PassLeader supply the newest 299q 70-689 vce dumps and pdf dumps, the latest 299q 70-689 braindumps are the best dumps with all the new exam questions, it will let you passing 70-689 exam easily and quickly. Now going to passleader.com and download the valid 70-689 exam dumps and FREE VCE PLAYER!
keywords: 70-689 vce file,299q 70-689 exam dumps,299q 70-689 exam questions,70-689 pdf dumps,70-689 vce dumps,70-689 braindumps,70-689 practice test,70-689 study guide,Microsoft Upgrading Your Skills to MCSA Windows 8

QUESTION 211
You administer client computers that run Windows 8 Enterprise deployed by using Windows Deployment Services (WDS). Your company recently purchased 25 new tablets that run Windows 8 Pro. For all 25 new tablets, you want to replace the existing Windows 8 Pro installation with Windows 8 Enterprise. You need to deploy the Windows 8 Enterprise image to all 25 tablets simultaneously by using the existing WDS infrastructure. What should you do?
A. Start the tablets by using a network boot option.
B. Start the tablets from a default Windows Recovery Environment (WinRE).
C. Start the tablets in Windows Recovery mode.
D. Start the tablets from the Windows To Go workspace.
Answer: A
QUESTION 212
You have 100 client computers that run Windows 8 Pro. Each computer has a single local hard disk drive, a DVD drive, and an external USB drive. Each computer has a different set of line-of-business (LOB) desktop applications that are installed locally. All of the applications store their configurations in the HKEY_Local_Machine\Software registry hive. You need to design a recovery solution to ensure that you can restore the initial state of the locally installed LOB desktop applications if an application is misconfigured. The solution must preserve the existing locally stored user data. What should you do?
A. Enable File History. Restore files by using File History.
B. Create a Microsoft Diagnostics and Recovery Toolset (DaRT) recovery image. Start the computer from the DaRT image and perform a file restore.
C. Run recimg.exe. Perform a system refresh.
D. Create a system repair disk by using Windows 7 File Recovery. Start the computer from the Windows 8 Enterprise installation media and perform an automatic repair,
Answer: C
Explanation:
Reinstalling all of your Desktop apps can be time consuming, so Windows 8 offers a command called recimg.exe to make this easier. recimg creates an image which is used by the refresh facility when restoring Windows. Not only will your personal data and Metro style apps be saved, but so will Desktop apps you have installed at the time you create the image. This can save you a lot of time.
QUESTION 213
At home, you use a desktop computer that runs Windows 8. At work, you use a laptop that runs Windows 8 and is connected to a corporate network. You use the same Microsoft account to log on to both computers. You have a folder with some personal documents on your desktop computer. The folder must be available and synced between both computers. You need to ensure that the latest version of these files is available. What should you do?
A. Move the folder to the Documents folder.
B. Go to PC Settings. Under Homegroup, select Documents to be Shared.
C. Install SkyDrive for Windows. In Windows Explorer, move the folder that contains the personal documents to the SkyDrive folder.
D. Move the folder to the Libraries folder.
E. Go to PC Settings. Under Sync your settings, enable App settings.
F. Right-click the folder and click Properties. Under Security, provide Full Control for the Microsoft account.
Answer: A
QUESTION 214
Drag and Drop Questions
You have a computer that runs Windows 8. You have a 1-terabyte external hard drive. You purchase a second 1-terabyte external hard drive. You need to create a fault-tolerant volume that includes both external hard drives. You also need to ensure that additional external hard drives can be added to the volume. Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
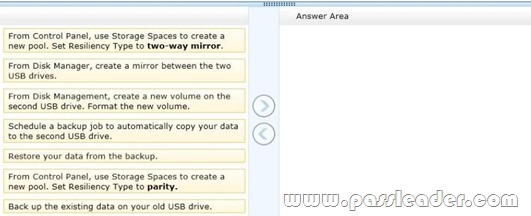
Answer:
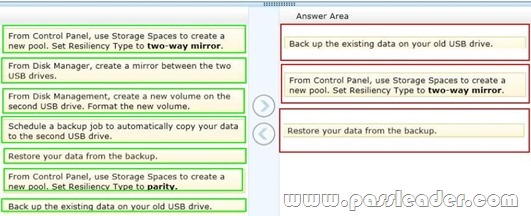
Explanation:
To create a storage space, you’ll have to connect two or more additional drives to your computer you can’t use your system drive for this. The drives can be either internal or external drives. You can open the Storage Spaces configuration window from the Control Panel or by bringing up the Start screen with the Windows key, typing “Storage Spaces,” clicking the Settings category and selecting the Storage Spaces shortcut. Select the drives you want to use for the storage space and click the “Create pool” button to continue. You’ll lose any files that are already on the drive – copy any important files off the drives before pooling them. You can add additional drives later. The resiliency type controls how Windows handles your data. There are four options:
* None: Windows will store only a single copy of your. You’ll lose the data if one of your drives fails, but no space will be used on backups.
* Two-way mirror: Windows will store two copies of your data. If one of your drives fails, you won’t lose your data. This requires at least two drives.
* Three-way mirror: Windows will store three copies of your data. If one or two of your drives fails, you won’t lose your data. This requires at least three drives.
* Parity: Windows stores parity information with the data, protecting you from a single drive failure. Parity uses drive space more efficiently than mirroring, but file access times are slower. Parity is ideal for drives with large, infrequently updated files, such as video files. Reference: How to Use Windows 8s Storage Spaces to Mirror & Combine Drives
QUESTION 215
You administer computers that run Windows 8 Pro and are members of an Active Directory domain. The computers are encrypted with BitLocker and are configured to store BitLocker encryption passwords in Active Directory. A user reports that he has forgotten the BitLocker encryption password for volume E on his computer. You need to provide the user a BitLocker recovery key to unlock the protected volume. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Ask the user for his computer name.
B. Ask the user to run the manage-bde -unlock E: -pw command.
C. Ask the user for his logon name.
D. Ask the user for a recovery key ID for the protected volume.
Answer: AC
QUESTION 216
You administer laptops that run Windows 8 Enterprise and are members of an Active Directory domain. Users travel frequently and access domain resources from inside client networks or from their home network. You want to manage the laptops when they are connected to the company network from the external networks. You need to ensure that the laptops can be managed and maintained while users are not logged on to the computers. Which of the following should you recommend?
A. Remote Assistance
B. Windows Remote Management (WinRM)
C. DirectAccess
D. Remote Desktop
Answer: C
QUESTION 217
You support computers that run Windows 8 Pro and are members of an Active Directory domain. Several desktop computers are located in a subnet that is protected by a firewall. The firewall allows incoming TCP connections only to ports 80 and 443. You want to manage disk volumes on the desktop computers from your computer, which is located outside the protected subnet. You need to configure the network to support the required remote administration access. What should you do?
A. Enable Remote Desktop on the desktop computers.
B. Run the winrm quickconfig command on your computer.
C. Install Remote Server Administration Tools (RSAT) on your computer.
D. Run the winrm quickconfig command on the desktop computers.
Answer: D
QUESTION 218
You support desktop computers and tablets that run Windows 8 Enterprise. All of the computers are able to connect to your company network from the Internet by using DirectAccess. Your company wants to deploy a new application to the tablets. The deployment solution must meet the following requirements:
– The application is not accessible if a user is working offline.
– The application is stored on an internal solid-state drive (SSD) on the tablets.
– The application is isolated from other applications.
– The application uses the least amount of disk space.
You need to deploy the new application to the tablets. What should you do?
A. Deploy the application as an Application Virtualization (App-V) package. Install the App-V 4.6 client on the tablets.
B. Deploy the application as a published application on the Remote Desktop server. Create a Remote Desktop connection on the tablets.
C. Install the application on a local drive on the tablets.
D. Install the application in a Windows To Go workspace.
E. Install Hyper-V on tablets. Install the application on a virtual machine.
F. Publish the application to Windows Store.
G. Install the application within a separate Windows 8 installation in a virtual hard disk (VHD) file. Configure the tablets with dual boot.
H. Install the application within a separate Windows 8 installation in a VHDX file. Configure tablets with dual boot.
Answer: A
QUESTION 219
You support desktop computers and tablets that run Windows 8 Enterprise. All of the computers are able to connect to your company network from the Internet by using DirectAccess. Your company wants to deploy a new application to the tablets. The deployment solution must meet the following requirements:
– Users have offline access to the application only within the first seven days following their latest online session.
– The application uses the least amount of disk space.
You need to deploy the new application to the tablets. What should you do?
A. Deploy the application as an Application Virtualization (App-V) package. Install the App-V client on the tablets.
B. Deploy the application as a published application on the Remote Desktop server. Create a Remote Desktop connection on the tablets.
C. Install the application on a local drive on the tablets.
D. Install the application in a Windows To Go workspace.
E. Install Hyper-V on tablets. Install the application on a virtual machine.
F. Publish the application to Windows Store.
G. Install the application within a separate Windows 8 installation in a virtual hard disk (VHD) file. Configure the tablets with dual boot.
H. Install the application within a separate Windows 8 installation in a VHDX file. Configure tablets with dual boot.
Answer: A
QUESTION 220
Hotspot Questions
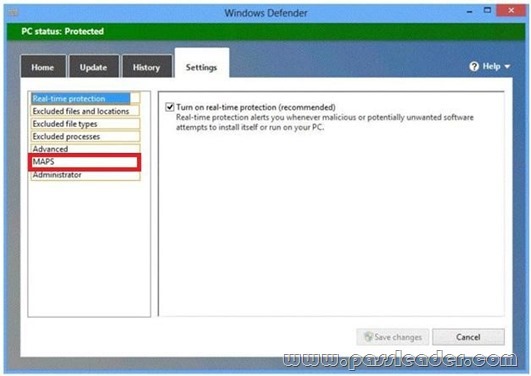
You have computers that run Windows 8 Pro and are configured as a workgroup. Each computer is scheduled to run a Windows Defender full scan every morning at 07:00. Users report that they are unable to view previous instances of detected malware when they arrive to work. You need to ensure that all users can see previous instances of detected malware in Windows Defender. Which option on the Settings tab should you select? (To answer, select the appropriate option in the answer area.)
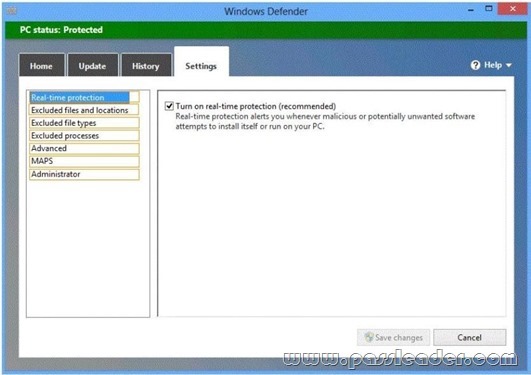
Answer:

70-689 exam dumps, 70-689 exam questions, 70-689 vce dumps, 70-689 pdf dumps, 70-689 practice test, 70-689 study guide: http://www.passleader.com/70-689.html
QUESTION 221
You support laptops that run Windows 8 Pro and are part of a workgroup. An employee is unable to start Windows Mobility Center on his laptop. You need to make it possible for the employee to use Windows Mobility Center on the laptop. What should you do?
A. Use Add features to Windows 8 to add Windows Mobility Center.
B. Use Programs and Features to repair the installation of Windows Mobility Center.
C. Use Local Group Policy Editor to set Turn off Windows Mobility Center to Not Configured.
D. Use Turn Windows features on or off in Programs and Features to enable Windows Mobility Center.
Answer: A
QUESTION 222
You administer computers that run Windows 8 Enterprise and are members of a workgroup. Company policy requires that all computers receive the latest updates from a Windows Server Update Services (WSUS) server. Only updates that are digitally signed by Microsoft are installed. You need to configure the computers to automatically receive and apply the updates. What should you do first?
A. Configure the Configure Automatic Updates policy setting to Allow local admin to choose setting.
B. Configure the Configure Automatic Updates policy setting to Auto download and schedule for install.
C. Configure the Specify intranet Microsoft update service location policy setting to use the local WSUS server.
D. Enable the Allow signed updates from an intranet Microsoft update service location policy setting.
Answer: C
QUESTION 223
You administer several computers that run Windows 8. The manufacturer of the video display adapters used in these computers issues a new version of the video driver. You need to install the new version of the driver on the computers. What should you do first?
A. From the Start screen, search settings for “update device drivers.”
B. From the Start screen, search settings for “devices and printers.”
C. From the Start screen, right-click the Video tile.
D. From the Start screen, open the Charms bar and select Devices.
E. From the Start screen, open the Charms bar and select Settings.
Answer: A
QUESTION 224
You are an administrator for a large company that has an Active Directory domain. Your company has tablets that run Windows RT. Users report that their tablets get locked after one minute of inactivity. They also report that when they change the Personalization setting to 15 minutes, it resets back to 1 minute. You need to ensure that the lockout time for inactivity is set to 15 minutes. What should you do?
A. Log on to the tablets as a local administrator and configure the screensaver wait time and logon options.
B. Modify Group Policy.
C. Modify ActiveSync configuration.
D. Log on to the tablets as a local administrator and run the PowerShell cmdlet Set -ScreenSaverTimeout -Seconds 900.
E. Configure the local system policy Do not display the lock screen setting to Enabled.
Answer: C
QUESTION 225
Hotspot Questions
You support computers that run Windows 8 Pro. You plug a legacy hardware adapter into a computer. You open Device Manager and notice that the legacy hardware adapter is not listed. You need to install the legacy hardware adapter. To which node should you add the legacy hardware adapter? (To answer, select the appropriate object in the answer area.)
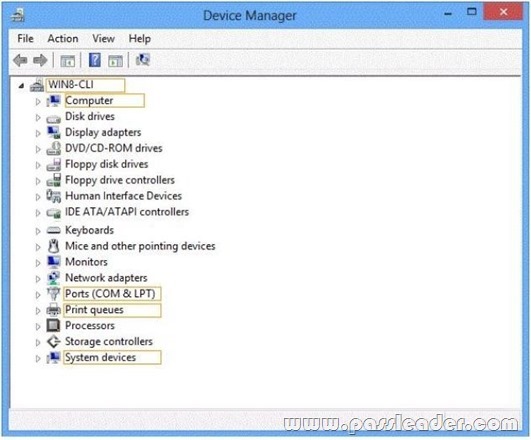
Answer:
QUESTION 226
You administer computers that run Windows 8 Pro. You have secured the computers by using BitLocker. You have distributed a new application to the computers. Users report that file associations for ZIP archives is broken and users are unable to open ZIP files. You need to design a solution that recovers file association. You also need to ensure that BitLocker encryption settings are maintained. What should you do?
A. Restore computer from the latest restore point.
B. Delete the HKEY_CLASSES_ROOT\exefile\shell\open\command registry key.
C. Modify setting in Change default settings for media or devices.
D. Select Reset your PC.
Answer: A
QUESTION 227
You support computers that run Windows 8 Enterprise and are members of a workgroup. Users are able to download and install any app from Windows Store. You need to ensure that only approved apps can be installed from Windows Store. What should you do?
A. Configure an AppLocker Packaged app rule.
B. Enable Windows SmartScreen and select the Get administrator approval before running an unrecognized app from the Internet option.
C. Configure an AppLocker Publisher rule.
D. Configure a Software Restriction Policy Certificate rule.
Answer: A
QUESTION 228
Drag and Drop Questions
You support computers that run Windows 8. A computer receives a STOP error. You plan to restore the operating system without losing user documents and settings. You need to restore the operating system and user data in the least amount of time. Which three steps should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Answer:
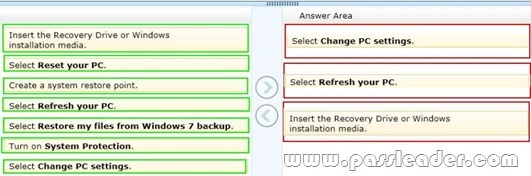
Explanation:
Note:
* Refresh PC lets you restore all Windows settings to their defaults without deleting your documents, music and other files, and Reset PC reinstalls Windows and wipes out everything, including your files.
* To refresh your PC:
1. Swipe in from the right edge of the screen, tap Settings, and then tap Change PC set-tings. (If you’re using a mouse, point to the upper-right corner of the screen, move the mouse pointer down, click Settings, and then click Change PC settings.)
2. Under PC settings, tap or click General.
3. Under Refresh your PC without affecting your files, tap or click Get started.
4. Follow the instructions on the screen.
If asked, insert your Windows 8 disc, flash drive, or whatever else you used to first install Windows.
Reference: How To Reset Or Refresh Windows 8 Without DVD.
QUESTION 229
You administer client computer that run Windows 8 Enterprise deployed by using Windows Deployment Services (WDS). Your company recently purchased 25 new tablets that run Windows 8 Pro. For all 25 new tables, you want to replace the existing Windows 8 Pro installation with Windows 8 enterprise. You need to deploy the Windows 8 Enterprise image to all 25 tablets simultaneously by using the existing WDS infrastructure. What should you do?
A. Start the tablets normally. Map the Windows Image (WIM) file from a WDS network share.
B. Start the tablets from a customized Windows Recovery Environment (WinRE)
C. Start the tablets in Windows Recovery Mode.
D. Start the tablets from a USB flash drive with a customized Windows Preinstallation Environment (WinPE.).
Answer: A
Explanation:
Extract the boot.wim file. Use the boot.wim file to create a bootable partition.
QUESTION 230
You have a client computer that runs Windows 8 Enterprise. The computer uses BitLocker Drive Encryption (BitLocker) on a fixed disk that only stores data. You need to prevent any data from being written to the fixed disk. What should you do?
A. Run the Disable-BitLocker cmdlet.
B. Run the manage-bde command and specify the -pause switch.
C. Run the Lock-BitLocker cmdlet.
D. Run the manage-bde command and specify the -off switch.
Answer: B
Explanation:
Manage-bde: pause
Pauses BitLocker encryption or decryption.
Incorrect answers:
Not A: The Disable-BitLocker cmdlet disables BitLocker Drive Encryption for a BitLocker volume. When you run this cmdlet, it removes all key protectors and begins decrypting the content of the volume.

http://www.passleader.com/70-689.html