[2016-NEW!] Download PassLeader NSE5 VCE Practice Test And PDF Study Guide Collection (Question 21 – Question 40)
Want To Pass The New NSE5 Exam Easily? DO NOT WORRY! PassLeader now is supplying the latest and 100 percent pass ensure 240q NSE5 PDF dumps and VCE dumps, the new updated NSE5 braindumps are the most accurate with all the new changed NSE5 exam questions, it will help you passing NSE5 exam easily and quickly. Now visit the our site passleader.com and get the valid 240q NSE5 VCE and PDF exam questions and FREE VCE PLAYER! keywords: NSE5 exam,240q NSE5 exam dumps,240q NSE5 exam questions,NSE5 pdf dumps,NSE5 vce dumps,NSE5 braindumps,NSE5 practice tests,NSE5 study guide,Fortinet Network Security Analyst Exam P.S. Download Free NSE5 PDF Dumps and Get Premium PassLeader NSE5 VCE Dumps At The End Of This Post!!! (Ctrl+End) QUESTION 21
A firewall policy has been configured for the internal email server to receive email from external parties through SMTP. Exhibits A and B show the antivirus and email filter profiles applied to this policy.
Exhibit A:
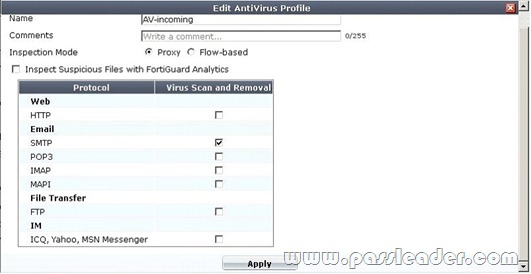 Exhibit B:
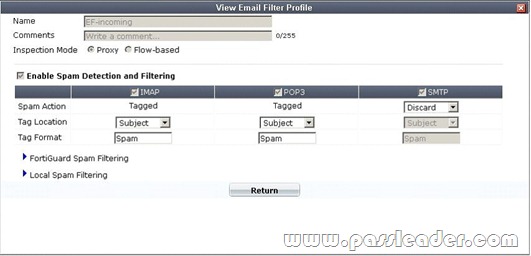
What is the correct behavior when the email attachment is detected as a virus by the FortiGate antivirus engine? A. The FortiGate unit will remove the infected file and deliver the email with a replacement message to alert the recipient that the original attachment was infected.
B. The FortiGate unit will reject the infected email and the sender will receive a failed delivery message.
C. The FortiGate unit will remove the infected file and add a replacement message. Both sender and recipient are notified that the infected file has been removed.
D. The FortiGate unit will reject the infected email and notify the sender. Answer: B QUESTION 22
In order to match an identity-based policy, the FortiGate unit checks the IP information. Once inside the policy, the following logic is followed: A. First, a check is performed to determine if the user's login credentials are valid. Next, the user is checked to determine if they belong to any of the groups defined for that policy. Finally, user restrictions are determined and port, time, and UTM profiles are applied.
B. First, user restrictions are determined and port, time, and UTM profiles are applied. Next, a check is performed to determine if the user's login credentials are valid. Finally, the user is checked to determine if they belong to any of the groups defined for that policy.
C. First, the user is checked to determine if they belong to any of the groups defined for that policy. Next, user restrictions are determined and port, time, and UTM profiles are applied. Finally, a check is performed to determine if the user's login credentials are valid. Answer: A QUESTION 23
An administrator configures a FortiGate unit in Transparent mode on the 192.168.11.0 subnet. Automatic Discovery is enabled to detect any available FortiAnalyzers on the network. Which of the following FortiAnalyzers will be detected? (Select all that apply.) A. 192.168.11.100
B. 192.168.11.251
C. 192.168.10.100
D. 192.168.10.251 Answer: AB QUESTION 24
An end user logs into the full-access SSL VPN portal and selects the Tunnel Mode option by clicking on the "Connect" button. The administrator has enabled split tunneling.
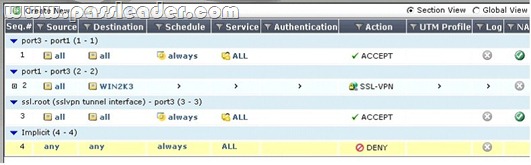
Given that the user authenticates against the SSL VPN policy shown in the image below, which statement below identifies the route that is added to the client's routing table. A. A route to destination matching the `WIN2K3' address object.
B. A route to the destination matching the `all' address object.
C. A default route.
D. No route is added. Answer: A QUESTION 25
Which of the following components are contained in all FortiGate units from the FG50 models and up? (Select all that apply.) A. FortiASIC content processor.
B. Hard Drive.
C. Gigabit network interfaces.
D. Serial console port. Answer: AD QUESTION 26
Which of the following pieces of information can be included in the Destination Address field of a firewall policy? A. An IP address pool, a virtual IP address, an actual IP address, and an IP address group.
B. A virtual IP address, an actual IP address, and an IP address group.
C. An actual IP address and an IP address group.
D. Only an actual IP address. Answer: B QUESTION 27
DLP archiving gives the ability to store session transaction data on a FortiAnalyzer unit for which of the following types of network traffic? (Select all that apply.) A. SNMP
B. IPSec
C. SMTP
D. POP3
E. HTTP Answer: CDE QUESTION 28
Which of the following products can be installed on a computer running Windows XP to provide personal firewall protection, antivirus protection, web and mail filtering, spam filtering, and VPN functionality? A. FortiGate
B. FortiAnalyzer
C. FortiClient
D. FortiManager
E. FortiReporter Answer: C QUESTION 29
A FortiGate 100 unit is configured to receive push updates from the FortiGuard Distribution Network, however, updates are not being received. Which of the following statements are possible reasons for this? (Select all that apply.) A. The external facing interface of the FortiGate unit is configured to use DHCP.
B. The FortiGate unit has not been registered.
C. There is a NAT device between the FortiGate unit and the FortiGuard Distribution Network.
D. The FortiGate unit is in Transparent mode. Answer: ABC QUESTION 30
Which of the following statements describes the method of creating a policy to block access to an FTP site? A. Enable Web Filter URL blocking and add the URL of the FTP site to the URL Block list.
B. Create a firewall policy with destination address set to the IP address of the FTP site, the Service set to FTP, and the Action set to Deny.
C. Create a firewall policy with a protection profile containing the Block FTP option enabled.
D. None of the above. Answer: B QUESTION 31
Which of the following statements regarding Banned Words are correct? (Select all that apply.) A. The FortiGate unit can scan web pages and email messages for instances of banned words.
B. When creating a banned word list, an administrator can indicate either specific words or patterns.
C. Banned words can be expressed as simple text, wildcards or regular expressions.
D. Content is automatically blocked if a single instance of a banned word appears.
E. The FortiGate unit updates banned words on a periodic basis. Answer: ABC QUESTION 32
Which of the following items is NOT a packet characteristic matched by a firewall service object? A. ICMP type and code
B. TCP/UDP source and destination ports
C. IP protocol number
D. TCP sequence number Answer: D QUESTION 33
Which of the following network protocols are supported for administrative access to a FortiGate unit? A. HTTPS, HTTP, SSH, TELNET, PING, SNMP
B. FTP, HTTPS, NNTP, TCP, WINS
C. HTTP, NNTP, SMTP, DHCP
D. Telnet, FTP, RLOGIN, HTTP, HTTPS, DDNS
E. Telnet, UDP, NNTP, SMTP Answer: A QUESTION 34
Which of the following spam filtering methods are supported on the FortiGate unit? (Select all that apply.) A. IP Address Check
B. Open Relay Database List (ORDBL)
C. Black/White List
D. Return Email DNS Check
E. Email Checksum Check Answer: ABCDE QUESTION 35
Which of the following statements are correct regarding URL filtering on the FortiGate unit? (Select all that apply.) A. The allowed actions for URL Filtering include Allow, Block and Exempt.
B. The allowed actions for URL Filtering are Allow and Block.
C. The FortiGate unit can filter URLs based on patterns using text and regular expressions.
D. Any URL accessible by a web browser can be blocked using URL Filtering.
E. Multiple URL Filter lists can be added to a single protection profile. Answer: AC QUESTION 36
Which of the following items represent the minimum configuration steps an administrator must perform to enable Data Leak Prevention for traffic flowing through the FortiGate unit? (Select all that apply.) A. Assign a DLP sensor in a firewall policy.
B. Apply one or more DLP rules to a firewall policy.
C. Enable DLP globally using the config sys dlp command in the CLI.
D. Define one or more DLP rules.
E. Define a DLP sensor.
F. Apply a DLP sensor to a DoS sensor policy. Answer: ADE QUESTION 37
Which of the following items does NOT support the Logging feature? A. File Filter
B. Application control
C. Session timeouts
D. Administrator activities
E. Web URL filtering Answer: C QUESTION 38
An administrator wants to assign a set of UTM features to a group of users. Which of the following is the correct method for doing this? A. Enable a set of unique UTM profiles under "Edit User Group".
B. The administrator must enable the UTM profiles in an identity-based policy applicable to the user group.
C. When defining the UTM objects, the administrator must list the user groups which will use the UTM object.
D. The administrator must apply the UTM features directly to a user object. Answer: B QUESTION 39
In which order are firewall policies processed on the FortiGate unit? A. They are processed from the top down as they appear in Web Config.
B. They are processed based on the policy ID number shown in the left hand column of the policy window.
C. They are processed using a policy hierarchy scheme that allows for multiple decision branching.
D. They are processed based on a priority value assigned through the priority column in the policy window. Answer: A QUESTION 40
Which of the following statements is correct regarding URL Filtering on the FortiGate unit? A. The FortiGate unit can filter URLs based on patterns using text and regular expressions.
B. The available actions for URL Filtering are Allow and Block.
C. Multiple URL Filter lists can be added to a single Web filter profile.
D. A FortiGuard Web Filtering Override match will override a block action in the URL filter list. Answer: A Download Free NSE5 PDF Dumps From Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpU0FrbTh1X3JMSmM Download New NSE5 VCE Dumps From PassLeader: http://www.passleader.com/nse5.html (New Questions Are 100% Available and Wrong Answers Have Been Corrected!!!)
|


