Free Download 100% Pass Ensure 200q New 70-686 Exam Dumps! The new 70-686 vce dumps from PassLeader cover all new 70-686 exam questions, which will ensure your 70-686 exam 100% pass! Now the free new version VCE Player along with the 70-686 VCE braindumps, and the 70-686 PDF dumps are all available now!
keywords: 70-686 exam,200q 70-686 exam dumps,200q 70-686 exam questions,70-686 pdf dumps,70-686 vce dumps,70-686 braindumps,70-686 practice test,70-686 study guide,Pro: Windows 7, Enterprise Desktop Administrator Exam

QUESTION 151
Your network has a single domain with 1,000 client computers that run Windows Vista. All client computers are members of the domain. You are planning to deploy Windows 7. You need to create a report that shows hardware and device compatibility on all client computers. You need to perform this action without installing any additional software on the client computers. Which tool should you use?
A. System Center Configuration Manager
B. System Center Capacity Planner
C. Windows Performance Monitor Data Collector Sets
D. Microsoft Assessment and Planning Toolkit
Answer: D
QUESTION 152
You are designing a Windows 7 virtual desktop infrastructure. You have the following requirements:
* Provide access to Remote Desktop Services RemoteApp sources from multiple remote desktop servers.
* Support network load balancing. Support reconnection to existing sessions on virtual desktops.
You need to specify a design that meets the requirements. What should you include in your design?
A. Remote Desktop Gateway
B. Windows Deployment Services
C. Remote Desktop Connection Broker
D. Windows Virtual PC and Windows XP Mode
Answer: C
QUESTION 153
Your company plans to deploy Windows 7 Enterprise. The current client computers run either Windows XP Professional or Windows Vista Enterprise. The company uses 20 custom applications that were written for Windows XP. You need to create a log of compatibility issues for the custom applications. What should you do?
A. Install each application on a Windows XP client computer, and then run the Application Compatibility Toolkit (ACT).
B. Install each application on a Windows 7 client computer, and then run the Application Compatibility Toolkit (ACT).
C. Install each application on a Windows XP client computer. Sequence each application by using Microsoft Application Virtualization (App-V).
D. Install each application on a Windows Vista client computer. Sequence each application by using Microsoft Application Virtualization (App-V).
Answer: A
QUESTION 154
You are planning to deploy Windows 7. You have a custom line-of-business application that is not compatible with Windows 7. You need to design a solution that allows the application to run. What should you do?
A. Use the Windows Compatibility Evaluator.
B. Use the Setup Analysis Tool.
C. Use the Compatibility Administrator.
D. Use the Update Compatibility Evaluator.
Answer: C
QUESTION 155
Your company is planning to deploy Windows 7 to all client computers. You have the following requirements:
* Test an application to detect potential compatibility issues caused by User Account Control (UAC).
* Monitor an applications operating system use.
You need to select the appropriate method to detect application compatibility issues. What should you do?
A. Use the Setup Analysis Tool in a virtual environment.
B. Use the standalone Setup Analysis Tool.
C. Use the Standard User Analyzer Wizard.
D. Use the Standard User Analyzer tool.
Answer: D
QUESTION 156
Your company has a single Active Directory Domain Services (AD DS) domain and 1,000 Windows 7 computers. You are planning to deploy a custom application. You need to schedule the deployment to occur outside of business hours and without user interaction. Which deployment method should you choose?
A. Lite Touch Installation
B. software deployment with Microsoft System Center Configuration Manager 2007
C. software installation with Group Policy
D. Microsoft Application Virtualization (App-V)
Answer: B
QUESTION 157
Your network has 1,000 client computers that run Windows 7. You plan to deploy a new application. You need to ensure that the application deploys only during non-business hours. What should you do?
A. Use Group Policy.
B. Use Microsoft System Center Configuration Manager.
C. Use Windows Deployment Services with a schedule cast.
D. Use a logon script.
Answer: B
QUESTION 158
Your company has a single Active Directory Domain Services (AD DS) domain and 1,000 Windows Vista computers. You are planning to deploy Windows 7 and a custom application. You have the following requirements:
* The application must be available to only a specific group of users.
* You must be able to monitor application usage.
You need to design a deployment method for the custom application that meets the requirements. Which deployment method should you use in your design?
A. software installation in Group Policy
B. Microsoft Application Virtualization (App-V)
C. baseline Windows 7 image that includes the custom application
D. startup scripts in Group Policy
Answer: B
QUESTION 159
Your companys network has client computers that run Windows 7. A software vendor releases version 2 of an application that your company uses. Your company currently uses version 1. Version 1 and version 2 are not compatible. You plan to deploy version 2 of the application. You have the following requirements:
* Users must be able to run both versions of the application on their computers.
* Version 2 must be available when a client computer is not connected to the network.
You need to plan a software deployment process that meets the requirements. What should you do?
A. Deploy version 2 of the application by using a Microsoft System Center Configuration Manager package.
B. Deploy version 2 of the application by using a Group Policy Software Installation policy.
C. Deploy version 2 of the application as a Remote Desktop Services RemoteApp.
D. Deploy version 2 of the application by using Microsoft Application Virtualization (App-V).
Answer: D
QUESTION 160
Your network has client computers that run Windows XP. Users do not have administrative rights to their local computers. You use Windows Server Update Services (WSUS) to manage software updates. You are planning to deploy Windows 7. Your company uses a custom application that is not compatible with Windows 7. You need to ensure that all users are able to run the custom application. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
A. Install and register a shim on the WSUS server
B. Install and register a shim on the client computers by using Group Policy.
C. Deploy and register the compatibility-fix database file to the client computers by using a computer startup script.
D. Deploy and register the compatibility-fix database file to the client computers by using a user startup script.
Answer: BC

http://www.passleader.com/70-686.html
QUESTION 161
Your companys client computers run Windows 7. Your companys network has a wireless access point (WAP). A user reports that he regularly loses connectivity to the WAP. You need to display information about client connectivity to the WAP. What should you do?
A. Use Event Viewer to view events from a source of WlanConn.
B. Use auditpol.exe to enable successful attempts in the Object Access category.
C. Use Event Viewer to view events from a source of WLAN AutoConfig.
D. Use auditpol.exe to enable failed attempts in the Object Access category.
Answer: C
QUESTION 162
Your company has an Active Directory Domain Services (AD DS) forest with a single domain named contoso.com. The design of the domain and Group Policy object (GPO) is shown in the following diagram.
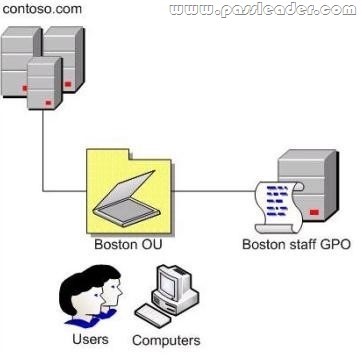
You configure Group Policy preferences to define mapped drives in the Boston staff GPO. Users in the Boston organizational unit (OU) then report that the mapped drives are not available. You need to identify and resolve Group Policy issues to ensure that the mapped drives are available. What should you do?
A. Enable loopback processing in Replace mode.
B. Enable loopback processing in Merge mode.
C. Enable the computer configuration settings.
D. Enable the user configuration settings.
Answer: D
QUESTION 163
You deploy Windows 7 and several custom Internet Explorer add-ons to 1,000 client computers. Internet Explorer closes when users run a specific Web application. You need to find out whether an add-on is the cause of the problem. What should you do?
A. Use Group Policy to disable the Programs tab in Internet Explorer for all client computers.
B. Use Group Policy to turn on Internet Explorer 7 Standards mode.
C. Start Internet Explorer in No Add-ons mode.
D. Reset all Internet Explorer security zones to the default levels.
Answer: C
QUESTION 164
Your companys network has client computers that run Windows 7. From a computer named Computer1, a user attempts to log on to the domain and receives the following message: The system cannot log you on to this domain because the system’s computer account in its primary domain is missing or the password on that account is incorrect. You need to ensure that the user can log on to the domain from Computer1. What should you do?
A. Reset the password of the user account.
B. Move the computer account for Computer1 to the Computers container.
C. Run netdomcomputername computer1.
D. Remove Computer1 from the domain and rejoin Computer1 to the domain.
Answer: D
QUESTION 165
Your company has a single Active Directory Domain Services (AD DS) forest with a single domain named contoso.com. All client computers run Windows 7. All client computer accounts are located in the Computers container in the contoso.com domain. You discover that multiple client computers were automatically shut down because the security log was full. You need to ensure that client computers are not shut down when the security log becomes full. What should you do?
A. Increase the maximum log size.
B. Configure an Event Viewer subscription.
C. Modify the event log policy settings in the Default Domain Controllers Policy Group Policy object (GPO).
D. Modify the event log policy settings in the Default Domain Policy Group Policy object (GPO).
Answer: D
QUESTION 166
Your company has an internal Web application that uses a self-signed SSL certificate. The company has an internal certification authority (CA) with auto enrollment. When users attempt to start the Web application, Internet Explorer displays an error message that recommends closing the Web page rather than continuing to the application. You need to ensure that Internet Explorer does not display the error message. What should you do?
A. Install the Web applications certificate into the computer store on each client computer.
B. Purchase a commercial certificate and install it on the internal CA.
C. Issue a certificate from the internal CA and install it on the application server.
D. Install the Web applications certificate into the personal store on each client computer. Add the applications URL to the Trusted Sites zone in Internet Explorer.
Answer: C
QUESTION 167
Your company has an Active Directory Domain Services (AD DS) forest with a single domain named contoso.com. You deploy a new Group Policy object (GPO) named NY Computers GPO as part of the organizational unit (OU) and GPO design shown in the following diagram.
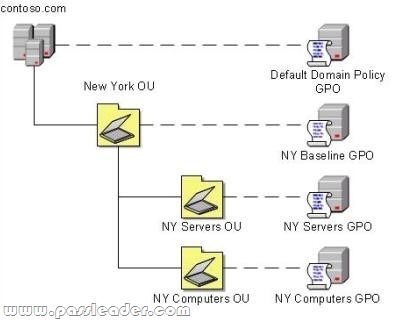
The NY Computers GPO contains computer configuration settings and user configuration settings. User configuration settings are not being applied to users who log on to client computers in the NY Computers OU. You need to ensure that user configuration settings are being applied. What should you do?
A. Enable user configuration settings in the Default Domain Policy GPO.
B. Enable loopback processing in the NY Computers GPO.
C. Enable user configuration settings in the NY Computers GPO.
D. Enable loopback processing in the Default Domain Policy GPO.
Answer: B
QUESTION 168
You create a shim database and distribute it to each of a companys client computers through a script. You name the database Shim_Database and give it a filename of shimdatabase.sdb. The database GUID is 18315260-2ecb-43af-945a-56810da33fb4. The database must be registered on all client computers. The registration process must be invisible to the user. You need to construct a command to register the shim database. Which command should you use? To answer, drag the appropriate component from the list of command components to the correct location or locations in the work area.
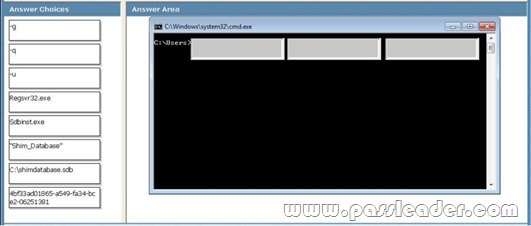
Answer:
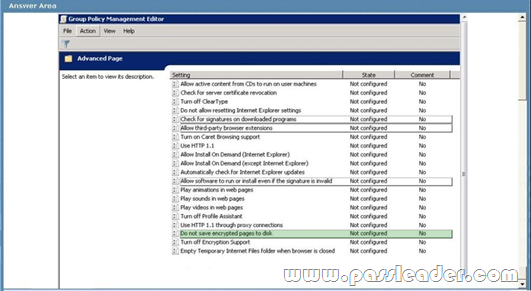
QUESTION 169
You upgrade all of a companys client computers from Microsoft Internet Explorer 8 to Internet Explorer 9. After the upgrade, users are unable to download attachments from Microsoft Outlook Web App (OWA) or any other secure website. You verify the Group Policy settings for Internet Explorer 9. You need to ensure that all users can download attachments from OWA and other secure websites. Which setting should you select? To answer, select the appropriate item in the work area.
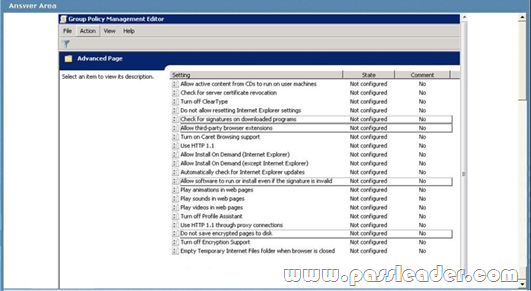
Answer:
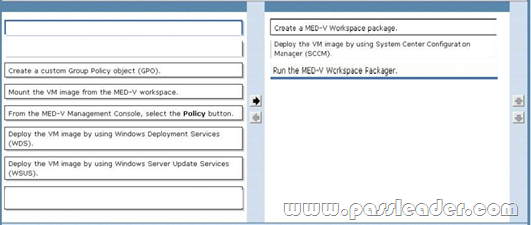
QUESTION 170
Your company has 1,000 client computers that run Windows 7. The company uses several custom line-of-business applications that are not compatible with Windows 7. You need to distribute a Microsoft Enterprise Desktop Visualization (MED-V) virtual machine (VM) image that includes the custom applications to all Windows 7 client computers. Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
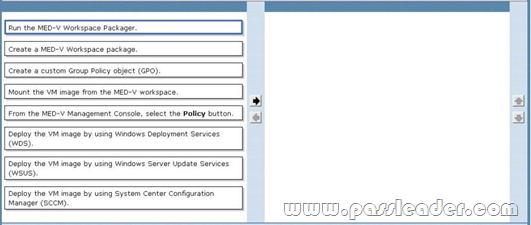
Answer:

http://www.passleader.com/70-686.html