Pass 70-342 exam easily by learning PassLeader 70-342 exam dumps! PassLeader just updated the 231q 70-342 exam questions, the new 70-342 VCE or PDF practice tests cover all the real questions, which will help you passing 70-342 exam easily. What’s more, PassLeader’s new 70-342 VCE dumps and PDF dumps have corrected many wrong answers, which is not available in other free 70-342 VCE dumps, it will ensure you 100 percent passing 70-342 exam!
keywords: 70-342 exam,231q 70-342 exam dumps,231q 70-342 exam questions,70-342 pdf dumps,70-342 vce dumps,70-342 study guide,70-342 practice test,Microsoft Advanced Solutions of Microsoft Exchange Server 2013 Exam
P.S. Download Free 70-342 PDF Dumps and Preview PassLeader 70-342 VCE Dumps At The End Of This Post!!! (Ctrl+End)
QUESTION 91
The Internet link in the Tampa office will be unavailable during the weekend. You need to ensure that all outbound email messages are sent from the Charlotte office during the planned outage. What should you do?
A. Modify the cost of the Tampa SMTP Send connector.
B. Create a new mail exchanger (MX) record named SMTP2.fabrikam.com in the internal DNS zone.
C. Modify the smart host of the Tampa SMTP Send connector.
D. Modify the preference value of the fabrikam.com mail exchanger (MX) records.
Answer: C
QUESTION 92
Hotspot Question
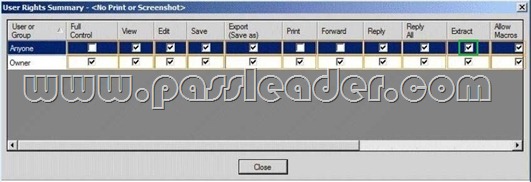
You need to resolve the IRM template issue. Which user right should you modify? To answer, select the appropriate user right in the answer area.
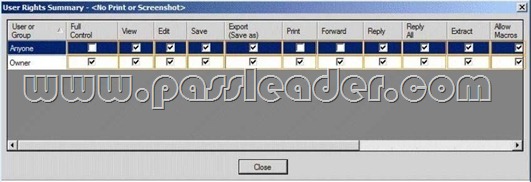
Answer:
QUESTION 93
You need to recommend a solution for the HR voice mail. The solution must meet the security requirements. What should you recommend?
A. Create a UM mailbox policy and associate the policy to UM1.
Configure the voice mail protection settings of the UM mailbox policy.
Create an auto attendant and link the auto attendant to UM1.
B. Create a UM mailbox policy and associate the policy to a new dial plan.
Configure the voice mail protection settings of the UM mailbox policy.
Create an auto attendant and link the auto attendant to the new dial plan.
C. Create a UM mailbox policy and associate the policy to a new dial plan.
Configure the voice mail protection settings of the UM mailbox policy.
Assign the UM mailbox policy to the mailbox of the HR department.
D. Create a UM mailbox policy and associate the policy to UM1.
Configure the voice mail protection settings of the UM mailbox policy.
Assign the UM1 mailbox policy to the mailbox of the HR department.
Answer: D
QUESTION 94
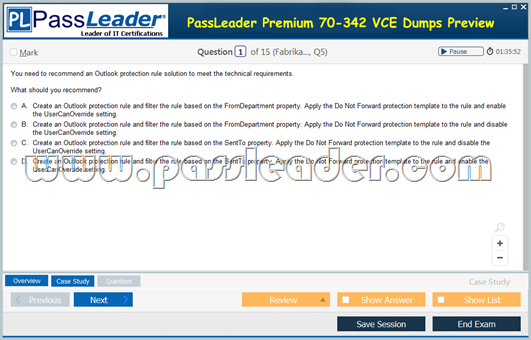
You need to recommend an Outlook protection rule solution to meet the technical requirements. What should you recommend?
A. Create an Outlook protection rule and filter the rule based on the FromDepartment property.
Apply the Do Not Forward protection template to the rule and enable the UserCanOverride setting.
B. Create an Outlook protection rule and filter the rule based on the FromDepartment property.
Apply the Do Not Forward protection template to the rule and disable the UserCanOverride setting.
C. Create an Outlook protection rule and filter the rule based on the SentTo property.
Apply the Do Not Forward protection template to the rule and disable the UserCanOverride setting.
D. Create an Outlook protection rule and filter the rule based on the SentTo property.
Apply the Do Not Forward protection template to the rule and enable the UserCanOverride setting.
Answer: B
QUESTION 95
Hotspot Question
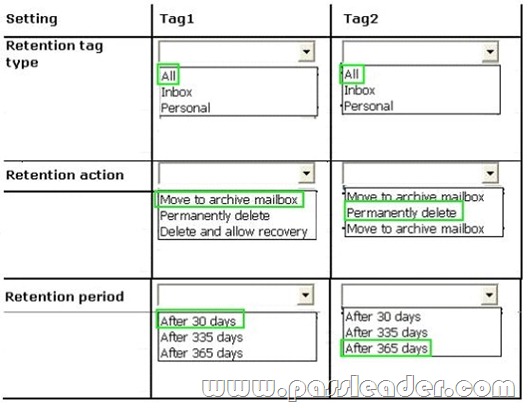
You plan to create two retention tags named Tag1 and Tag2. Tag1 will be used to move email messages to the Archive mailbox. Tag2 will be used to delete the email messages. You need to identify which settings must be configured in the retention tags to meet the technical requirements. How should you configure each retention tag? To answer, configure the appropriate options for each retention tag setting in the answer area.
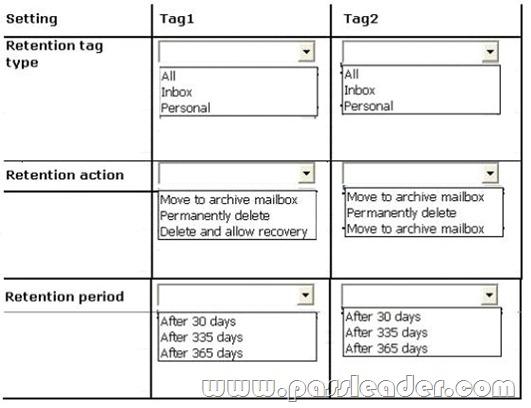
Answer:
QUESTION 96
Hotspot Question
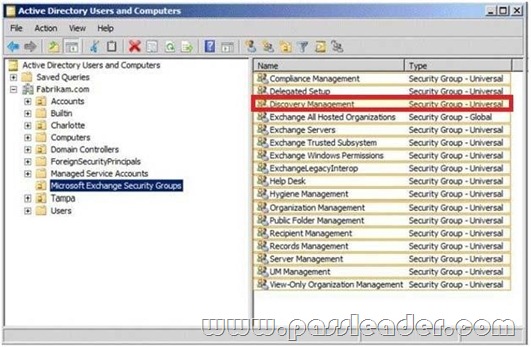
You need to ensure that the HR1 group can perform the tasks required to meet the technical requirements. To which group should you add HR1? To answer, select the appropriate group in the answer area.
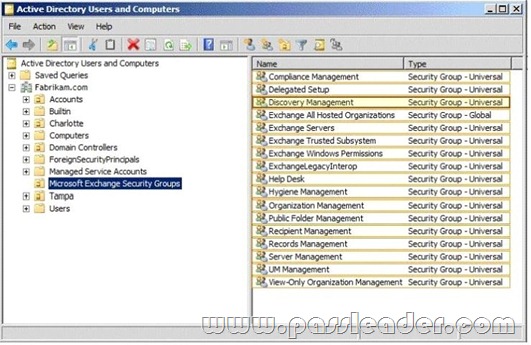
Answer:
QUESTION 97
You are evaluating the implementation of the planned static IP addresses for DAG1. You need to identify the appropriate IP addresses for DAG1. Which two IP addresses should you identify? (Each correct answer presents part of the solution. Choose two.)
A. 169.254.0.10
B. 192.168.1.10
C. 192.168.2.10
D. 192.168.10.10
E. 192.168.20.10
F. 224.0.0.10
Answer: BD
QUESTION 98
Drag and Drop Question
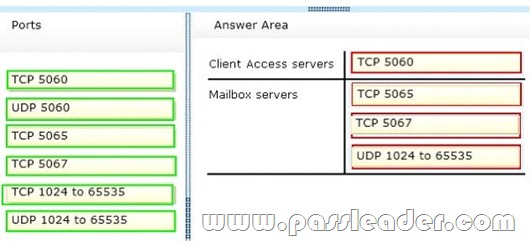
The security department implements a new firewall between the IP-PBX system and the servers in the Tampa office. You discover that SIP sessions cannot be established between the IP-PBX and EX1. You need to identify which ports must be opened between the IP-PBX and the Exchange Server 2013 servers. Which ports should you identify? To answer, drag the appropriate port or ports to the correct group of servers in the answer area. Each port or ports may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
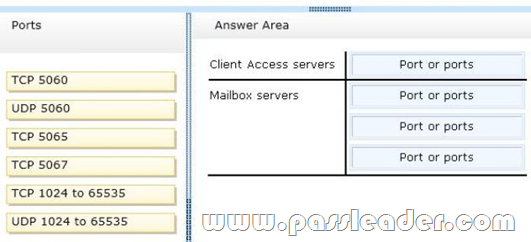
Answer:
QUESTION 99
You have a hybrid deployment of Exchange Server 2013 and Microsoft Office 365. The Exchange Server organization has a mailbox size limit of 2 GB. You need to provide engineers with the ability to retain certain email messages indefinitely. The solution must meet the following requirements:
– Ensure that the engineers can access the retained email messages by using Outlook Web App.
– Ensure that the retained email messages do not apply to the mailbox size limit of the engineers.
– Minimize the storage requirements of the on-premises servers.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From Office 365, create Archive mailboxes.
B. Instruct the engineers to create a personal folder.
C. Create a retention policy.
D. From the on-premises Exchange Server 2013 organization, create Archive mailboxes.
E. Create a data loss prevention (DLP) policy.
Answer: AC
QUESTION 100
You have a database availability group (DAG). The DAG is configured as shown in the following table.
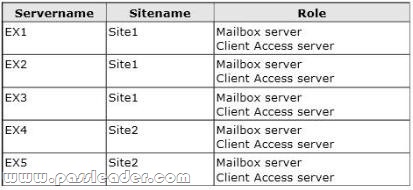
You need to prevent a split-brain condition if a restore operation of the DAG occurs. What should you do?
A. Deploy an alternate witness server to each site.
B. Modify the Datacenter Activation Coordination (DAC) mode.
C. Set the quorum model of the cluster to Node and Disk Majority.
D. Deploy another Mailbox server to Site2.
Answer: B
QUESTION 101
Hotspot Question
Your network contains two Active Directory sites named Sitel and Site2. Both sites contain an equal number of users. Each site contains two Exchange Server 2013 Mailbox servers. You need to recommend a high-availability solution that meets the following requirements:
– If a single Mailbox server fails, the active mailbox database copies on that server must fail over to a Mailbox server in the same site.
– If both Mailbox servers in the same site fail, the active mailbox databases copies must be switched over to the other site manually.
– If a WAN link fails, multiple copies of the same mailbox database must not be activated in both sites simultaneously.
How should you configure the database availability groups (DAGs)? (To answer, configure the appropriate options in the answer area.)
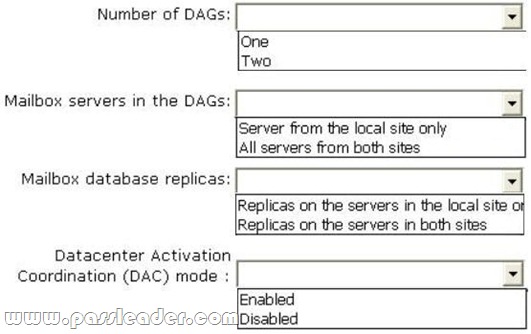
Answer:
QUESTION 102
Drag and Drop Question
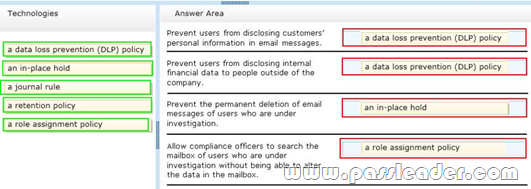
Contoso, Ltd., is a bank that has offices in North America and Europe. The company must comply with different regulations for North America and Europe. The company uses Information Right Management (IRM) to protect sensitive documents, such as internal financial reports. You need to recommend a compliance solution to meet the following requirements:
– Prevent users from disclosing customers’ personal information in email messages.
– Prevent users from disclosing internal financial data to people outside of the company.
– Prevent the permanent deletion of email messages of users who are under investigation.
– Allow compliance officers to search the mailbox of users who are under investigation without being able to alter the data in the mailbox.
Which technology should you recommend for each requirement? To answer, drag the appropriate technology to the correct requirement in the answer area. Each technology may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
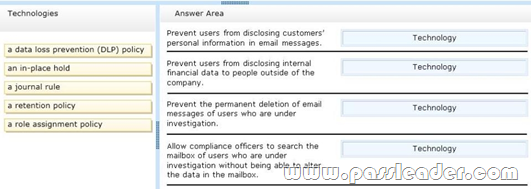
Answer:
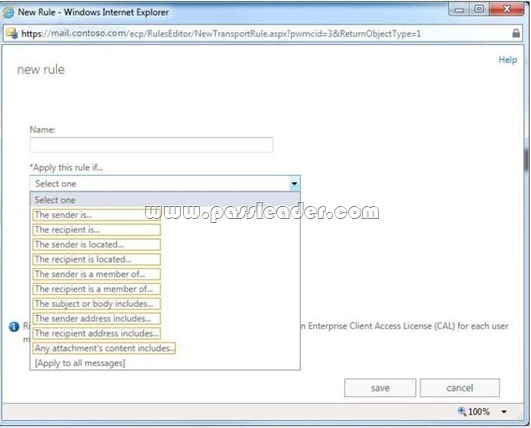
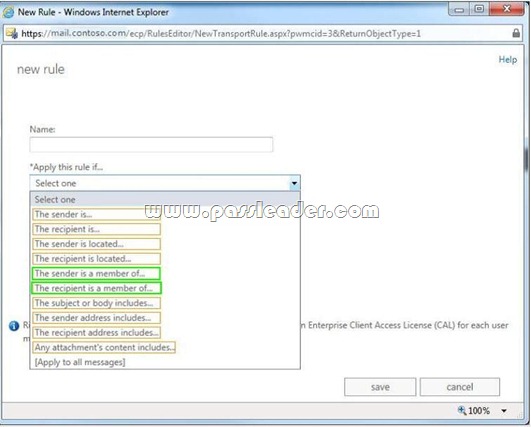
QUESTION 103
Hotspot Question
You have an Exchange Server 2013 organization. You need to create a single transport rule that prevents users in a group named Group1 from exchanging messages with users in a group named Group2. Which two options should you use? To answer, select the two appropriate options in the answer area.
Answer:
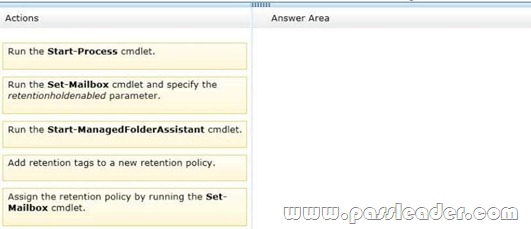
QUESTION 104
Drag and Drop Question
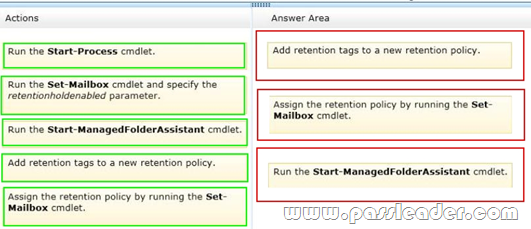
You have an Exchange Server organization. The organization contains servers that have Exchange Server 2010 and Exchange Server 2013 installed. A new compliance policy requires that all email messages remain stored for two years. You create two retention tags named Tag1 and Tag2. Tag1 moves the email messages to an Archive mailbox after one year. Tag2 permanently deletes the email messages after two years. You need to meet the compliance policy requirements. The solution must ensure that all email messages that are older than two years are removed as quickly as possible. Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Answer:
QUESTION 105
You have an Exchange Server 2013 organization. You need to ensure that a user named User1 can prevent the deletion of every email message that contains a specific word from all of the mailboxes. The solution must minimize the number of permissions assigned to User1. What should you do?
A. Add User1 to the Records Management management role group.
Instruct User1 to run the New-ManagedContentSettings cmdlet.
B. Add User1 to the Records Management management role group.
Instruct User1 to run the New-MailboxSearch cmdlet.
C. Add User1 to the Discovery Management management role group.
Instruct User1 to run the New-ManagedContentSettings cmdlet.
D. Add User1 to the Discovery Management management role group.
Instruct User1 to run the New-MailboxSearch cmdlet.
Answer: D
QUESTION 106
Your company has an Exchange Server 2013 organization named Contoso. A partner company has an Exchange Server 2013 organization named Fabrikam. Neither company has any trusts between their forests. Users from both organizations access their mailbox from the Internet by using Outlook Anywhere. You need to ensure that the users from both organizations can share free/busy information. Which two cmdlets should you run? (Each correct answer presents part of the solution. Choose two.)
A. New-AcceptedDomain
B. Add-AvailabilttyAddressSpace
C. Set-AvailabilityConfig
D. New-SharingPolicy
E. Add-ADPermission
Answer: BD
QUESTION 107
A company named Contoso, Ltd., has an Exchange Server 2013 organization. The primary SMTP suffix for all users is contoso.com. A company named Fabrikam, Inc., has an Exchange Server 2010 organization. The primary SMTP suffix for all users is fabrikam.com. The users in both organizations access their email by using Microsoft Outlook 2010 and Outlook Anywhere. All of the users work from domain-joined client computers that connect to the internal network. Contoso acquires Fabrikam. You establish a cross-forest trust between the Contoso forest and the Fabrikam forest. In fabrikam.com, you create a user named User1. In contoso.com, you create a linked mailbox for User1 and you set the primary SMTP address to [email protected]. User1 reports that Outlook 2010 fails to configure his mail profile automatically. User1 can manually configure his profile and connect to his mailbox. You need to ensure that users in fabrikam.com can find their mailboxes automatically. What should you do in contoso.com?
A. Create a DNS record named autodiscover.fabrikam.com.
Point the record to the virtual IP address of the Client Access servers.
B. Modify the ExternalURL of the Autodiscover virtual directory on the Exchange Servers 2013 servers.
C. Modify the Autodiscover Service Connection Point (SCP).
D. Run the Export-AutoDiscoverConfig cmdlet on an Exchange Server 2013 server.
Answer: D
QUESTION 108
You have an Exchange Server 2013 organization that contains 10 servers. You have a federation trust to the Microsoft Federation Gateway. The certificate in the trust relationship expires soon. You need to replace the certificate. The solution must minimize downtime. You purchase a new certificate. What should you do next?
A. On all of the Exchange servers, import the certificate, and then run the New- FederationTrust cmdlet.
B. On all of the Exchange servers, import the certificate, and then run the Set- OrganizationRelationship cmdlet.
C. On one of the Exchange servers, import the certificate, and then run the Set- FederationTmst cmdlet.
D. On one of the Exchange servers, import the certificate, and then run the Set- FederatedOrganizationldentifier cmdlet.
Answer: C
QUESTION 109
Drag and Drop Question
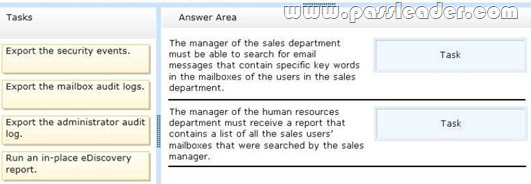
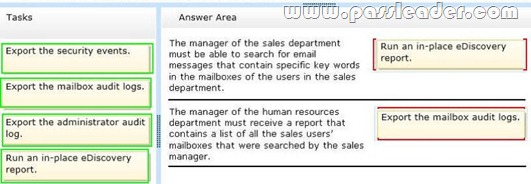
You work for a financial services company that has an Exchange Server 2013 organization. Mailbox audit logging is enabled for all mailboxes. The company identifies the following requirements for the sales department:
– The manager of the sales department must be able to search for email messages that contain specific key words in the mailboxes of the users in the sales department.
– The manager of the human resources department must receive a report that contains a list of all the sales users’ mailboxes that were searched by the sales manager.
You need to identify which tasks must be performed to meet the requirements. Which tasks should you identify? To answer, drag the appropriate task to the correct requirement in the answer area. Each task may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Answer:
QUESTION 110
You have an Exchange Server 2013 organization that contains one office in Los Angeles and one office in New York. All servers have the Mailbox server role and the Client Access server role installed and are members of a data availability group (DAG) named DAG1. The servers and databases are shown in the exhibit. (Click the Exhibit button.)
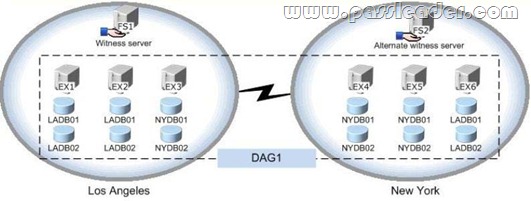
You need to ensure that if the active copy of LADB01 fails, a server in the same site will attempt to activate a copy of the database before a server in another site does. The solution must not influence the activation of other database copies. Which command should you run?
A. Set-databaseavailabilitygroupserver -identity dagl-alternatewitnessserverfs2
B. Set-mailboxserver-identity ex6 autodatabasemountdial bestavailability
C. Suspend-mailboxdatabasecopy-identity Iadb01\ex6 -activationonly
D. Set-mailboxdatabasecopy -identity Iadb01\ex2-activationpreferencel
Answer: D
QUESTION 111
Your company has offices in Montreal, New York, and Toronto. Each office is configured as an Active Directory site. The Montreal office has a site link to the New York office. The New York office has a site link to the Toronto office. You have an Exchange Server 2013 organization that contains five Mailbox servers. The organization is configured as shown in the exhibit. (Click the Exhibit button.)
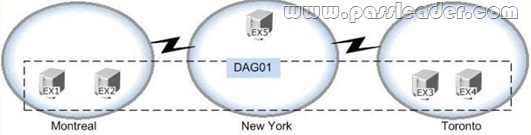
The servers in the Montreal and Toronto offices are members of a database availability group (DAG) named DAG01. DAG01 contains two databases name TOMBX and MTLMBX. MTLMBX is active on EX1 and contains all of the mailboxes of the users in the Montreal office. TOMBX is active on EX3 and contains all of the mailboxes of the users in the Toronto office. You need to ensure that all email messages transmitted between the Montreal users and the Toronto users are routed through EX5. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Run the Set-MailboxTransportService cmdlet on EX5.
B. Make EX5 the source server for all of the Send connectors.
C. Create a separate DAG for each of the Montreal and Toronto offices.
D. Add EXS to DAG01.
E. Configure the New York office as a hub site.
Answer: CE
QUESTION 112
You are a network administrator for a company named Contoso, Ltd. You install the Active Directory Rights Management Services server role on a server. The Active Directory Rights Management Services (AD RMS) server uses an internal certification authority (CA) for all certificates. You plan to provide users with the ability to use AD RMS to protect all of the email messages sent to a partner company named A.Datum Corporation. A.Datum does not have AD RMS deployed. You need to identify which components from the Contoso network must be accessible to A.Datum to ensure that the users at A.Datum can open protected messages. Which two components should you identify? (Each correct answer presents part of the solution. Choose two.)
A. The Active Directory domain controllers
B. The Client Access servers
C. The certificate revocation list (CRL)
D. The Mailbox servers
Answer: AC
QUESTION 113
You hire a junior administrator named Admin5. Admin5 is a member of the Recipient Management management role group. You discover that Admin5 created two new mailbox-enabled users by using the New-Mailbox command. You need to identify which management role provides Admin5 with the permissions to create new mailbox-enabled users. Which cmdlets should you run?
A. Get-ManagementRoleEntry and Get-RoleAssignmentPolicy
B. Get-Rolegroup and Get-ManagementRoleAssignment
C. Get-ManagementRoleEntry a-d Get-ManagementRoleAssignment
D. Get-RolegroupMember and Get-ManagementRoleAssignment
Answer: C
QUESTION 114
You have an Exchange Server 2013 organization that contains one Client Access server named EX1 and one Mailbox server named EX2. You have a perimeter network and an internal network. The perimeter network contains an Edge Transport server named EX3 that has Exchange Server 2010 installed. You need to ensure that all of the email messages sent to and received from the Internet are routed through the EX3. Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Allow SMTP traffic between EX3 and EX2.
B. Create an Edge Subscription.
C. Allow traffic over TCP 50636 from EX1 to EX3.
D. Allow SMTP traffic between EX3 and EX1.
E. Allow traffic over TCP 50636 from EX2 to EX3.
F. Modify the default Receive connector on EX2.
Answer: ABE
QUESTION 115
You are an administrator for a company named Contoso, Ltd. Contoso has an Exchange Server 2013 organization. Contoso has a partnership agreement with a company named A.Datum Corporation. A.Datum has an Exchange server 2013 organization. Both organizations have a federation trust to the Microsoft Federation Gateway. Users at Contoso plan to share their free/busy information with users at A.Datum. You need to recommend which tasks must be performed to ensure that the A.Datum users can see the free/busy information of the Contoso users. Which two actions should you recommend? (Each correct answer presents part of the solution. Choose two.)
A. In the Exchange Server organization of Contoso, configure directory synchronization.
B. In the Exchange Server organization of A. Datum, create a sharing policy.
C. In the Exchange Server organization of A. Datum, configure directory synchronization.
D. In the Exchange Server organization of Contoso, create an organization relationship.
E. In the Exchange Server organization of Contoso, create a sharing policy.
F. In the Exchange Server organization of A. Datum, create an organization relationship.
Answer: DE
QUESTION 116
Drag and Drop Question
You have a server that has Exchange Server 2013 installed. You plan to deploy Unified Messaging (UM) to all users. You have two UM IP gateways named GW1 and GW2. You create, and then associate a new UM dial plan for each IP gateway. The IP gateways are configured as shown in the following table.
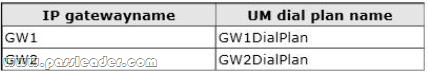
You need to recommend a solution that meets the following security requirements:
– All voice traffic received by GW1 must be encrypted.
– All voice traffic received by GW2 must be unencrypted.
– All signaling traffic to GW1 and GW2 must be encrypted.
Which security settings should you recommend configuring for each dial plan? To answer, drag the appropriate security setting to the correct UM dial plan in the answer area. Each security setting may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Answer:
QUESTION 117
You have an Exchange Server 2013 organization that contains multiple Hub Transport servers. You need to recommend a message hygiene solution to meet the following requirements:
– Block servers that are known to send spam
– Minimize administrative effort
What should you recommend?
A. an IP Block list
B. IP Block list providers
C. recipient filtering
D. sender filtering
Answer: B
QUESTION 118
You have an Exchange Server 2010 organization named adatum.com. All public folders are stored on a server named EX5. You deploy a new server named EX6. EX6 has Exchange Server 2013 installed. You move all mailboxes to EX6. You need to move the public folders to EX6. The solution must ensure that users can access the public folders after EX5 is decommissioned. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. On EX6, create a public folder mailbox.
B. On EX6, run the New-PublicFolderMigrationRequest cmdlet.
C. On EX5, modify the replication partners for all of the public folders.
D. On EX6, run the New-SiteMailboxProvisioningPolicy cmdlet.
E. On EX5, assign the FolderOwner permission to the Public Folder Management management role group for all of the public folders.
F. On EX6, run the MoveAllReplicas.ps1 script.
Answer: AB
QUESTION 119
Your company has a main office and a branch office. An Active Directory site exits for each office. The offices are connected by a WAN link. You plan to deploy Exchange Server 2013 in each site. You need to identify the number of Exchange servers required to meet the following requirements:
– Maintain user access to mailboxes if a single server fails
– Use the minimize account of Exchange servers in each site
How many servers should you deploy in each site?
A. 1
B. 2
C. 3
D. 4
Answer: B
QUESTION 120
You have an Exchange Server 2010 organization. A user named User1 connects to his mailbox using Microsoft Office Outlook. User1 reports that he is unable to send encrypted email messages to an external recipient named User2. You verify that User1 and User2 have email encryption certificates. You need to ensure that User1 can send encrypted email messages to User2. What should you do first?
A. Instruct User2 to add a delegate.
B. Instruct User2 to send a signed email message to User1.
C. Instruct User1 to send a signed email message to User2.
D. Instruct User1 to modify the sensitivity settings of the email message.
Answer: B
Download Free 70-342 PDF Dumps From Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpfnExREVzWWtnTGZYZDhiVm1ESjV2dkgwU09EOExRMloxUE95aUdnWC1lUU0 (Explanation For Every Question Is Available!)
PassLeader 70-342 VCE Dumps Screenshots:
Download New 70-342 VCE Dumps From PassLeader: http://www.passleader.com/70-342.html (New Questions Are 100% Available and Wrong Answers Have Been Corrected!!!)