[2016-NEW!] Do Not Miss 70-342 Exam Dumps Shared By PassLeader -- 100% Exam Pass Guarantee (Question 61 – Question 90)
Where Download New Free 70-342 Exam Dumps? As we all konw that new 70-342 exam is difficult to pass, if you cannot get the valid 70-342 exam questions, you will fail the 70-342 exam, but DO NOT WORRY! Nowdays, PassLeader has published the newest 231q 70-342 vce dumps and pdf dumps, in PassLeader's new 231q 70-342 braindumps, you can get all the new questions and answers, it is 100% vaild and will help you achieving 70-342 exam certification quickly. keywords: 70-342 exam,231q 70-342 exam dumps,231q 70-342 exam questions,70-342 pdf dumps,70-342 vce dumps,70-342 study guide,70-342 practice test,Microsoft Advanced Solutions of Microsoft Exchange Server 2013 Exam P.S. Download Free 70-342 PDF Dumps and Preview PassLeader 70-342 VCE Dumps At The End Of This Post!!! (Ctrl+End) QUESTION 61
Drag and Drop Question
You have an Exchange Server organization named adatum.com. The organization contains servers that have Exchange Server 2010 and Exchange Server 2013 installed. The company executives require that all email messages remain stored for three years. You create two retention tags named Ret1 and Ret2. Ret1 moves the email messages to an Archive mailbox after one year. Ret2 permanently deletes the email messages after three years. You need to meet the company executives' requirements. The solution must ensure that all email messages that are older than two years are removed as quickly as possible. Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
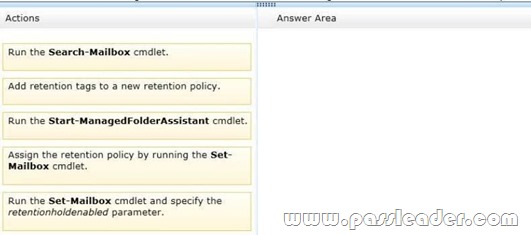 Answer:
 QUESTION 62
You have an Exchange Server 2013 organization named adatum.com. The organization contains five Mailbox servers. You need to prevent a user named User8 from permanently deleting an email message in his mailbox. What should you do on the mailbox of User8? A. Configure an in-place hold.
B. Create an Archive mailbox.
C. Configure a retention hold.
D. Create a Retention tag. Answer: A QUESTION 63
You have an Exchange Server 2013 organization named adatum.com. You have a database availability group (DAG) that contains four Exchange servers named Server1, Server2, Server3, and Server4. The file share witness is on a server named Share1. The organization has two Send connectors. The Send connectors are configured as shown in the following table.
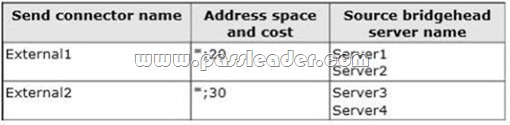
Users report that email sent to external recipients is not being received. You discover that outbound email messages are queued on Server3 and Server4. You need to ensure that all of the email messages queued on Server3 and Server4 are delivered to the Internet as quickly as possible. What should you do? A. Modify the cost of External.
B. Disable External1.
C. Modify the list of source bridgehead servers of External2.
D. Modify the cost of External1. Answer: B QUESTION 64
You are a network administrator for a company named Humongous Insurance. Humongous Insurance has an Active Directory forest that contains two domains. You install the Active Directory Rights Management Services server role on a server named ADRMS1. The Active Directory Rights Management Services (AD RMS) server uses an internal certification authority (CA) for all certificates. You plan to provide users with the ability to use AD RMS to protect all of the email messages sent to a partner company named Contoso, Ltd. Contoso does not have AD RMS deployed. You need to identify which components from the Humongous Insurance network must be accessible to Contoso to ensure that the users at Contoso can open protected messages. Which two components should you identify? (Each correct answer presents part of the solution. Choose two.) A. the AD RMS cluster
B. the certificate revocation list (CRL)
C. the Active Directory domain controllers
D. the Client Access servers
E. the Mailbox servers
F. the Global Catalog servers Answer: BC QUESTION 65
You have an Exchange Server organization that contains four servers. The servers are configured as shown in the following table.
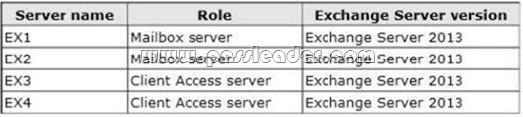
You are deploying Unified Messaging (UM). You create a dial plan named UMPIan1 and a UM mailbox policy named UMPlan Mailbox Policy. You need to ensure that all voice mail sent to the existing extension of a user is delivered to the user's mailbox. Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.) A. Create a UM hunt group.
B. Create a UM IP gateway.
C. Configure the IP-PBX to route calls to EX3 and EX4.
D. Configure the IP-PBX to route calls to EX1 and EX2.
E. Assign EX1 and EX2 to UMPIan1.
F. Assign EX3 and EX4 to UMPIan1. Answer: ABC QUESTION 66
Drag and Drop Question
You have an Exchange Server 2013 organization that contains two Mailbox servers and two Client Access servers. You have an Active Directory Rights Management Services (AD RMS) cluster. Information Rights Management (IRM) is enabled for the Exchange Server organization. All company executives are in a security group named Execs. All of the executives use smartphones that are managed by using a mobile device mailbox policy. The executives frequently read IRM-protected email messages by using Microsoft Outlook. You need to ensure that the executives can read the IRM-protected messages on their smartphone. Which task should you perform in each environment? (To answer, drag the appropriate tasks to the correct environments. Each task may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
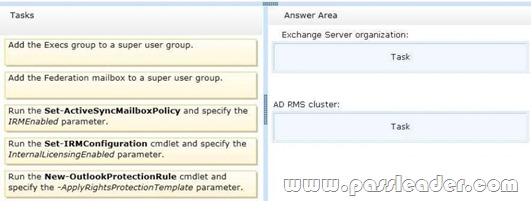 Answer:
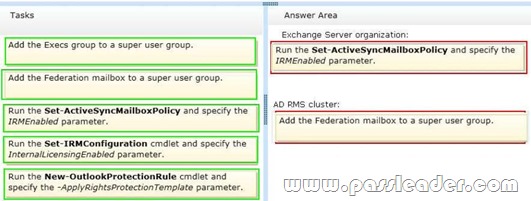 QUESTION 67
Drag and Drop Question
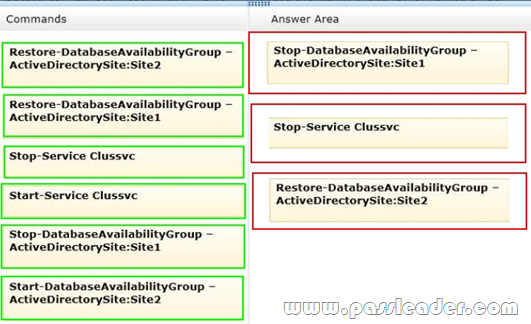
Your company has two offices. Each office is configured as an Active Directory site. The sites are named Site1 and Site2. You have an Exchange Server 2013 organization that is configured as shown in the following exhibit. (Click the Exhibit button.)
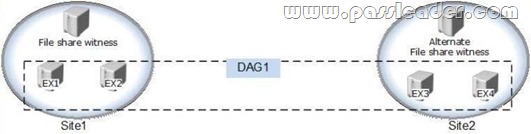
Datacenter Activation Coordination (DAC) mode is enabled on the database availability group (DAG) named DAG1. You are testing a site failover by shutting down all of the servers in Site1. You need to mount the databases in Site2. Which three commands should you run in sequence? (To answer, move the appropriate three commands from the list of commands to the answer area and arrange them in the correct order.)
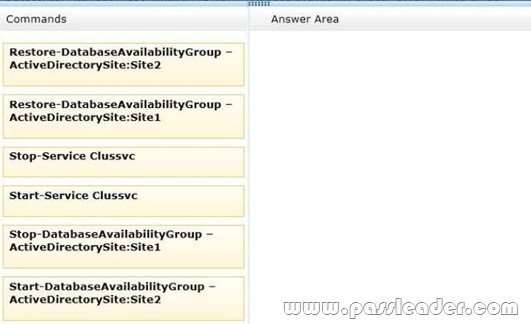 Answer:
 QUESTION 68
Drag and Drop Question
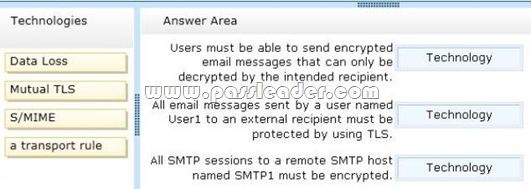
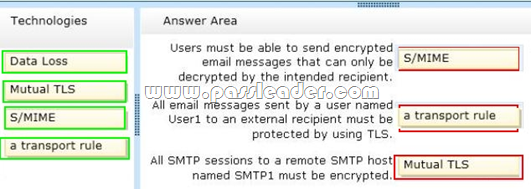
You have an Exchange Server 2013 organization. Your company identifies the following security requirements:
- Users must be able to send encrypted email messages that can only be decrypted by the intended recipient.
- All email messages sent by a user named User1 to an external recipient must be protected by using TLS.
- All SMTP sessions to a remote SMTP host named SMTP1 must be encrypted.
You need to recommend which technology must be used to meet each requirement. Which technologies should you recommend? (To answer, drag the appropriate technologies to the requirements in the answer area. Each technology may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
 Answer:
 QUESTION 69
Hotspot Question
Your company has a main office and a disaster recovery site. An Active Directory site named MainSite exists for the main office. An Active Directory site named DRSite exists for the disaster recovery site. The two sites connect to each other by using a WAN link. All users work in the main office. You have an Exchange Server 2013 organization. The organization contains six servers. The servers are configured as shown in the following table.
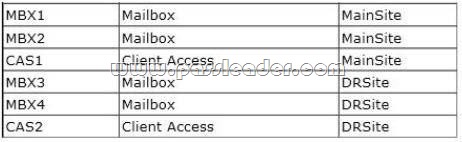
All of the Mailbox servers are members of a database availability group (DAG) named DAG1. After a WAN link failure, you discover that all of the active mailbox database copies are located on MBX3, even though MBX1 and MBX2 are still running. You need to prevent an automatic failover of DAG1 if the WAN link between the two sites fails but the servers in both sites are still running. The solution must prevent two active copies of the same database. What should you do? (To answer, select the appropriate options in the answer area.)
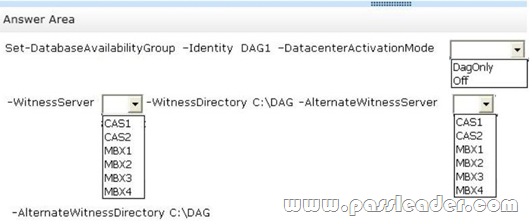 Answer:
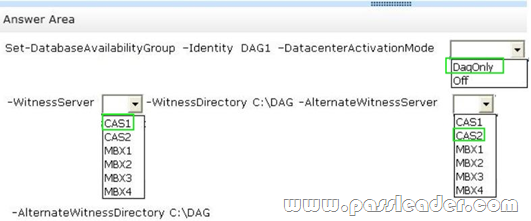 QUESTION 70
You have an Exchange Server 2010 organization that contains three servers. The servers are configured as shown in the following table.
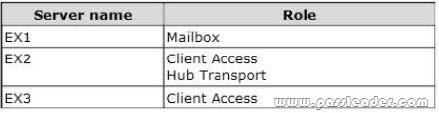
Microsoft Outlook is configured to connect to an FQDN of mail.adatum.com. Mail.adatum.com resolves to the IP address of a Layer 7 hardware load balancer. The hardware load balancer is configured to send traffic to EX2 and EX3. You deploy an Exchange Server 2013 Mailbox server and an Exchange Server 2013 Client Access server. You plan to migrate all mailboxes to Exchange Server 2013. You need to recommend a solution to ensure that users can access their mailbox on EX1 or EX4 during the migration. What should you do? A. Create a Client Access server array that contains EX1 and EX5.
B. Modify the autodiscover.contoso.com resource record to point to EX5.
C. Modify the properties of the hardware load balancer to point to EX5.
D. Create a DNS record named legacy.contoso.com in the internal DNS zone. Answer: C QUESTION 71
Your company has three data centers. The data centers are located in Montreal, New York, and Seattle. You have an Exchange Server 2013 organization that contains six servers. The servers are configured as shown in the following table.
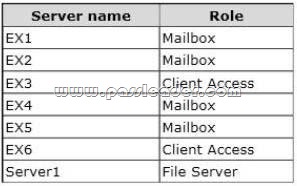
The organization is configured as shown in the following exhibit. (Click the Exhibit button.)
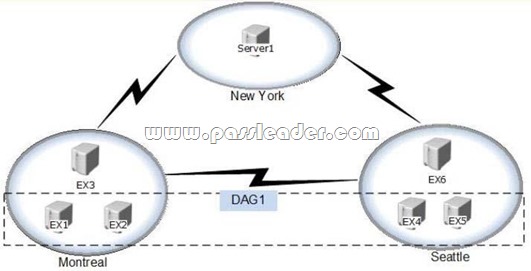
The file share witness for DAG1 is located on EX3. You plan to implement site resiliency and use a single name space named mail.contoso.com. You need to recommend a solution to minimize the amount of time that the Exchange Server services are unavailable if either the data center in Montreal or the data center in Seattle fails. Which two tasks should you recommend performing? (Each correct answer presents part of solution. Choose two.) A. Deploy a hardware load balancer to EX3 and EX6.
B. Create two DNS host (A) records for mail.contoso.com.
C. Configure EX6 as an alternate file share witness.
D. Move the file share witness to Server1. Answer: AD QUESTION 72
You have an Exchange Server 2013 organization. You create a data loss prevention (DLP) policy. The mode of the DLP policy is set to Enforce. You need to ensure that email messages containing social security numbers from the United States are blocked. Which two possible rules achieve this goal? (Each correct answer presents a complete solution. Choose two.) A. U.S. State Breach: Allow Override
B. U.S. State Breach: Scan email sent outside - low count
C. U.S. State Breach: Scan email sent outside - high count
D. U.S. State Breach: Scan text limit exceeded
E. U.S. State Breach: Attachment not supported Answer: BC QUESTION 73
You have an Exchange Server 2013 organization. You purchase a Microsoft Office 365 subscription and configure a hybrid deployment. The network contains an SMTP relay server named smarthost.contoso.com. The server is configured to use a certificate that has a subject name of smarthost.contoso.com. All users have Microsoft Outlook 2013 installed on their client computer. Outlook 2013 is configured to connect to mail.contoso.com. All Exchange servers have a certificate that has a subject name of mail.contoso.com. You discover that email messages sent from on-premises users are not delivered to Office 365 recipients. You discover that the Send connector for Office 365 uses a smart host of smarthost.contoso.com. You need to ensure that the on-premises users can send email messages to the Office 365 recipients. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.) A. Run the Hybrid Configuration Wizard again.
B. Configure the Microsoft Exchange Online Protection (EOP) Send connector to use smarthost.contoso.com.
C. Configure the centralized mail transport option.
D. Remove the smart host from the Send connector.
E. Assign a certificate that has a subject name of smarthost.contoso.com to the Send connector. Answer: AE QUESTION 74
You have a server named Server1 that has Exchange Server 2013 installed. Users access their mailbox by using Microsoft Outlook 2010 and Outlook Web App. You enable auditing for all of the mailboxes. You need to identify when a mailbox is accessed by someone other than the owner of the mailbox. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.) A. Export the administrator audit log.
B. Run an administrator role group report.
C. Export the mailbox audit log.
D. Run a non-owner mailbox access report.
E. Review the security event log. Answer: CD QUESTION 75
Hotspot Question
Your company implements Exchange Server 2013 Unified Messaging (UM). The company uses an auto attendant. You need to ensure that when calls are routed to the auto attendant, callers can press 0 to reach a receptionist. Which option should you configure from the UM Auto Attendant window? To answer, select the appropriate option in the answer area.
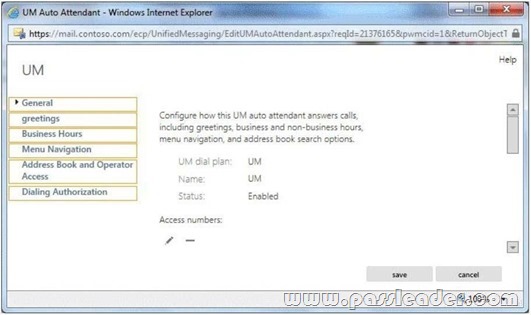 Answer:
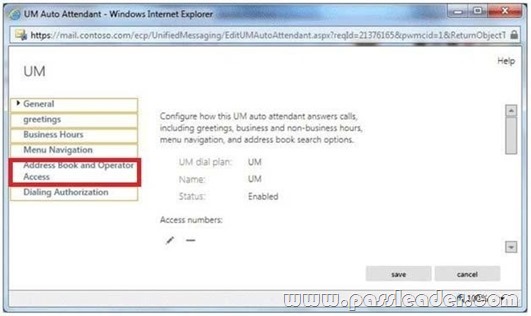 QUESTION 76
Hotspot Question
You have an Exchange Server organization that contains four servers. The servers are configured as shown in the following table.
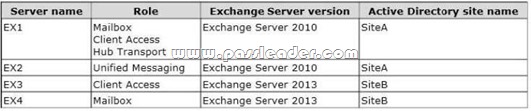
SiteA contains an IP gateway that uses a dial plan named Dialplan1. SiteB contains a Lync Server 2013 server that uses a dial plan named Dialplan2. You plan to migrate all Unified Messaging (UM) functionalities to Exchange Server 2013. You need to identify which tasks must be performed to complete the migration. Which tasks should you identify? (To answer, select the tasks that are required and not required in the answer area.)
 Answer:
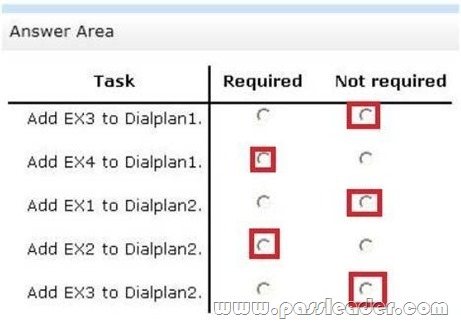 QUESTION 77
Hotspot Question
You have an Exchange Server 2013 organization. All users are enabled for Unified Messaging (UM) and access their voice mail by using Microsoft Lync 2010. Callers report that when they press a key to dial an external telephone number, they hear a message indicating that the intended destination cannot be reached. You need to ensure that the callers can reach the external number successfully. What should you modify? To answer, select the appropriate object in the answer area.
 Answer:
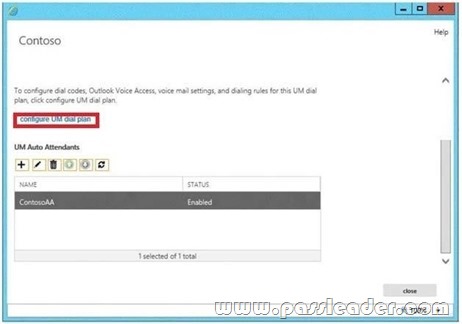 QUESTION 78
You have an Exchange Server 2013 organization. You successfully migrate the public folders from a previous version of Exchange Server. You discover that one of the public folder mailboxes almost reached its quota size. You need to move some of the public folders in the public folder mailbox to another public folder mailbox. What should you run? A. Update-PublicFolderMailbox
B. New-PublicFolderMoveRequest
C. New-PublicFolderMigrationRequest
D. Set-PublicFolderMailbox Answer: B QUESTION 79
Your company has three offices. Each office has 1,000 users and is configured as an Active Directory site. Each site connects directly to the Internet. The network contains six servers that have Exchange Server 2013 installed. The servers are configured as shown in the following table.
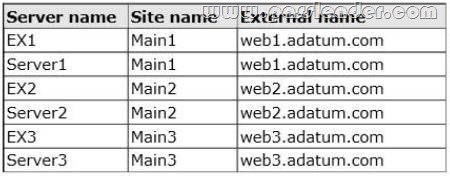
An administrator performs a datacenter switchover by changing the DNS record for webl.adatum.com to point to the IP address of web2.adatum.com. Users from Main1 report that when they connect to Outlook Web App, they receive a certificate warning message. You need to recommend a solution to ensure that the users do not receive a certificate warning message when a datacenter switchover is performed. What should you include in the recommendation? A. Three host headers for the Default Web Site on each Client Access server
B. One certificate that contains all of the external names as subject alternative names
C. Three certificates that each contains one of the external names
D. An external URL for each Client Access server set to $null Answer: B QUESTION 80
You have an Exchange Server 2010 organization named adatum.com. All public folders are stored on a server named EX5. You deploy a new server named EX6. EX6 has Exchange Server 2013 installed. You move all mailboxes to EX6. You need to move the public folders to EX6. The solution must ensure that users can access the public folders after EX5 is decommissioned. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.) A. On EX6, create a public folder mailbox.
B. On EX6, run the New-PublicFolderMigrationRequest cmdlet.
C. On EX5, modify the replication partners for all of the public folders.
D. On EX6, run the New-SiteMailboxProvisioningPolicy cmdlet.
E. On EX5, assign the FolderOwner permission to the Public Folder Management management role group for all of the public folders.
F. On EX6, run the MoveAllReplicas.ps1 script. Answer: AB QUESTION 81
You have an Exchange Server 2013 organization that contains a database available group (DAG) named DAG1. DAG1 contains three Mailbox servers named Server1, Server2, and Server3. DAG1 contains a mailbox database copy named DB1. You implement a lagged copy of DB1 on Server3. The copy lag time is seven days. You need to ensure that copies of successfully processed email messages are stored on Server1 and Server2 for seven days. What should you modify? A. The Shadow Redundancy settings
B. The Safety Net settings
C. The settings of DAG1
D. The settings of DB1 Answer: B QUESTION 82
You have an Exchange Server 2013 organization. All users are issued certificates from an internal certification authority (CA). Users who have a laptop can access their mailbox from the Internet by using Outlook Anywhere. When the users attempt to view or to create digitally signed email messages while they are connected to the Internet, the users receive a warning message. When the users use their laptop on the internal network, the users do not receive a warning message. You need to ensure that the users can send and receive digitally signed email messages without receiving a warning message. What should you do? A. Publish the root certificate of the CA to a server that is accessible from the Internet.
B. Publish the certificate revocation list (CRL) to a server that is accessible from the Internet.
C. Install a trusted root CA certificate on all Client Access servers.
D. Install a trusted root CA certificate on all of the laptops. Answer: B QUESTION 83
You have an Exchange Server 2013 organization. You successfully migrate the public folders from a previous version of Exchange Server. You discover that one of the public folder mailboxes almost reached its quota size. You need to move some of the public folders in the public folder mailbox to another public folder mailbox. What should you run? A. Set-PublicFolderMailbox
B. Merge PublicFolderMailbox.ps1
C. Split PublicFolderMailbox.ps1
D. New-PublicFolderMigrationRequest Answer: C QUESTION 84
Hotspot Question
Your network contains two Active Directory sites named Site1 and Site2. You have an Exchange Server 2013 organization that contains six servers. The servers are configured as shown in the following table.
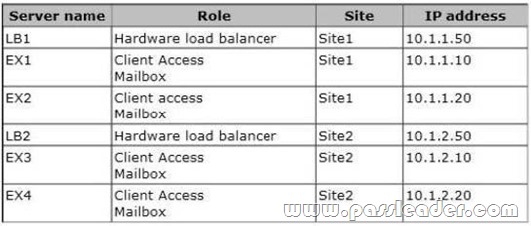
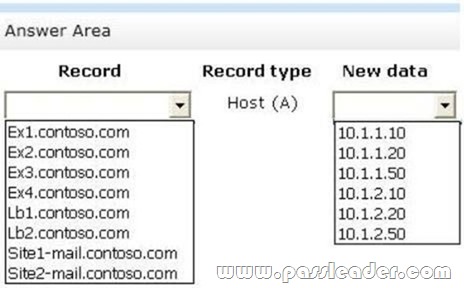
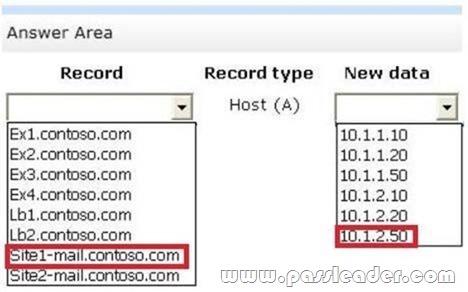
All of the mailbox databases replicate to all of the servers. Users in Site1 connect to sitel-mail.contoso.com to access their mailbox. Users in 5ite2 connect to site2-mail.contoso.com to access their mailbox. All of the users use Microsoft Outlook 2013. You need to identify which DNS modification must be made to fail over the email services from Site1 to Site2. Which DNS modification should you identify? (To answer, select the appropriate record to modify and the new data for the record in the answer area.)
 Answer:
 QUESTION 85
Drag and Drop Question
You have an Exchange Server 2013 organization and a Microsoft Lync Server 2013 infrastructure. You plan to implement voice mail for all users. You need to prepare the environment for the planned implementation. Which tool should you run in each environment? (To answer, drag the appropriate tool to the correct environment or environments. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
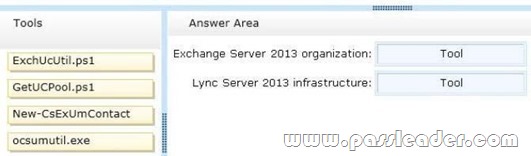 Answer:
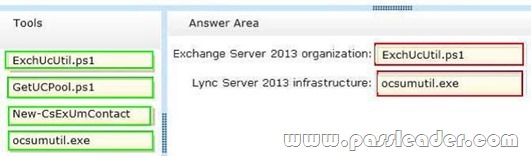 QUESTION 86
Hotspot Question
You have an Exchange Server 2013 organization that has mailbox audit logging enabled for all users. You deploy two third-party applications named App1 and App2. Both applications access a mailbox named Mailbox1. App1 uses a mail-enabled user account named App1_user. App2 uses a mailbox-enabled user account named App2_user. You need to prevent the audit logs from containing entries that relate to App2. Which command should you run? (To answer, select the appropriate options in the answer area.)
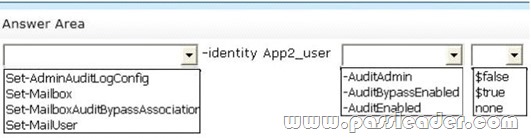 Answer:
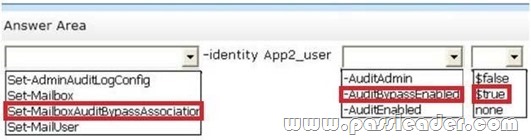 QUESTION 87
You have an Exchange Server 2013 organization that has Unified Messaging (UM) enabled for all mailboxes. The organization is configured to use an IP gateway to connect to a legacy PBX. An administrator recently performed some configuration changes. After the changes, users report that their voice mail is no longer being delivered to their Exchange Server mailbox. The users do not report any other problem. You need to identify which configuration change causes the issue. Which cmdlet should you run? A. Test-UMConnectivity
B. Test-CsExUMConnectivity
C. Test-ExchangeUMCallFlow
D. Test-CsExUMVoiceMail Answer: A QUESTION 88
You have an Exchange Server organization. The organization contains servers that have either Exchange Server 2010 or Exchange Server 2013 installed. You hire a new helpdesk technician named helpdesk1. Helpdesk1 is a member of the Recipient Management management role group. You discover that helpdesk1 created nine new mailbox-enabled users by using the New-Mailbox command. You need to identify which management role provides helpdesk1 with the permissions to create new mailbox-enabled users. Which cmdlets should you run? A. Get-ManagementRoleEntry and Get-ManagementRoleAssignment
B. Get-RolegroupMember and Get-ManagementRoleAssignment
C. Get-ManagementRoleEntry and Get-RoleGroup
D. Get-Rolegroup and Get-RoleGroupMember Answer: A QUESTION 89
Drag and Drop Question
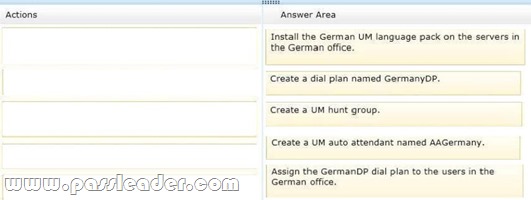
You company has offices in the United States and Germany. Each office contains several servers that have Exchange Server 2013 installed. The Exchange Server organization is configured for Unified Messaging (UM). Each office contains an IP-PBX device. You need to ensure that callers to the German office can navigate the voice mail system menu in German. In which sequence should you perform the actions? (To answer, move all of the actions from the list of actions to the answer area and arrange them in the correct order.)
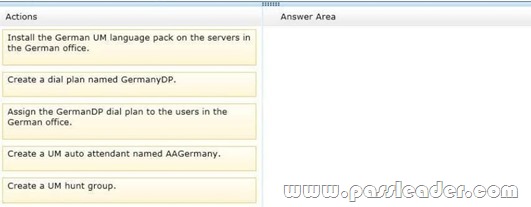 Answer:
 Case Study 5: Fabrikam, Inc (QUESTION 90 ~ QUESTION 98)
Overview General
Overview
Fabrikam, Inc., is a plastics manufacturer. Fabrikam has an Exchange Server organization that contains only servers that have Exchange Server 2013 installed.
Physical Locations
Fabrikam has two main offices. The main offices are located in Tampa and Charlotte. The company has 8,000 users in each office.
Existing Environment
Active Directory Environment
Fabrikam has an Active Directory forest that contains one domain named fabrikam.com. Each office is configured as an Active Directory site. The network contains four subnets. The subnets are configured as shown in the following table.

All of the traffic from Subnet1 is routable to Subnet3. All of the traffic from Subnet2 is routable to Subnet4. All client computers are on Subnet1 and Subnet3 only. Subnet 192.168.1.0/24 and subnet 192.168.10.0/24 are assigned as the MAPI network. The network contains four domain controllers. The domain controllers are configured as shown in the following table.
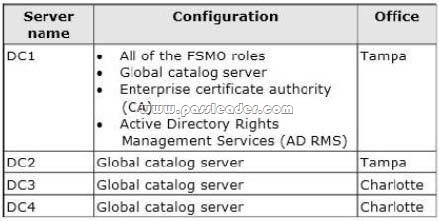
Network Infrastructure
The network contains the following components:
- Two 10-gigabits per second WAN links that connect the Tampa office and the Charlotte office. The links have a latency of less than 15 ms.
- One IP-PBX that is located in the Tampa office. The IP-PBX can use only unencrypted communications.
- An Internet connection in the Tampa office and an Internet connection the Charlotte office.
Exchange Environment
The network contains six servers that have Exchange Server 2013 installed. The servers are configured as shown in the following table.
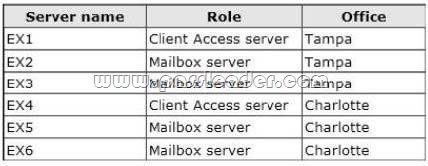
The Exchange Server environment has the following configurations:
- Two data loss prevention (DLP) policies named DLP_Finance and DLP_PII. DLP_Finance is based on a template named Financial Data - U.S. DLP_PII is based on a template named PII (U.S.).
- A mailbox database named UM that hosts only Unified Messaging (UM)-enabled mailboxes and is replicated between the Mailbox servers in the Tampa office only. -A database availability group (DAG) named DAG1 that contains EX2, EX3, EX5, and EX6. DAG1 is configured to use DHCP to obtain an IP address.
- A Send connector named Tampa SMTP that uses SMTP1 as a smart host. The cost of the Tampa SMTP connector is 10.
- Mailbox servers in the Tampa office that provide outbound SMTP services to the Internet.
- A UM dial plan named UMl.
- An SMTP relay device named SMTP2 in the Charlotte office.
- An SMTP relay device named SMTP1 in the Tampa office.
- No client access services are published to the Internet.
Requirements
Exchange Server Issues
- The current Exchange Server environment has the following issues:
- Due to power failures, the Exchange servers unexpectedly fail, causing databases to fail over. During the database failovers, the preferred database is not activated, causing an unexpected distribution of active databases.
- An IRM template named No Print or Screenshot is deployed, but the template fails to prevent users from taking screenshots of email messages.
Technical Requirements
You identify the following technical requirements:
- Assign a static IP address to DAG1.
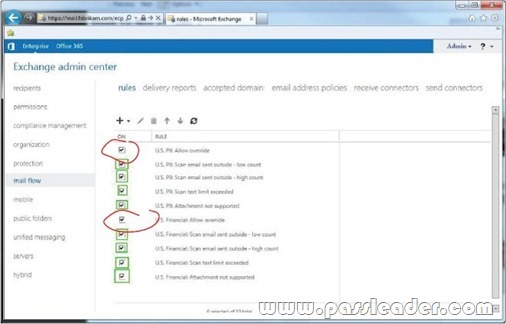
- Block all personally identifiable information (PII) data and financial data without exception.
- Prevent the forwarding of email messages sent by users who have a value of Legal in their Department field.
- Ensure that the members of a group named HR1 can search all of the mailboxes for sensitive email content.
- Use Information Rights Management (IRM) to protect all of the voice mails left for the telephone number of the human resource (HR) department.
- Implement an archiving policy that moves all of the email messages from the mailbox folders to an Archive mailbox after 30 days and permanently deletes all of the email messages after 365 days. QUESTION 90
Hotspot Question
You need to configure transport rules to meet the technical requirements for the PII data and the financial data. How should you configure the rules? To answer, disable the appropriate rule or rules in the answer area.
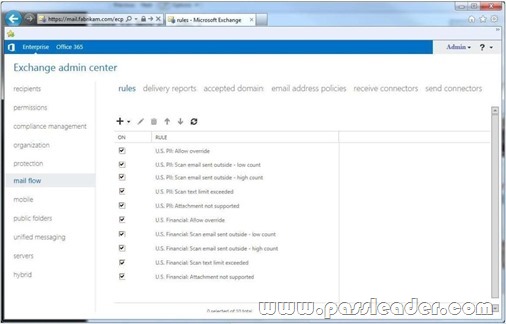 Answer:
 Download Free 70-342 PDF Dumps From Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpfnExREVzWWtnTGZYZDhiVm1ESjV2dkgwU09EOExRMloxUE95aUdnWC1lUU0 (Explanation For Every Question Is Available!) PassLeader 70-342 VCE Dumps Screenshots: 
Download New 70-342 VCE Dumps From PassLeader: http://www.passleader.com/70-342.html (New Questions Are 100% Available and Wrong Answers Have Been Corrected!!!)
|








































