dumps download from Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpd3JLalNVS0VWbms QUESTION 181
What are two advantages of NBAR2 over NBAR? (Choose two.) A. Only NBAR2 support Flexible NetFlow for extracting and exporting fields from the packet header.
B. Only NBAR2 allows the administrator to apply individual PDL files.
C. Only NBAR2 support PDLM to support new protocals.
D. Only NBAR2 can use Sampled NetFlow to extract pre-defined packet headers for reporting.
E. Only NBAR2 supports custom protocols based on HTTP URLs. Answer: AE QUESTION 182
Which two statements about Network Edge Authentication Technology (NEAT) are true? (Choose two.) A. It requires a standard ACL on the switch port
B. It conflicts with auto-configuration
C. It allows you to configure redundant links between authenticator and supplicant switches
D. It supports port-based authentication on the authenticator switch
E. It can be configured on both access ports and trunk ports
F. It can be configured on both access ports and EtherChannel ports Answer: DE QUESTION 183
What are three pieces of data you should review in response to a suspected SSL MITM attack? (Choose three.) A. The IP address of the SSL server
B. The X.509 certificate of the SSL server
C. The MAC address of the attacker
D. The MAC address of the SSL server
E. The X.509 certificate of the attacker
F. The DNS name off the SSL server Answer: ABF QUESTION 184
From what type of server can you to transfer files to ASA's internal memory? A. SSH
B. SFTP
C. Netlogon
D. SMB Answer: D QUESTION 185
Which configuration is the correct way to change VPN key Encryption key lifetime to 10800 seconds on the key server? 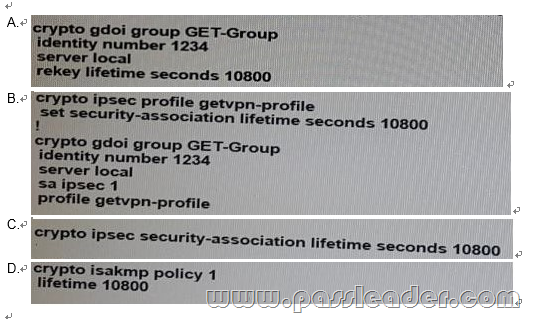
Answer: A QUESTION 186
Which feature can you implement to protect against SYN-flooding DoS attacks? A. the ip verify unicast reverse-path command
B. a null zero route
C. CAR applied to icmp packets
D. TCP Intercept Answer: B QUESTION 187
Refer to the exhibit. If R1 is connected upstream to R2 and R3 at different ISPs as shown, what action must be taken to prevent Unicast Reverse Path Forwarding (uRPF) from dropping asymmetric traffic?
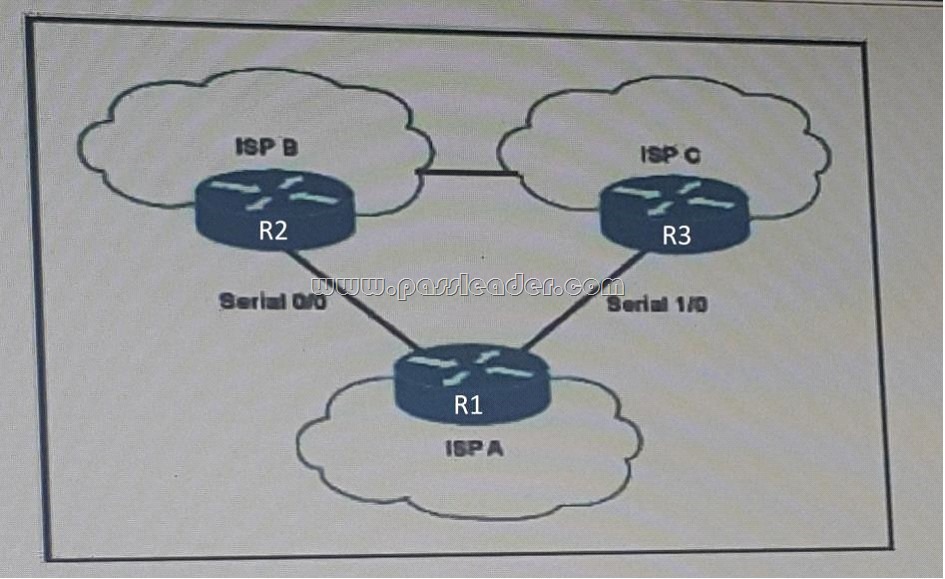 A. Configure Unicast RPF Loose Mode on R2 and R3 only.
B. Configure Unicast RPF Loose Mode on R1 only.
C. Configure Unicast RPF Strict Mode on R1 only.
D. Configure Unicast RPF Strict Mode on R1,R2 and R3.
E. Configure Unicast RPF Strict Mode on R2 and R3 only. Answer: E QUESTION 188
Refer to the exhibit. Which effect of this Cisco ASA policy map is true?
 A. The Cisco ASA is unable to examine the TLS session.
B. The server ends the SMTP session with a QUIT command if the algorithm or key length is insufficiently secure.
C. it prevents a STARTTLS session from being established.
D. The Cisco ASA logs SMTP sessions in clear text. Answer: B QUESTION 189
What security element must an organization have in place before it can implement a security audit and validate the audit results? A. firewall
B. network access control
C. an incident response team
D. a security policy
E. a security operation center Answer: D QUESTION 190
Which two statements about RFC 2827 are true? (Choose two.) A. RFC 2827 defines egress packet filtering to safeguard against IP spoofing.
B. A corresponding practice is documented by the IEFT in BCP 38.
C. RFC 2827 defines ingress packet filtering for the multihomed network.
D. RFC 2827 defines ingress packet filtering to defeat DoS using IP spoofing.
E. A corresponding practice is documented by the IEFT in BCP 84. Answer: BD QUESTION 191
From the list below, which one is the major benefit of AMP Threat GRID? A. AMP Threat Grid collects file information from customer servers and run tests on them to see if they are infected with viruses
B. AMP Threat Grid learns ONLY from data you pass on your network and not from anything else to monitor for suspicious behavior. This makes the system much faster and efficient
C. AMP Threat Grid combines Static, and Dynamic Malware analysis with threat intelligence into one combined solution
D. AMP Threat Grid analyzes suspicious behavior in your network against exactly 400 behavioral indicators Answer: C QUESTION 192
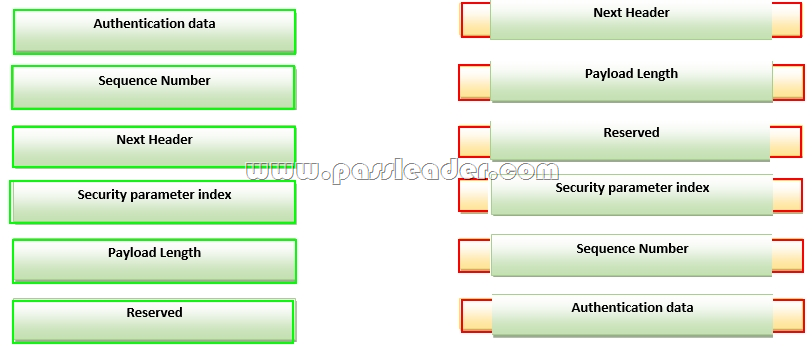
Drag and Drop Question
Drag each field authentication Header on the left into the order in which it appears in the header on the right.
 Answer:
 QUESTION 193
Which two statement about Infrastructure ACLs on Cisco IOS software are true? (Choose two.) A. Infrastructure ACLs are used to block-permit the traffic in the router forwarding path.
B. Infrastructure ACLs are used to block-permit the traffic handled by the route processor.
C. Infrastructure ACLs are used to block-permit the transit traffic.
D. Infrastructure ACLs only protect device physical management interface. Answer: BD QUESTION 194
Which three statements about SCEP are true? (Choose three.) A. It Supports online certification revocation.
B. Cryptographically signed and encrypted message are conveyed using PKCS#7.
C. The certificate request format uses PKCS#10.
D. It supports multiple cryptographic algorithms, including RSA.
E. CRL retrieval is support through CDP (Certificate Distribution Point) queries.
F. It supports Synchronous granting. Answer: BCE QUESTION 195
class-map nbar_rtp
match protocol rtp payload-type "0, 1, 4 - 0x10, 10001b - 10010b, 64"
The above NBAR configuration matches RTP traffic with which payload types? 
Answer: A QUESTION 196
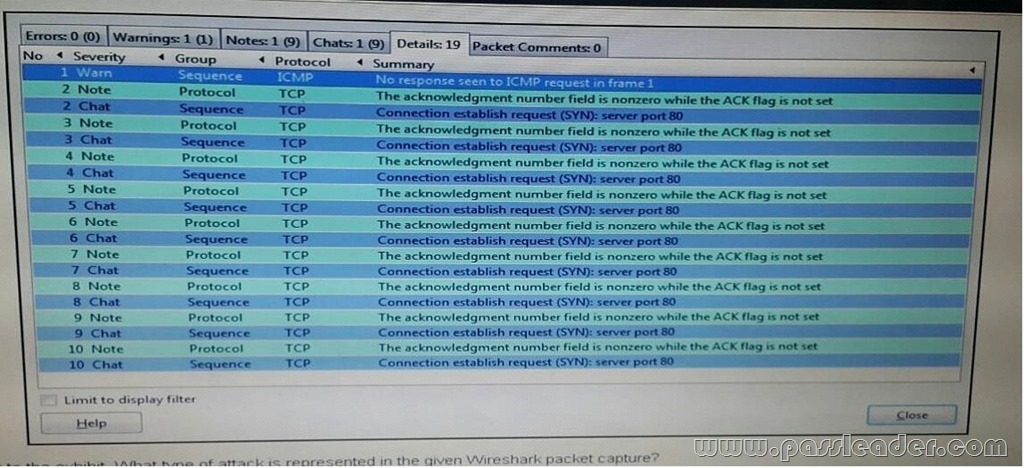
Refer to the exhibit. What type of attack is represented in the given Wireshark packet capture?
 A. a SYN flood
B. spoofing
C. a duplicate ACK
D. TCP congestion control
E. a shrew attack Answer: A QUESTION 197
What message does the TACACS+ daemon send during the AAA authentication process to request additional authentication information? A. ACCEPT
B. REJECT
C. CONTINUE
D. ERROR
E. REPLY Answer: C QUESTION 198
Refer to the exhibit.While troubleshooting a router issue, you executed the show ntp association command and it returned this output. Which condition is indicated by the reach value of 357?
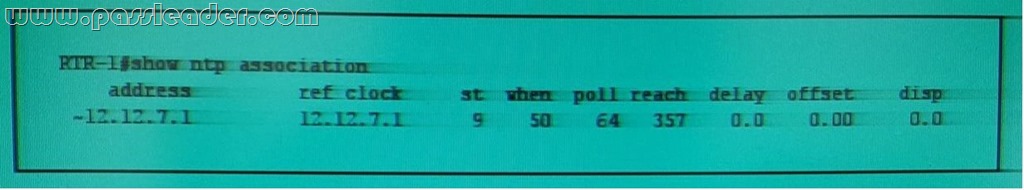 A. The NTP continuously received the previous 8 packets.
B. The NTP process is waiting to receive its first acknowledgement.
C. The NTP process failed to receive the most recent packet, but it received the 4 packets before the most recent packet.
D. The NTP process received only the most recent packet. Answer: C QUESTION 199
Which three IP resources is IANA responsible for? (Choose three.) A. IP address allocation
B. detection of spoofed address
C. criminal prosecution of hackers
D. autonomous system number allocation
E. root zone management in DNS
F. BGP protocol vulnerabilities Answer: ADE QUESTION 200
Which three attributes may be configured as part of the Common Tasks panel of an authorization profile in the Cisco ISE solution? (Choose three.) A. VLAN
B. voice VLAN
C. dACL name
D. voice domain permission
E. SGT Answer: ACD QUESTION 201
Which two statements about DTLS are true? (Choose two.) A. It uses two simultaneous IPSec tunnels to carry traffic.
B. If DPD is enabled, DTLS can fall back to a TLS connection.
C. Because it requires two tunnels, it may experience more latency issues than SSL connections.
D. If DTLS is disabled on an interface, then SSL VPN connections must use SSL/TLS tunnels.
E. It is disabled by default if you enable SSL VPN on the interface. Answer: BC QUESTION 202
Refer to the exhibit, which two Statements about the given Configuration are true? (Choose two.)
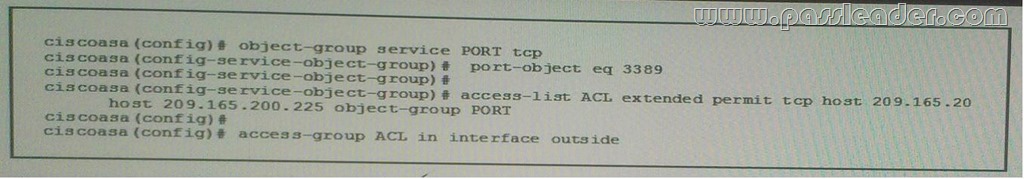 A. It is an inbound policy.
B. It will allow 209.165.202.129 to connect to 202.165.200.225 on an IMAP port.
C. It will allow 209.165.202.129 to connect to 202.165.200.225 on an RDP port.
D. It will allow 202.165.200.225 to connect to 209.165.202.129 on an RDP port.
E. It will allow 202.165.200.225 to connect to 209.165.202.129 on a VNC port.
F. It is an outbound policy. Answer: AC QUESTION 203
What command can you use to protect a router from TCP SYN-flooding attacks? A. ip igmp snooping
B. rate-limit input <bps><burst-normal><Burst-max>
C. ip tcp intercept list <access-list>
D. ip dns spoofing <ip-address>
E. police <bps> Answer: C QUESTION 204
Refer to the exhibit, what is the effect of the given configuration?
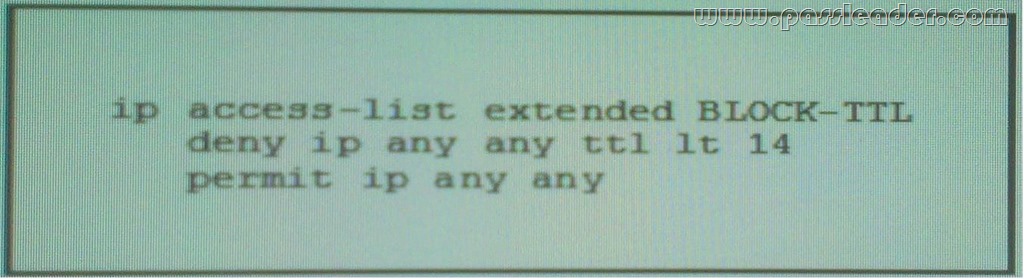 A. It will Drop all TTL packet with a value of 14 in the IP header field.
B. It will Drop all TTL packet with a TTL value less than 14.
C. It will Drop all TTL packet with a TTL value of 15 or more.
D. It will Drop all TTL packet with a TTL value of 14 or more. Answer: B QUESTION 205
If the ASA interfaces on a device are configured in passive mode, which mode must be configured on the remote device to enable EtherChannel? A. standby
B. active
C. on
D. passive Answer: B QUESTION 206
Which three statements about the SHA-2 algorithm are true? (Choose three.) A. It provides a variable-length output using a collision-resistant cryptographic hash.
B. It provides a fixed-length output using a collision-resistant cryptographic hash.
C. It is used for integrity verification.
D. It generates a 160-bit message digest.
E. It is the collective term for the SHA-224, SHA-256, SHA-384, and SHA-512 algorithms.
F. It generates a 512-bit message digest. Answer: BCE QUESTION 207
Drag and Drop Question
Drag and drop each RADIUS packet field on the left onto the matching decription on the right.
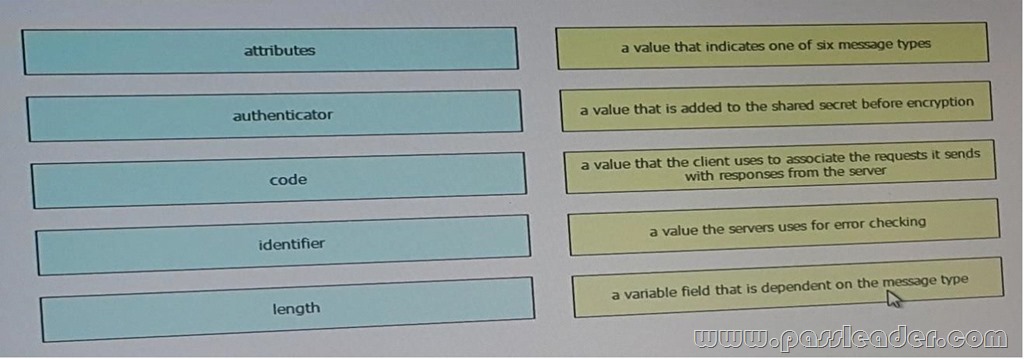 Answer:
 QUESTION 208
Which three of these situation warrant engagement of a security incident Response team? (Choose three.) A. damage to computer/network resources
B. pornographic biogs'websites
C. computer or network misuse/abuse
D. denial of service (DoS)
E. loss of data confidentialitymtegrity Answer: CDE QUESTION 209
What are three protocol that support layer 7 class maps and policy maps for zone based firewalls? (Choose three.) A. IMAP
B. RDP
C. MME
D. ICQ
E. POP3
F. IKE Answer: ADE QUESTION 210
You have configured an authenticator switch in access mode on a network configured with NEAT what radius attribute must the ISE server return to change the switch's port mode to trunk? A. device-traffic-class=switch
B. device-traffic-class=trunk
C. framed-protocol=1
D. EAP-message-switch
E. Authenticate=Administrative
F. Acct-Authentic=radius Answer: A
Download the newest PassLeader 400-251 dumps from passleader.com now! 100% Pass Guarantee! 400-251 PDF dumps & 400-251 VCE dumps: http://www.passleader.com/400-251.html (366 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!) p.s. Free 400-251 dumps download from Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpd3JLalNVS0VWbms
|











