Want to pass new 70-414 exam easily? PassLeader have been updated the 70-414 exam dumps with the newest exam questions. We offer the latest 247q 70-414 PDF dumps and VCE dumps with New Version VCE simulator for free download to ensure your 70-414 exam passing. Now visit www.passleader.com and get the 100 percent pass ensure 70-414 braindumps!
keywords: 70-414 exam,247q 70-414 exam dumps,247q 70-414 exam questions,70-414 pdf dumps,70-414 practice test,70-414 vce dumps,70-414 study guide,70-414 braindumps,Implementing an Advanced Server Infrastructure Exam
P.S. Download Free 70-414 PDF Dumps and Preview PassLeader 70-414 VCE Dumps At The End Of This Post!!! (Ctrl+End)
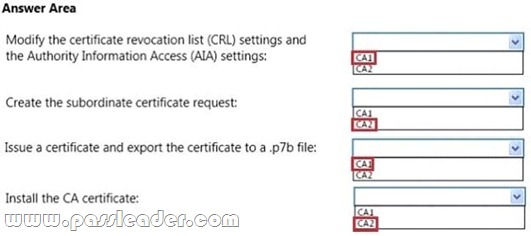
QUESTION 141
You plan to deploy a certification authority (CA) infrastructure that contains the following servers:
– An offline standalone root CA named CA1
– An enterprise subordinate CA named CA2
On all of the computers, you import the root CA certificate from CA1 to the Trusted Root Certification Authorities Certificates store. You need to ensure that CA2 can issue certificates for the CA hierarchy. What should you do? To answer, select the appropriate options in the answer area.

Answer:
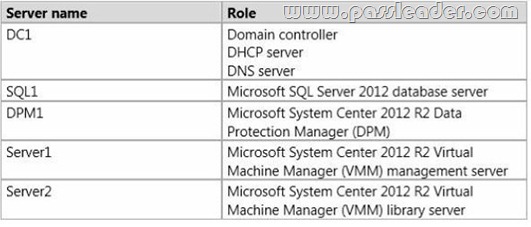
QUESTION 142
Your network contains five physical servers. The servers are configured as shown in the following table.
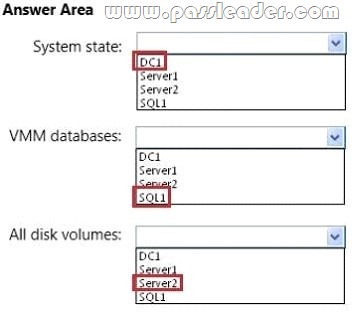
All servers run Windows Server 2012 R2. During the setup of VMM, you configure distributed key management. You need to ensure that the entire VMM infrastructure can be restored. What should you include in the backup plan? To answer, select the appropriate server to back up for each backup content type in the answer.
Answer:
QUESTION 143
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. System Center 2012 R2 Virtual Machine Manager (VMM) is deployed to the domain. In VMM, you create a host group named HostGroup1. You add a 16-node Hyper-V failover cluster to HostGroup1. From Windows PowerShell, you run the following commands:
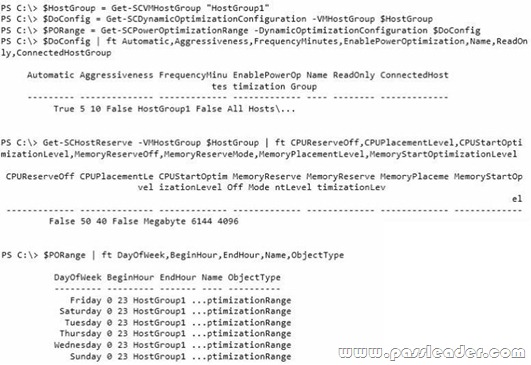
Use the drop-down menus to select the answer choice that completes each statement.
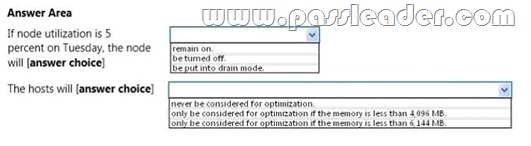
Answer:
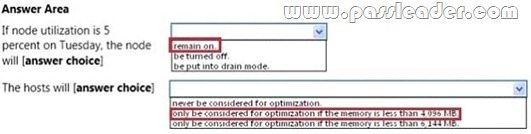
QUESTION 144
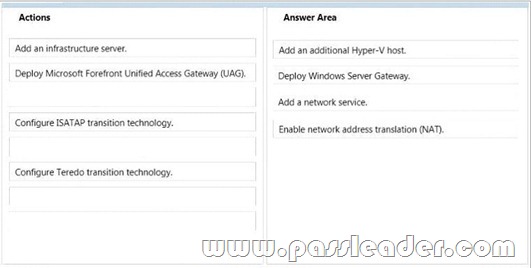
You are planning to set up a proof-of-concept network virtualization environment. The environment will contain three servers. The servers will be configured as shown in the following table.
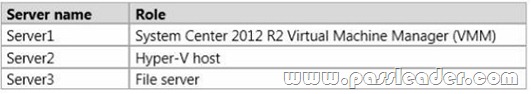
You need to enable network connectivity between the virtual machines and Server3. Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
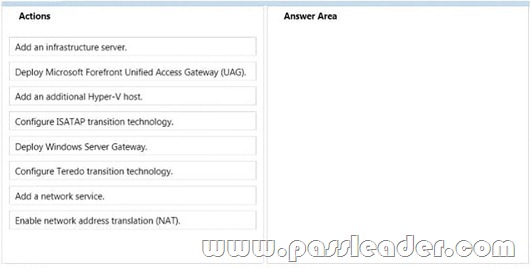
Answer:
QUESTION 145
You have a System Center 2012 R2 Virtual Machine Manager (VMM) deployment. You implement Hyper-V Recovery Manager for the deployment. You create two new clouds named Cloud1 and Cloud2. Metadata for both clouds is uploaded to Windows Azure. You need to ensure that the virtual machines in Cloud1 are protected by using replicas in Cloud2. Where should you perform each action? To answer, select the appropriate tool for each action in the answer area.
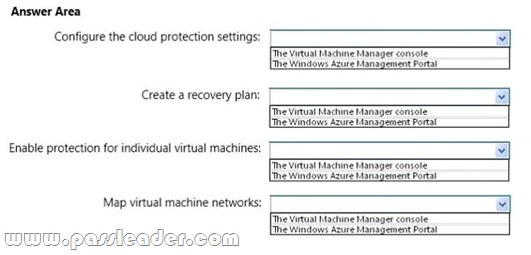
Answer:

QUESTION 146
Your network contains an Active Directory forest named contoso.com. All servers run Windows Server 2012 R2. The forest contains two servers. The servers are configured as shown in the following table.
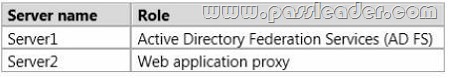
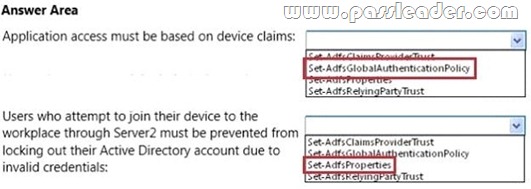
You prepare the forest to support Workplace Join and you enable the Device Registration Service (DRS) on Server1. You need to ensure that Workplace Join meets the following requirements:
– Application access must be based on device claims.
– Users who attempt to join their device to the workplace through Server2 must be prevented from
locking out their Active Directory account due to invalid credentials. Which cmdlet should you run to achieve each requirement? To answer, select the cmdlet for each requirement in the answer area.
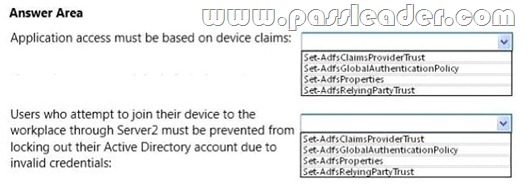
Answer:
QUESTION 147
Your network contains two servers named Server1 and Server2 that run Windows Server 2012. Server1 and Server2 are connected to a Fibre Channel Storage Area Network (SAN). Server1 and Server2 are members of a failover cluster named Cluster1. You plan to host the clustered File Server role on the nodes in Cluster1. Cluster1 will store application databases in shared folders. You need to implement a storage solution for Cluster1. The solution must minimize the amount of time the shared folders are unavailable during a failover. What should you implement? More than one answer choice may achieve the goal. Select the BEST answer.
A. An iSCSI Target Server cluster role in Cluster1
B. The Multi Path I/O (MPIO) feature on Server1 and Server2
C. A Virtual Fibre Channel SAN on Server1 and Server2
D. A Cluster Shared Volume (CSV) in Cluster1
Answer: D
QUESTION 148
Your network contains two servers named Server1 and Server2 that run Windows Server 2012. Server1 and Server2 are members of a failover cluster named Cluster1 and are connected to an iSCSI Storage Area Network (SAN). You need to ensure that you can implement the clustered File Server role of the File Server for scale-out application data type for Cluster1. What should you install?
A. The iSCSI Target Server cluster role
B. The Distributed Transaction Coordinator (DTC) cluster role
C. The DFS Namespace Server cluster role
D. A Cluster Shared Volume (CSV)
Answer: D
QUESTION 149
Your network contains an Active Directory domain named contoso.com. The domain contains Server 2012 R2 and has the Hyper-V server role installed. You need to log the amount of system resources used by each virtual machine. What should you do?
A. From Windows PowerShell, run the Enable-VMResourceMeteringcmdlet.
B. From Windows System Resource Manager, enable Accounting.
C. From Windows System Resource Manager, add a resource allocation policy.
D. From Windows PowerShell, run the Measure-VM cmdlet.
Answer: A
QUESTION 150
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named HVServer1. HVServer1 runs Windows Server 2012 R2 and has the Hyper-V server role installed. HVServer1 hosts 10 generation 1 virtual machines. All of the virtual machines connect to a virtual switch named Switch1. Switch1 is configured as a private network. All of the virtual machines have the DHCP guard and the router guard settings enabled. You install the DHCP server role on a virtual machine named Server1. You authorize Server1 as a DHCP server in contoso.com. You create an IP scope. You discover that the virtual machines connected to Switch1 do not receive IP settings from Server1. You need to ensure that the virtual machines can use Server1 as a DHCP server. What should you do?
A. Enable MAC address spoofing on Server1.
B. Enable single-root I/O visualization (SR-IOV) on Server1.
C. Disable the DHCP guard on Server1.
D. Disable the DHCP guard on all of the virtual machines that are DHCP clients.
Answer: C
QUESTION 151
You have a server named Server1 that runs Windows Server 2012 R2. You plan to enable Hyper-V Network Virtualization on Server1. You need to install the Windows Network Virtualization Filter Driver on Server1. Which Windows PowerShell cmdlet should you run?
A. Set-NetVirtualizationGlobal
B. Enable-NetAdapterBinding
C. Add – WindowsFeature
D. Set-NetAdapterVmq
Answer: B
QUESTION 152
Your network contains an Active Directory domain named contoso.com. You install Windows Server 2012 R2 on a new server named Server1 and you join Server1 to the domain. You need to ensure that you can view processor usage and memory usage information in Server Manager. What should you do?
A. From Server Manager, click Configure Performance Alerts.
B. From Performance Monitor, create a Data Collector Set (DCS).
C. From Performance Monitor, start the System Performance Data Collector Set (DCS).
D. From Server Manager, click Start Performance Counters.
Answer: D
QUESTION 153
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. The domain contains a virtual machine named VM1. A developer wants to attach a debugger to VM1. You need to ensure that the developer can connect to VM1 by using a named pipe. Which virtual machine setting should you configure?
A. BIOS
B. Network Adapter
C. COM 1
D. Processor
Answer: C
QUESTION 154
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server 1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed. You create an external virtual switch named Switch1. Switch1 has the following configurations:
– Connection type: External network
– Single-root I/O virtualization (SR-IOV): Enabled
Ten virtual machines connect to Switch1. You need to ensure that all of the virtual machines that connect to Switch1 are isolated from the external network and can connect to each other only. The solution must minimize network downtime for the virtual machines. What should you do?
A. Remove Switch1 and recreate Switch1 as an internal network.
B. Change the Connection type of Switch1 to Private network.
C. Change the Connection type of Switch1 to Internal network.
D. Remove Switch1 and recreate Switch1 as a private network.
Answer: B
QUESTION 155
Your network contains two Hyper-V hosts named Host1 and Host2. Host1 contains a virtual machine named VM1. Host2 contains a virtual machine named VM2. VM1 and VM2 run Windows Server 2012 R2. You install the Network Load Balancing feature on VM1 and VM2. You need to ensure that the virtual machines are configured to support Network Load Balancing (NLB). Which virtual machine settings should you configure on VM1 and VM2?
A. DHCP guard
B. MAC address
C. Router guard
D. Port mirroring
Answer: B
QUESTION 156
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed. On Server1, an administrator creates a virtual machine named VM1. A user named User1 is the member of the local Administrators group on Server1. User1 attempts to modify the settings of VM1 as shown in the following exhibit. (Click the Exhibit button.)
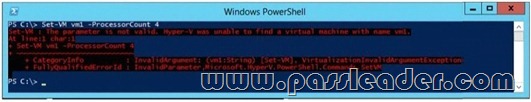
You need to ensure that User1 can modify the settings of VM1 by running the Set-Vmcmdlet. What should you instruct User1 to do?
A. Run Windows PowerShell with elevated privileges.
B. Install the Integration Services on VM1.
C. Modify the membership of the local Hyper-V Administrators group.
D. Import the Hyper-V module.
Answer: A
QUESTION 157
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 has access to four physical disks. The disks are configured as shown in the following table.
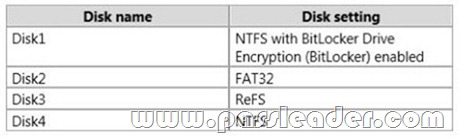
You need to ensure that all of the disks can be added to a Cluster Shared Volume (CSV). Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Enable BitLocker on Disk4.
B. Disable BitLocker on Disk1.
C. Format Disk2 to use NTFS.
D. Format Disk3 to use NTFS.
Answer: CD
QUESTION 158
Your network contains three servers named HV1, HV2, and Server1 that run Windows Server 2012 R2. HV1 and HV2 have the Hyper-V server role installed. Server1 is a file server that contains 3 TB of free disk space. HV1 hosts a virtual machine named VM1. The virtual machine configuration file for VM1 is stored in D:\VM and the virtual hard disk file is stored in E:\VHD. You plan to replace drive E with a larger volume. You need to ensure that VM1 remains available from HV1 while drive E is being replaced. You want to achieve this goal by using the minimum amount of administrative effort. What should you do?
A. Perform a live migration to HV2.
B. Add HV1 and HV2 as nodes in a failover cluster.
Perform a storage migration to HV2.
C. Add HV1 and HV2 as nodes in a failover cluster.
Perform a live migration to HV2.
D. Perform a storage migration to Server1.
Answer: D
QUESTION 159
Hotspot Question
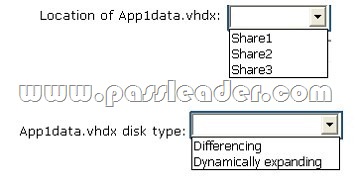
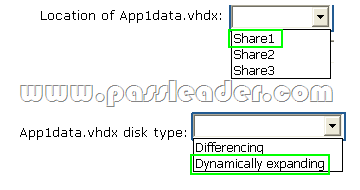
Your network contains an Active Directory domain named contoso.com. You have a failover cluster named Cluster1 that contains two nodes named Server1 and Server2. Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed. You plan to create two virtual machines that will run an application named App1. App1 will store data on a virtual hard drive named App1data.vhdx. App1data.vhdx will be shared by both virtual machines. The network contains the following shared folders:
– An SMB file share named Share1 that is hosted on a Scale-Out File Server.
– An SMB file share named Share2 that is hosted on a standalone file server.
– An NFS share named Share3 that is hosted on a standalone file server.
You need to ensure that both virtual machines can use App1data.vhdx simultaneously. What should you do? To answer, select the appropriate configurations in the answer area.
Answer:
Case Study 5: Contoso Ltd Case B (QUESTION 160 – QUESTION 168)
Background
Overview
Contoso, Ltd., is a software development company. The company has a main office in Seattle and branch offices that are located in Los Angeles and New Delhi. Contoso’s sales staff are all located in the Los Angeles office. Contoso’s software developers are all located in the New Delhi office.
Current Environment
The network for the Seattle office contains:
– 2 domain controllers with integrated DNS
– 200 Windows workstations
– 14-node Hyper-V cluster
– 1 file server with multiple shares
– 1 Active Directory Rights Management Services (AD RMS) cluster
The network for the Los Angeles office contains:
– 2 domain controllers with integrated DNS
– 100 Windows workstations
– 1 file server with multiple shares
The network for the New Delhi office contains:
– 2 domain controllers with integrated DNS
– 300 Windows workstations
– 10 Hyper-V servers that host 100 development virtual machines (VMs)
– 50 production virtual machines that are hosted in Azure
All the Contoso offices connect to each other by using VPN links, and each office is connected to the Internet. Contoso has a single Active Directory Domain Services (AD DS) domain named contoso.com. Contoso.com has a configured certification authority (CA). Contoso currently leverages System Center Virtual Machine Manager 2012 R2 to manage its virtual environment servers. Contoso uses an application named HRApp1 for its human resources (HR) department. HR users report that the application stops responding and must be restarted before they can continue their work.
Fabrikam Inc
Contoso has recently acquired Fabrikam. Inc. Fabrikam has a single office that is located in Seattle. Fabrikam has a single AD DS domain named fabrikam.com. The network for Fabrikam contains:
– 2 domain controllers with Active Directory-integrated DNS
– 150 Windows workstations
– 5 Hyper-V servers
– 1 file server with multiple shares
A two-way trust exists between Contoso.com and Fabrikam.com.
Business Requirements
Consolidation
Contoso must complete the consolidation of the Contoso and Fabrikam networks. The consolidation of the two networks must:
– Minimize all hardware and software costs.
– Minimize WAN traffic.
– Enable the users by providing self-service whenever possible.
Security
Contoso requires that all Windows client devices must be encrypted with BitLocker by using the Trusted Platform. The CA for the domain contoso.com must be designated as the resource forest. The domain fabrikam.com must leverage certificates that are issued by the domain contoso.com.
Other Information
HRApp1
Each time HRApp1 stops responding and is restarted, an incident must be created and associated with the existing problem ticket.
Development environment
You have the following requirements:
– Developers must be able to manage their own VM checkpoints.
– You must implement a disaster recovery strategy for development virtual machines.
Technical Requirements
Windows System Updates
You have the following system update requirements:
– Consolidate reporting of all software updates in all offices.
– Software updates must be applied to all Windows devices.
– Ensure the ability to report on update compliance.
Monitoring
You have the following monitoring requirements:
– Each time HRApp1 shows performance problems, ensure that a ticket is created.
– When performance problems are resolved, ensure that the ticket closes automatically.
Security
You have the following security requirements:
– Ensure that all documents are protected.
– Ensure that contoso.com domain users get use licenses for RMS-protected documents from the domain contoso.com.
– Ensure that fabrikam.com domain users get use licenses for RMS-protected documents from the domain contoso.com.
QUESTION 160
You need to ensure that the developers can manage their own virtual machines. Solution: You perform the following actions:
– In virtual machine manager, you create a new user role named DevUsers that used the Application Administrator profile.
– You add the virtual machines to the DevUsers role.
– You grant checkpoint permissions to the DevUsers role.
– You distribute the virtual machine manager console URL to the developers.
Does this meet the goal?
A. YES
B. NO
Answer: B
Download Free 70-414 PDF Dumps From Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpfmxzR3ZsVU52M0wxX2d6OWtDWjJSZVE5Tm81bEpDak5MQWlOTHBDdERCWXM (Explanation For Every Question Is Available!)
PassLeader 70-414 VCE Dumps Screenshots:
Download New 70-414 VCE Dumps From PassLeader: http://www.passleader.com/70-414.html (New Questions Are 100% Available and Wrong Answers Have Been Corrected!!!)